A Note from the CTO
We’ve been hard at work on all things BlindSPOT and wanted to share just a few of the highlights with you.
As you’ll see in this update, the BlindSPOT team continues to build out new features and functionality that make conducting Breach and Attack Simulation style testing easier, while reducing the time and friction to get to the results. A lot of the features and changes you’ll notice when using the platform came directly from the feedback of our customers, so thank you, and keep it coming.
-Ben Finke
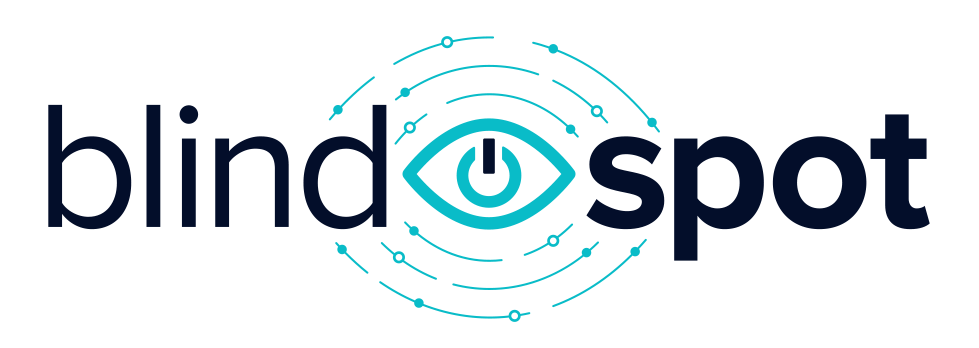
Simulation Library Updates
Our Simulation Library has been completely redesigned to make it easier to find the simulations you need to test your defenses and train your team. The new look and feel makes it easy to find and start campaigns, and you can even create your own favorites list for suture workshops.
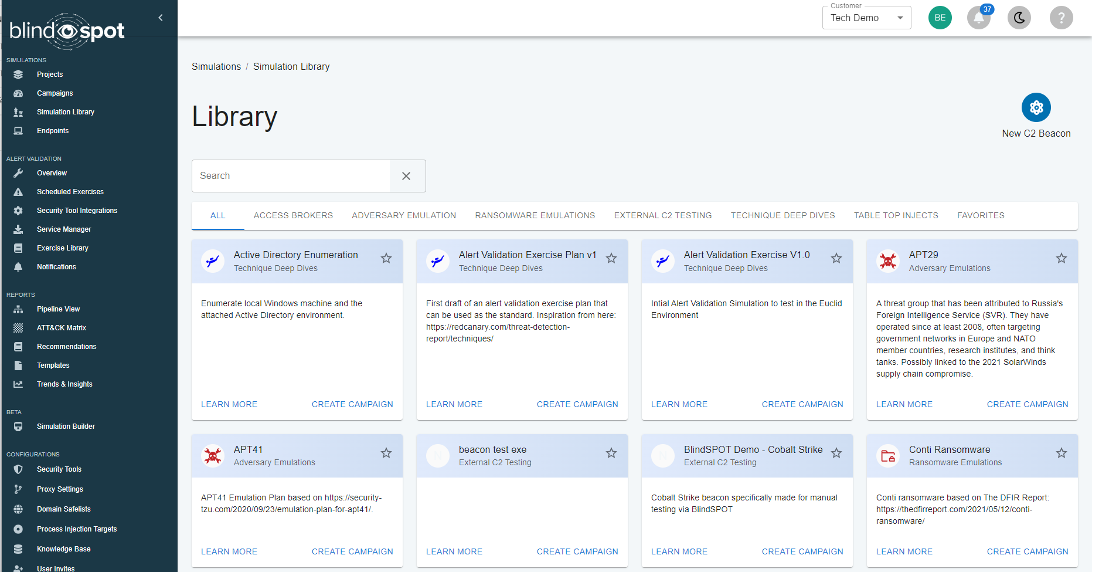
Simulation Builder Updates
Our beta release of the Simulation Builder is getting better every day, thanks to your feedback (please, keep it coming)!
The new interface makes it easy to add new steps to your simulations and to create or modify existing steps.
Here are some of the key improvements:
- Easy step placement: You can now easily pick where you want to add new steps in your simulation. Simply click on the “+” button at the desired location, and a new step will be added.
- Cleaner and simpler step creation: Creating and modifying steps is now easier and faster. The new interface is more organized and user-friendly, so you can focus on your simulation instead of the tools.
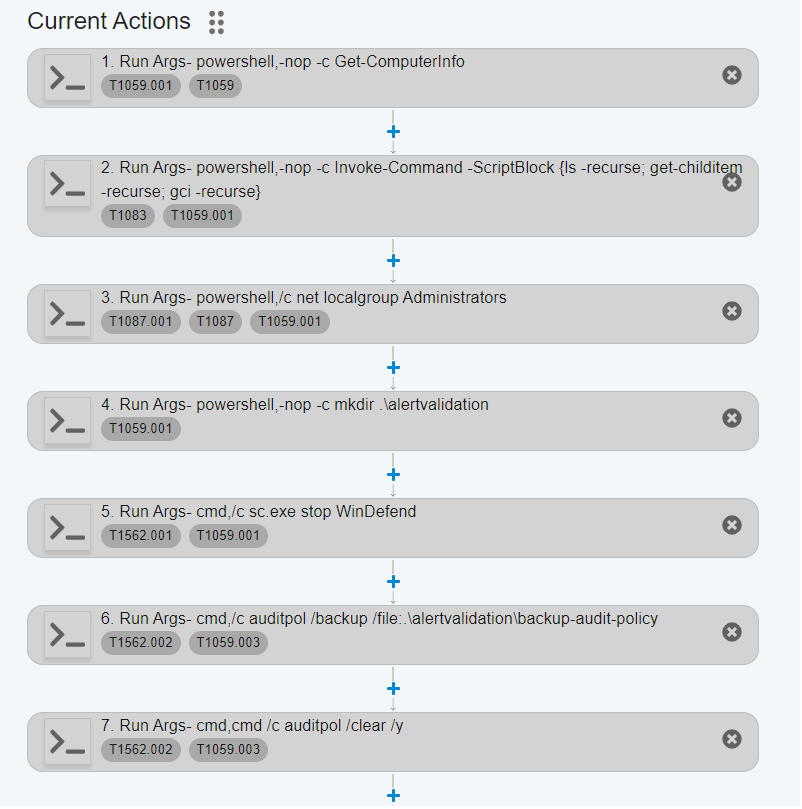

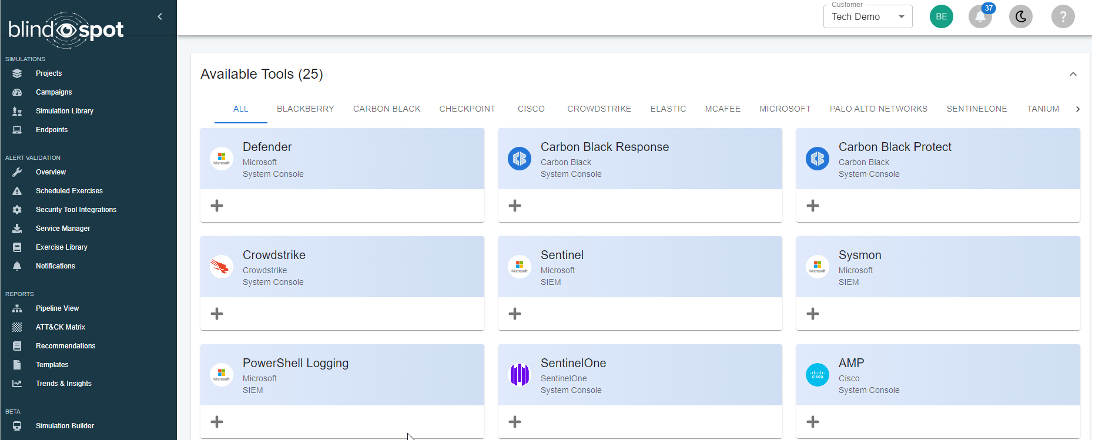
New Security Tools Catalog
We’ve updated our security tools area to give you a better view of your current tools and to suggest new tools that you may want to consider.
Here are the key changes:
- Improved view: Your current security tools are now displayed in a more organized and easy-to-read format.
- Suggested tools: We’ve prepopulated a list of security tools that you may want to include, based on your current setup and industry best practices.
If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
Originally written for Jacksonville Business Journal by James Cannon
For more than 25 years, the Jacksonville Business Journal has identified the fastest growing companies on the First Coast.
This list has tracked companies that boomed during the good times, that grew even when the economy shrank, that stand as an example of what ingenuity, hard work and creativity can lead to.
This year’s list of honorees are drawn from a range of industries, including real estate, transportation, technology and manufacturing.
As a group, the Fast 50 honorees saw their revenue grow by more than $2 billion collectively over the past three years.
OnDefend made a significant leap up the rankings this year, taking home the coveted 14th spot, a one-position improvement from last year.
Founded in 2016 by Co-Founders Chris Freedman & Ben Finke, OnDefend started as a service company but has quickly become a leader in the SaaS space with their attack simulation tool, BlindSPOT.
In this interview with the Jacksonville Business Journal, Freedman explains what this milestone means to the company.
What led you to the point of starting or buying into a company? “I wanted to change the world in a positive way and watching companies being devastated by cyber criminals inspired Ben and myself to launch OnDefend so that we could help companies around the world secure their future.”
What has been the biggest challenge you’ve overcome as you’ve grown? Covid was not easy for any company to endure, but being followed by an economic downturn has made growth at the scale I would prefer extremely difficult.
What’s been the ‘secret sauce’ that has helped propel your growth? Identifying niche markets in our industry and executing effectively within them.
What have you done to keep your company culture strong as you grow? Our core values which are Passion, Creativity, Humility, Motivation, Integrity and Authenticity.
What advice did you receive earlier in your career that has stuck with you as you lead your company? Know what your customers want most and what your company does best. Focus on where those two meet.
What advice would you have for those who are looking to lead a fast-growing company? Find a strong niche through market research and build a team of smart people to execute your vision and mission in a sustainable way.
What challenges or opportunities do you see on the horizon and how are you preparing for them? Spinning out a SaaS business from a service-based organization and scaling both independently during an economic downturn.
Link to original article: 2023 Class of Fast 50: Ondefend
It is about to be busy season for cyber security providers around the world. From non-stop conferences and awards to new vulnerabilities and cybersecurity awareness month. Let’s get started.
OnDefend Insights
It’s likely one of the most common questions our in-house red team gets asked, “how did you become an ethical hacker?” In today’s job market it seems as if entry-level cybersecurity jobs are non-existent, but how do you become a seasoned professional without the experience? OnDefend senior tradecraft engineer Ryan Tucker created a how-to guide on becoming a hacker, and his advice to others on growing their careers.
Becoming an Ethical Hacker > OnDefend
——
A recent report revealed less than a quarter of CISO’s are participating in business strategy and decision-making processes within their organization (I know what you’re already thinking, that doesn’t shock you at all.) Here’s what you might not have expected, the report showed cybersecurity budgets are increasing but there was a catch to receiving that budget. You can read the full report here.
Cybersecurity budgets are increasing, yet CISO’s are still not invited to the boardroom. > OnDefend
——
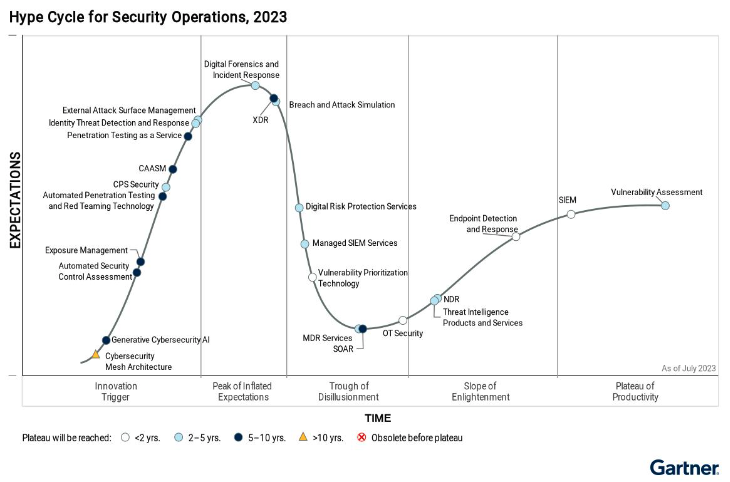
Breach & Attack Simulation or BAS technology is at peak interest according to Gartner’s 2023 security operations hype cycle. BAS technology provides automated and consistent assessment of an enterprise’s threat vectors. Frequent automated BAS assessments also enable organizations to detect gaps in their security posture due to configuration errors or reevaluate priorities of upcoming security investments.
What makes OnDefend‘s BAS tool BlindSPOT stand out from the competition?
⭐️ Can be offered as a one-time attack simulation or a fully managed service
⭐️ Competitively priced compared to other BAS products
⭐️ Allows for customized payloads, C2 integrations, and stakeholder reporting
Visualize the power of removing these “blind spots” here.
Visualizing the Power of BlindSPOT > OnDefend
Cybersecurity Roundup: Top Stories from the Digital Frontlines
Microsoft says Storm-0558 Chinese hackers stole a signing key used to breach government email accounts from a Windows crash dump after compromising a Microsoft engineer’s corporate account.
Hackers stole Microsoft signing key from Windows crash dump (bleepingcomputer.com)
—
CISA confirms the addition of Peiter ‘Mudge’ Zatko to its roster of prominent voices preaching the gospel of security-by-design and secure-by-default development principles. According to CISA director Jen Easterly Mduge was brought on to “shape a culture of security by design that is foundational to every security team, every C-suite, and every board room in the country.”
CISA Hires ‘Mudge’ to Work on Security-by-Design Principles – SecurityWeek
—
Leading cybersecurity agencies from the UK, US, Australia, Canada, and New Zealand have discovered that the Sandworm cyber actor used a new mobile malware, “Infamous Chisel,” to target Android devices used by the Ukrainian military. They have previously connected Sandworm to Russia’s GRU Main Centre for Special Technologies (GTsST), indicating state-sponsored involvement in these cyberattacks.
Infamous Chisel Malware Analysis Report | CISA
—
The patch didn’t work. The FBI warns that Barracuda Email Gateways continue to be vulnerable despite attempts at a recent solution to the zero-day bug. According to the FBI, the fixes are considered “ineffective” and that it “continues to observe active intrusions and considers all affected Barracuda ESG appliances to be compromised and vulnerable to this exploit.”
Urgent FBI Warning: Barracuda Email Gateways Vulnerable Despite Recent Patches (thehackernews.com)
OnDefend in the News
“Hard work, consistency, curiosity, a positive attitude, and a desire to grow. All qualities that are needed to ensure an organizations growth.” OnDefend Co-Founder/CTO Ben Finke reflects on his leadership after being named one of the 2023 tech leaders of the year. If you’ve ever met Ben, you recognize his leadership combined with his technological savvy is unmatched. Check out his full interview.
2023 Tech Leaders: Ben Finke of OnDefend > OnDefend
BlindSPOT

We have some very exciting news on the BlindSPOT front that we will be announcing next month, from simulation library updates to a new security tools catalog. In fact, there is such a steady flow of updates, we figured the BlindSPOT section should have a page of its own. Consider this your foreshadowing to the big announcement next month. – Ben, OnDefend CTO
Anybody else feel like we just scratched the surface? That’s because we did. Stay tuned for this bi-monthly newsletter, for all of OnDefend’s latest and greatest.
If you want to stay in the loop about what’s happening at OnDefend, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
Originally written for Jacksonville Business Journal by James Cannon
JACKSONVILLE, Fla. –For the past five years, the Jacksonville Business Journal has honored some of the men and women whose technology leadership has helped local organizations grow, deal with challenges and shape the future.
We’re glad to have this opportunity to spotlight these leaders and their accomplishments, and we look forward to seeing the impact they and their organizations have on the community in the future.
Name: Ben Finke
Company: OnDefend
Title: Co-Founder and CTO
How has your leadership helped your organization grow? Hard work, consistency, curiosity, a positive attitude, and a desire to grow. All qualities that are needed to ensure an organizations growth. I will start by saying, the product and services our company offers has such an important need in every sector of business. A good product, like BlindSPOT will naturally lead to business growth but it was the above attributes that led to this product being built successfully and my continued desire to grow to teach others about it.
As the BlindSPOT product has gained new capabilities and we’ve expanded the content available we’ve added new customers, allowing us to reinvest that into more development and content capacity. Over the years our company has grown in employee count, financial revenue, and brand awareness. My willingness to continue to teach others and continually push the envelope has led us to where we are today and I know will only push is further to come.
What is your greatest career accomplishment? I’ve been very fortunate to work on several amazing projects and with some amazing people over my career, but in 2021 we were asked to help secure the upcoming FIFA World Cup in Qatar. In cybersecurity you’re not always allowed to mention the companies or organizations you’re working with for security reasons. This was one of those projects that for well over a year, my team worked tirelessly to make this event a success. It was one of those projects that if we did not do our job correctly, one of the most famous sporting events in the world would be in trouble. The OnDefend name was at stake, and we knew we had to get it right. In cybersecurity, no news is good news. The fact, that a cyber-attack on a global stage didn’t hit the news means we did our job correctly. To know that our company has reached a level to be selected for that kind of project and pull it off successfully is something I could have only dreamed of when I started my career.
OnDefend Media Contact: Lauren Verno, Lauren.verno@ondefend.com
Summer is wrapping up and “out of office” replies are slowly disappearing. Here’s an update on some of what OnDefend was up to while you we’re away.
Three CISO Problems Solved: Demonstrating Your Security Programs Value to Leadership
It was an exciting conversation between former CISO/cybersecurity executive Todd Salmon and OnDefend CEO Chris Freedman, as they discussed how to prepare for some of the most common questions security leaders face today. Including, how to prepare for industry specific threat actors, validating your security controls effectiveness, and responding to a real-world breach. Missed it? Check it out here 👇🏻
Three CISO Problems Solved: Demonstrating Your Security Programs Value to Leadership > OnDefend
OnDefend Insights
Pentests are one of the most requested services we get at OnDefend. The purpose of these tests are not to cause harm, but to understand the potential weaknesses in the system. COO Billy Steeghs created this one-stop shop for pentesting in “understanding network penetration testing: it’s significance, requirement, and compliance.
Understanding Network Penetration Testing: Its Significance, Requirement, and Compliance > OnDefend
——
We are lucky to have some of the most qualified and highly skilled red teamers at OnDefend. One of their jobs? Threat-Hunting. Our director of offensive security Joe Brinkley aka The Blind Hacker breaks down the importance of threat-hunting, the process, and what characteristics every threat-hunter should have.
An Introduction to Threat-Hunting > OnDefend
OnDefend In The News
OnDefend has once again been named one of the fastest-growing companies on the first coast! 🎉 For more than 25 years, the Jacksonville Business Journal has identified the fastest-growing companies on the First Coast.
“ This list has tracked companies that boomed during the good times, that grew even when the economy shrank, that stand as an example of what ingenuity, hard work and creativity can lead to.” – Jacksonville Business Journal
—
CTO Ben Finke answers the age-old question, “Can cybersecurity be solved” to Forbes. In this article, Ben takes a historian’s view on how the security arc closed in a hypothetical future to see how we might approach this problem in our present. *Hint, “uncovering a company’s security control blind spots” is just one component.
Can Cybersecurity Be ‘Solved’? Examining A Hypothetical Future (forbes.com)
—
Back to the basics. ONE click caused a small business owner to lose social media accounts to internet hackers. OnDefend VP of Communications Lauren Verno shares insights with her former news station. An excellent share for your non-technical friends, co-workers, and family!
One click caused small business owners to lose Instagram accounts to scammer (news4jax.com)
—
Better Together
BDO Digital, OnDefend, and Cyber Defense Magazine team up to introduce “How to Build a Resilient Cybersecurity Program.” In this webinar the three security leaders discussed everything from building a security stack that’s the right size for your company, how to compete in today’s market, and how to focus on the risks that are most likely to impact your organizations.
—
Going deep with DeepSeas’ Josh Nicholson for an episode of Cyber Security America. In this conversation between OnDefend CEO and SafeGuard Cyber CEO Chris Lehman, the discussion revolves around the “top five crucial aspects that the CISO communication should be aware of.”
BlindSPOT

Introducing the Custom Simulation Builder in Beta
We are thrilled to announce that the Blindspot team has opened the Simulation Builder into Beta, empowering you to create your very own simulations. Now, you have the freedom to design and test simulations during the draft phase. By simply having an agent running, you can instantly observe and evaluate the results in real-time within your window. Whether starting from scratch or using an existing simulation as a foundation, the possibilities are endless.
Simulation Actions Bulk Update
To streamline the scoring process, we have introduced the ability to perform bulk updates on simulation actions. Now, you can conveniently assign a status (No Evidence, Logged, Alerted, Blocked) and allocate a security tool to each item. This enhancement ensures faster and more efficient scoring, especially for large campaigns.
Blindspot’s Expanded Capability: Implanting Cobalt Strike Beacons
As part of our commitment to providing top-notch features, Blindspot now enables you to send Cobalt Strike beacons from within the platform. These beacons can be activated by our agents on your endpoint. Subsequently, from your Cobalt Strike server, you can execute commands seamlessly. Once you’ve completed your operations, the Cobalt Strike logs can be converted into a Blindspot Campaign, facilitating seamless reporting.
Anybody else feel like we just scratched the surface? That’s because we did. Stay tuned for this bi-monthly newsletter, for all of OnDefend’s latest and greatest.
If you want to stay in the loop about what’s happening at OnDefend, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
We get this question a lot – how does someone become an ethical hacker? Let’s start by saying that almost everyone has a different story but here’s our advice on some good places to start.
First, cybersecurity in general is a field that rewards actual hands-on experience as much as anything else. You’ll need to bring along your curiosity and your determination (the path to success is paved with failures you’ll learn from) and relax in the realization that you are going to be constantly learning.
Two major paths exist:
- Formal education and training
- Hands-on challenges.
These two paths play an important role in how you will capitalize on the knowledge and expertise you are going to gain.
Most formalized training paths involve certifications. There is a wide spectrum of cybersecurity certifications. Some are well-established ones that have been around for a longer amount of time, and they may have differing levels of respect between technical practitioners and hiring managers. New certification and training programs pop up frequently, and while they may not be as well-known they frequently offer more contemporary and practical content. Your own selected path is likely to be managing a balance between the value of a recognized certifications and the benefits of up-to-date, actionable knowledge.
Some certifications can provide a significant advantage during job applications. They act as credentials that can help an applicant stand out to hiring managers and secure interviews, making them a valuable addition to a resume. In fact, often these certifications are used to filter resumes before a hiring manager even sees them.
It’s a cliché, but like many cliches there’s truth to it – you can pass lots of certification tests and still not be able to do the actual work. There’s no better way to learn how to do the actual work then to do the actual work! One of the best ways to begin building your skills is to participate in Capture the Flag (CTF) competitions and experiences. These CTFs are essentially puzzles requiring you to learn and apply specific techniques in order to achieve the outcome. Most CTFs also include a training guide on how to complete the challenges (once the competition is over of course) so that you can see how the creators thought the challenges could be solved.
One of the challenges in the cybersecurity industry is the often-heard phrase, “you need experience to get experience”. Companies prefer to hire those with proven experience, creating a challenging situation for newcomers. By earning certifications and participating in practical exercises like CTFs, one can gain a semblance of ‘real world’ experience, making them more attractive to potential employers.
Here is a list of certification and training:
Non-certificate training/Capture the flags
- Hackthebox Academy– Hackthebox is a fantastic CTF platform which came out with an academy section that walks new professionals through the modern tools and techniques used in vulnerable labs and networks. If you are already familiar with the tools and techniques of the trade, there are other learning paths, Pro Labs or regular HackTheBox CTFs to test your skills.
- Tryhackme– Tryhackme is another CTF like platform that has content divided into much smaller chunks for easier consumption. They have a number of different “learning paths” to tailor the skills and content towards a specific direction.
- OWASP Juice Shop – An intentionally vulnerable web application that let’s you learn and hack a webapp written in Node.js
Certifications
- CompTIA Net+– Intro to all things networking
- Sec+– Intro to all thing security
- CEH– Intro to the field of ethical hacking with a theoretical tighter focus on attacking systems
- eJPT– One of the first “hands on” certs recommended a new person. It starts to focus on the Pentest side and how engagements are run
- PTP– The more “advanced” version of the eJPT, this course work broadens the knowledge from the eJPT in hands on environment
- OSCP/PWK/PEN-200– It goes by a handful of names now, but the OSCP certification is usually the hiring baseline for pentester/offsec engineer roles
These are just a fraction of the training and certifications available in the cybersecurity space but are the ones usually in reach for people just getting started.
About OnDefend:
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world threats. From ensuring compliance with industry standards to building out mature security programs our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, please visit OnDefend.com.
A new report reveals less than a quarter of CISO’s are participating in business strategy and decision-making processes.
Let’s acknowledge the elephant in the room: cybersecurity is still not a main priority for most organizations. It’s not that companies don’t care, many times investing in cybersecurity can seem out of reach, overwhelming, or an “IT problem”, but in today’s current landscape these excuses are no longer an option.
A recent survey of 150 CISO’s by BSS revealed less than a quarter (22%) of CISO’s are actively participating in business strategy and the decision-making processes. Even more staggering, only 1 in 10 (9%) of CISO’s said information security is always in the top three priorities on the boardroom’s meeting agenda.
Cybercrime is a TRILLION-dollar issue, $8 trillion to be exact and that number is expected to grow to $10.5 trillion by 2025 according to cybersecurity ventures. To give you some perspective of how much money that is, combine the worth of Apple, Microsoft, and Amazon… and then double it.
We understand cybersecurity can seem like a huge undertaking and there aren’t any tangible results. It’s a lot like investing in car insurance. You don’t need it until you’re in an accident. That’s how many companies approach cybersecurity, they don’t invest until there’s been a breach but by then the damage is done.
Now, it’s not all doom and gloom. The survey did reveal that investment in cybersecurity is slightly moving in the right direction. 61% of the CISO’s surveyed noted they received a significant increase in funding, averaging between 10-30% more. However, over half of respondents said “they we’re expected to spend their budget on cyber security issues hitting the news headlines, rather than where it’s really needed. “
However, the survey highlighted 78% of the CISO group said high-profile security incidents we’re the reason behind receiving more budget.
I’m not a big fan of scare tactics. I believe it’s important to understand the problem (which can have hints of scary) and then offer solutions.
That’s one of the reasons we saw a use case for BlindSPOT, OnDefend’s proprietary breach & attack simulation tool. It changes the mindset of a company that is historically reactive to cybersecurity incidents and makes them proactive. BlindSPOT consistently tests and tunes an organizations security control throughout the year. That way if an attacker we’re to strike, you would know your companies ready. It’s a lot like prepping for a hurricane. You can’t stop mother nature from striking but you can be prepared with flashlights, water, and rain boots for when it happens.
So, where am I going with all of this? The need to give cybersecurity a seat at the table. Once leadership changes their mind from not if we’re attacked but when, then we can all start doing the real job of protecting against the bad guys. In the end, we’re all after the same goal, right?
Security leaders deserve to be equipped with answers when their C-suite or Board of Directors ask questions.
How is that traditionally done? Investing in best-in-class security tools, hiring seasoned team members, and implementing policies to harden their environment from threats. All necessary, but you need reassurance it will all work when that inevitable attack comes.
Cybersecurity executive/former CISO Todd Salmon and OnDefend CEO/co-founder Chris Freedman identifies and solve three defense readiness questions every security leader should be able to answer, in a way that even the most non-technical stakeholders can understand, visualize, and value:
- Are we prepared for threats targeting our industry?
- We’ll reveal why organizations are unknowingly not preparing for these specific threats and how to prove your organizations readiness within 24 hours of leadership asking.
- Are the security controls we invest in working and worth it?
- Learn why security tools have consistent blind spots and how to prove their effectiveness all year long.
- Can we effectively respond to a real-world cyber breach?
- Bring your tabletop exercises to the 21st century by safely simulating real-world cyber attacks to prove your organization is resilient.
Speakers Information:
Todd Salmon, Former CISO/Cybersecurity Executive
Todd Salmon is a tenured cybersecurity executive with a multitude of experience leading professional services organizations focused on information security and technology, spanning all the vertical markets. Todd’s prior experience includes having served as the Chief Information Security Officer for one of the largest global technology distributors in the world. In this role he had worldwide responsibility for the organization’s entire information security program to include Security Engineering & Operations, Policy & Procedure, Compliance and Physical Security.
Chris Freedman, OnDefend Co-Founder/CEO
Chris is a highly accomplished business leader with a diverse background in diplomacy, business, and philanthropy. Chris began his career serving as a diplomat with the Atlantic Treaty Association and founding a regional real-estate development firm. He continued his career by founding and managing various corporations in the U.S. including, MyBenefitsLab, a national online provider of diagnostic testing with the nation’s largest laboratories and national physician’s network. In 2016, Chris Co-Founded OnDefend, an international cyber security firm, where he currently serves as the CEO. Civically, Chris has also served several charitable organizations, including Best Buddies Jacksonville and the American Red Cross of Northeast Florida. Chris graduated with the highest honors from the University of Florida.
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world threats. From ensuring compliance with industry standards to building out mature security programs our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, please visit OnDefend.com.
Threat-hunting is a proactive method of identifying and mitigating potential cyber threats that may have circumvented traditional security measures. Its objective is to discover and resolve security issues before they pose any problems to an organization.
Why is Threat-Hunting Important?
Threat-hunting is an essential tool for identifying and mitigating potential security threats before they cause damage. It also helps improve an organization’s overall security posture.
Characteristics of an Effective Threat-Hunter
A good threat-hunter should possess the following characteristics:
- Familiarity with the organization’s infrastructure and security processes
- Strong analytical skills
- Attention to detail
- Persistence and patience
- Creativity
- Knowledge of threat intelligence and the threat landscape
Threat-Hunting Process:
Preparation
- Define what we are looking for
- Identify what we need to protect
- Identify potential threats
- Develop a hypothesis
Detection
- Use different tools to detect threats
- Analyze logs and other data sources
- Look for anything suspicious
Analysis
- Review the data to determine what kind of threat being dealt with
- Identify the source of the threat
- Determine the extent of the damage
Response
- Deal with the threat effectively
- Implement measures to prevent similar threats in the future
- Share findings with appropriate parties
Tools & Techniques for Threat-Hunting:
- Endpoint detection and response (EDR) tools
- Security information and event management (SIEM) systems
- Network traffic analysis tools
- Threat intelligence feeds
Challenges in Threat-Hunting:
- Lack of personnel with the right skills
- Complex and diverse IT environments
- Difficulty in observing everything that is going on.
- Large amounts of data to sift through.
- Lack of actionable intelligence
Benefits of Threat-Hunting:
- Faster detection and response to threats
- Improved security posture
- Reduced likelihood of data breaches
- Greater awareness of the threat landscape
- Enhanced team incident response capabilities
How BlindSPOT Can Help
BlindSPOT is OnDefend’s proprietary breach and adversarial simulation tool that can help teams improve their cybersecurity defenses. One of its greatest strengths is its ability to facilitate threat hunting, simulate malware, test EDR/AV, tune SIEM, and other security tools.
By using BlindSPOT, teams can gain a better understanding of their organization’s security posture, identify potential vulnerabilities, and develop effective countermeasures. BlindSPOT provides a safe and controlled environment for simulating real-world cyber threats, allowing teams to practice and refine their incident response capabilities.
Compound Capabilities
In addition to its simulation capabilities, BlindSPOT also provides detailed reports and analytics that can aid in identifying security weaknesses and measuring the effectiveness of security controls. This can help organizations prioritize their security efforts and allocate resources more effectively. BlindSPOT can also help organizations comply with industry regulations and standards. By simulating real-world cyber threats, organizations can identify potential weaknesses in their security infrastructure and address them proactively. This can help organizations meet compliance requirements and avoid costly fines or legal actions.
Other Benefits of BlindSPOT
Another benefit of using BlindSPOT is its ability to provide a collaborative learning environment. Teams can work together to identify and respond to simulated cyber threats, sharing knowledge and best practices along the way. This can help foster a culture of security within the organization and improve overall cybersecurity awareness.
With BlindSPOT, teams can also gain insights into the latest cyber threats and attack techniques. BlindSPOT’s threat library is constantly updated with the latest threat intelligence, ensuring that teams are prepared to defend against the most current and sophisticated attacks.
Why BlindSPOT
BlindSPOT is a tool that organizations can use to identify and address security detection weaknesses. It offers a range of features, including simulation, reporting, compliance, collaboration, and threat intelligence. With BlindSPOT, organizations can confidently defend against cyber threats and protect critical assets. Overall, BlindSPOT is an invaluable tool for improving cybersecurity defenses. Teams can use its powerful simulation and detailed reporting capabilities to develop effective cybersecurity strategies and safeguard their organizations.
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world threats. From ensuring compliance with industry standards to building out mature security programs our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, please visit OnDefend.com.
With hackers constantly on the lookout for vulnerable targets, it’s important for organizations to stay one step ahead. Working in cybersecurity over the last two decades, there we can all agree pentesting continues to be one of the most powerful tools in any companies’ arsenal. A tried and true for a reason. Network Penetration Testing, commonly known as “PenTesting” is a bit like a fire drill for cyber-attacks, allowing organizations to identify and fix weaknesses before real hackers find them. But what exactly is Network Penetration Testing? Who needs it, what rules mandate its use, and why is it so important? Let’s dive in to answer these questions.
What is Network Penetration Testing?
Network Penetration Testing is a process by which trained and certified ethical hackers mimic malicious attacks on a network to identify vulnerabilities before actual hackers can exploit them. This testing process involves attacking the network’s infrastructure – servers, network devices, and system endpoints – to identify weaknesses in its defenses.
The purpose is not to cause harm, but to understand the potential weaknesses in the system. It’s about uncovering areas of improvement and ensuring that the appropriate measures are taken to secure the system.
Example of a Comprehensive Pen Test
A comprehensive penetration test, like those conducted by OnDefend, involves a systematic and thorough evaluation of your organization’s network security. Here’s a typical sequence of steps in such a test:
- Planning and Scoping: The first step is to define the scope and goals of the test, including the systems to be addressed and the testing methods to be used. This stage also involves gathering intelligence to understand how the targeted systems work and what potential weaknesses might exist.
- Reconnaissance: This phase involves deep-dive information gathering about the target. This might include identifying IP addresses, domain details, network topology and, in some cases, gathering information from public sources (also known as OSINT or Open-Source Intelligence) about the company or its employees.
- Vulnerability Assessment: Using manual or automated tools, the testing team identifies potential points of exploit on the target systems. This might include using software to scan for known vulnerabilities, such as open ports or insecure software configurations.
- Exploitation: In this stage, the pen tester attempts to exploit the vulnerabilities identified in the previous step. This could mean trying to gain unauthorized access to systems, extracting sensitive data, or performing other activities that real-world attackers might attempt.
- Post-Exploitation: Once access is gained, the focus shifts to what can be done with the exploited system. This might involve identifying and documenting sensitive data, accessing user accounts, or trying to escalate privileges to gain more control over the system or network.
- Reporting: The final step involves compiling a detailed report documenting the vulnerabilities found, the exploitation steps taken, and the sensitive data that could potentially have been exposed. This report also includes recommendations for mitigating the identified vulnerabilities.
Through this comprehensive process, OnDefend can provide your organization with a clear picture of your current security posture, potential vulnerabilities, and the most effective ways to address them. By revealing weak spots, a comprehensive penetration test helps organizations prioritize their security measures and ensure the most robust defense against real-world cyber threats.
Who Needs Network Penetration Testing?
The short answer is – everyone. All businesses, irrespective of their size or industry, should consider regular PenTesting to safeguard their sensitive data. This includes small businesses, corporations, government entities, and non-profit organizations.
For small and medium-sized businesses, PenTesting helps protect customer data and other sensitive information. For large corporations and government entities, it helps safeguard not only the customer and proprietary data but also their reputation and stakeholder trust.
Why is Network Penetration Testing Important?
In an era where cyber-attacks are not only more frequent but also more sophisticated, Network Penetration Testing is more important than ever. Here are some reasons why:
- Identifying Weaknesses: PenTesting helps identify vulnerabilities in your network that can be exploited by hackers. By finding these weaknesses ahead of time, you can address them and fortify your network.
- Regulatory Compliance: Many industries have regulations that require companies to conduct regular penetration tests to ensure that their digital assets are secure. Failure to meet these requirements can result in hefty fines.
- Preventing Financial Loss: Cyber-attacks can result in financial loss due to downtime, data breaches, or loss of customer trust. By identifying vulnerabilities before they can be exploited, you can prevent these losses.
- Protecting Customer Trust: Customers trust you with their sensitive data. A breach could lead to a loss of trust that can have long-term impacts on your business.
What Compliance Requires Network Penetration Testing?
Several industry standards and regulations necessitate regular network penetration testing. These include, but are not limited to:
- Payment Card Industry Data Security Standard (PCI DSS): For any organization handling cardholder information, regular penetration tests are required to remain compliant.
- Health Insurance Portability and Accountability Act (HIPAA): For healthcare providers, penetration testing is recommended to protect patient information and avoid breaches.
- General Data Protection Regulation (GDPR): This European regulation requires companies handling EU citizen data to conduct PenTests to ensure data security.
- Federal Information Security Management Act (FISMA):S. federal agencies or contractors and businesses dealing with federal agencies must adhere to this act, which includes penetration testing.
- ISO 27001: This international standard outlining best practices for an information security management system (ISMS) recommends regular penetration testing.
- System and Organization Controls (SOC) 2: Developed by the American Institute of CPAs (AICPA), SOC 2 is a voluntary compliance standard that applies to service organizations. It focuses on five trust service principles: security, availability, processing integrity, confidentiality, and privacy. Though SOC 2 doesn’t explicitly demand penetration testing, conducting such tests aligns perfectly with its emphasis on security. Regular penetration testing is considered a best practice to validate the effectiveness of security controls and ensure ongoing compliance with SOC 2 requirements.
Adopting Security Frameworks: NIST CSF, ISO 27001, and CIS20
Whether a business must comply with a specific regulatory standard or not, adopting a comprehensive cybersecurity framework is essential for maintaining robust security posture. These frameworks, such as the NIST Cybersecurity Framework (NIST CSF), ISO 27001, and CIS20, provide structured and systematic approaches to managing cybersecurity risks. Let’s delve into these popular security frameworks:
- NIST Cybersecurity Framework (NIST CSF): Developed by the National Institute of Standards and Technology, the NIST CSF is a voluntary framework primarily intended for critical infrastructure organizations to manage and mitigate cybersecurity risk based on existing standards, guidelines, and practices. However, the flexible and scalable nature of the NIST CSF allows its use by a wide range of businesses and organizations.
- ISO 27001: The ISO 27001 standard is an international standard for how to manage information security within an organization. It provides a set of standard procedures for an Information Security Management System (ISMS), detailing how to handle information in a way that ensures its accessibility, confidentiality, and integrity. Regular penetration testing, as recommended by this standard, can help organizations continuously monitor and improve their ISMS.
- CIS Critical Security Controls (CIS20): The Center for Internet Security’s Critical Security Controls (often referred to as CIS20) is a concise, prioritized set of 20 controls that can drastically reduce the risk of cyber threats. These controls are a combination of policies, procedures, hardware, and software that provide a defensive architecture and cover various aspects from data recovery capabilities to penetration tests and red team exercises.
For organizations that don’t have any regulatory compliance requirements, adopting one or more of these security frameworks can provide a comprehensive and proactive approach to cybersecurity. They offer methodologies to identify potential threats, protect against cyber-attacks, detect anomalies, respond to incidents, and recover from them. Furthermore, following these frameworks and implementing regular network penetration testing can greatly enhance an organization’s security stance and resilience against cyber threats.
How OnDefend Can Help with Your Cybersecurity Needs
In an ever-evolving digital landscape, securing your business from cyber threats can seem like an uphill battle. That’s where OnDefend comes into the picture. As a cybersecurity company dedicated to helping organizations fortify their digital infrastructure, we have in-house seasoned red teamers who can help protect your business and maintain the integrity of your digital assets.
Penetration Testing and Breach and Attack Simulation (BAS) Services
OnDefend excels in providing both Penetration Testing and Breach and Attack Simulation (BAS) services. Our certified ethical hackers execute targeted cyberattack simulations to identify your network’s vulnerabilities. Complementing this, our BAS services offer continuous, automated testing that emulates real-world threats, providing real-time insights into your security readiness. These dual services allow OnDefend to offer a comprehensive analysis of your organization’s security status, empowering you to maintain robust defenses against cyber threats.
Comprehensive Security Assessment
Beyond penetration testing, we conduct thorough security assessments to identify potential risks in your cybersecurity framework. By assessing your existing security measures against globally recognized frameworks like NIST CSF, ISO 27001, and CIS20, we provide insights into your security stance and provide recommendations to enhance it.
Cybersecurity Consulting
Our cybersecurity consulting services help you build or improve your cybersecurity program. Whether it’s ensuring compliance with various industry regulations like PCI DSS, HIPAA, GDPR, FISMA, and SOC 2 or designing a security plan from the ground up, OnDefend’s team of security experts is equipped to guide you every step of the way.
Training and Awareness Programs
Recognizing that human error often plays a part in successful cyberattacks, OnDefend offers training and awareness programs. We help educate your team about the latest cyber threats, safe digital practices, and incident response procedures. This empowers your team to become an active part of your cybersecurity defense.
With OnDefend, you’re not just investing in a cybersecurity service; you’re partnering with a team dedicated to protecting your business from cyber threats. Our objective is to help you achieve the peace of mind that comes with knowing your organization’s digital assets are well defended.
Solutions Tailored to You
At OnDefend, we understand that each organization has unique security needs. That’s why we offer tailored solutions to match your specific requirements and industry best practices. Our team works closely with your organization to understand its structure, needs, and potential threats, designing a cybersecurity strategy that is as unique as your business.