Discover Your Security Control Blind Spots
BlindSPOT simulates emerging cyber threats to identify security tool misconfigurations, control changes, alerting delays and other exploitable security control coverage gaps.
Attack Simulations
Safely emulate real-world threat actor tactics and techniques.
Control Validation
Visualize the effectiveness of your technical security controls.
Attack Customization
Build custom attack chains to exercise your tradecraft expertise.
Value Demonstration
Demonstrate your security tool value or investment needs.
How It Works
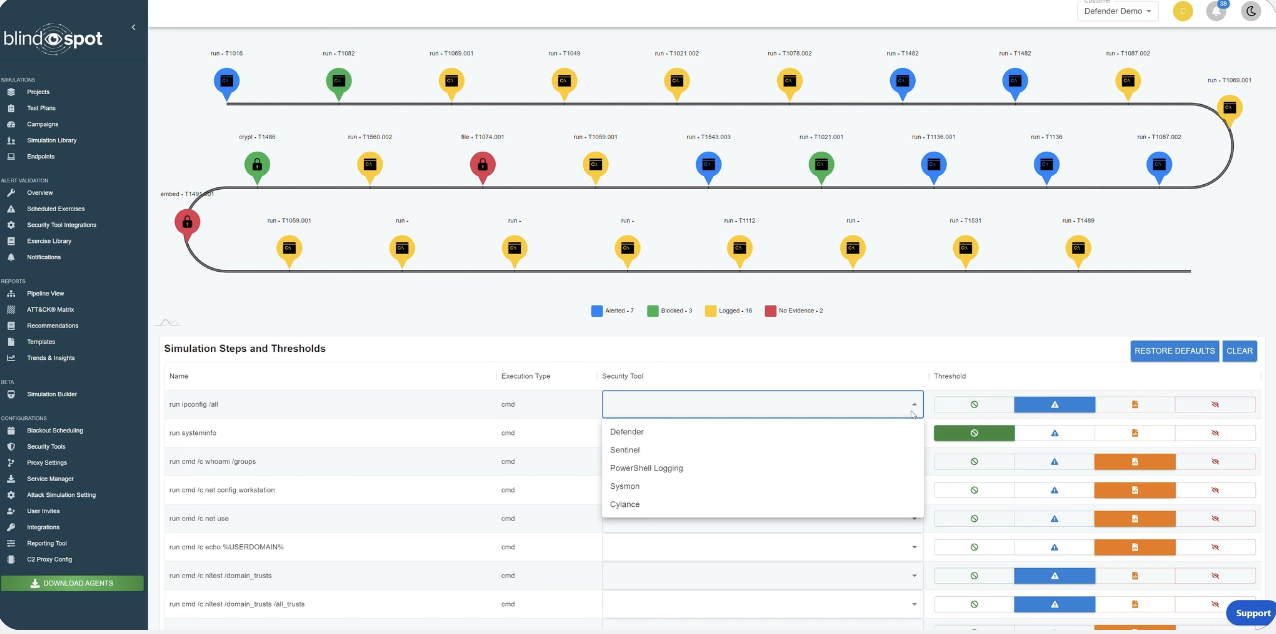
Simulate Attacks
Safely execute attack activities on your production network environments for consistent and realistic practice against adversaries.
All Attacks Welcome
Select from our automated library of ransomware strains, ATP’s and other threats, build your attack chains from scratch using your tradecraft and execute manual attack activity via our C2 Integrations.
Contact UsSecurity Tool Response
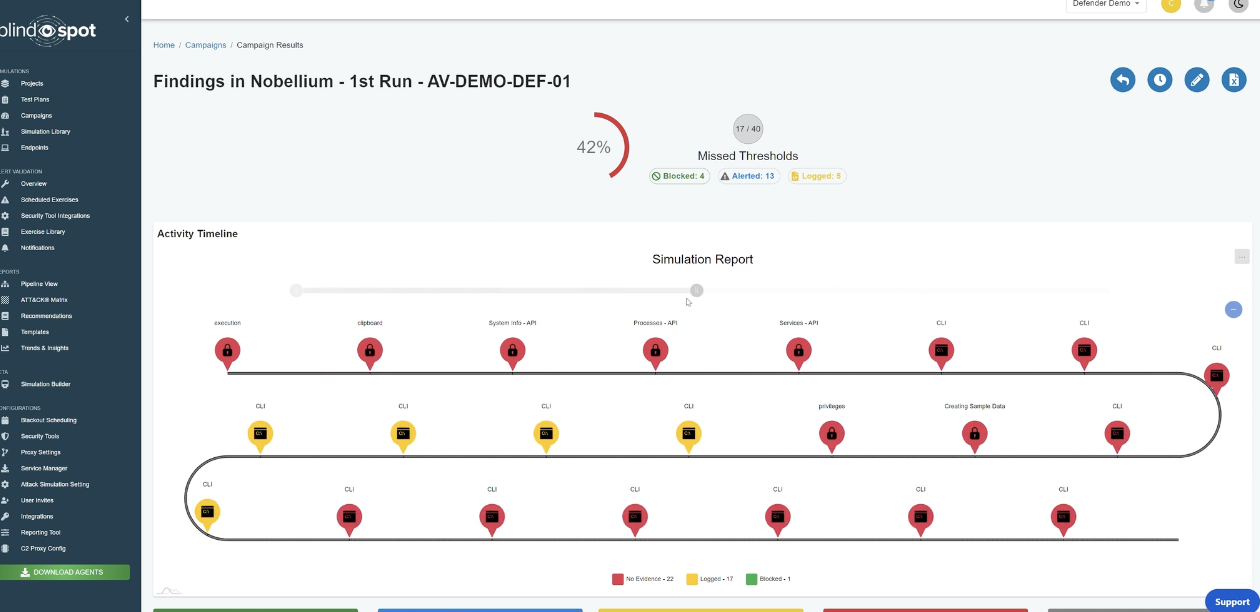
Comprehensively review your security tools' response to attack activity, identifying detection and alerting successes and failures.
Automated & Manual Options
BlindSPOT integrates with EDR, SIEM, and other tools for automated result scoring, or you can manually score the results.
Contact UsVisualize Controls
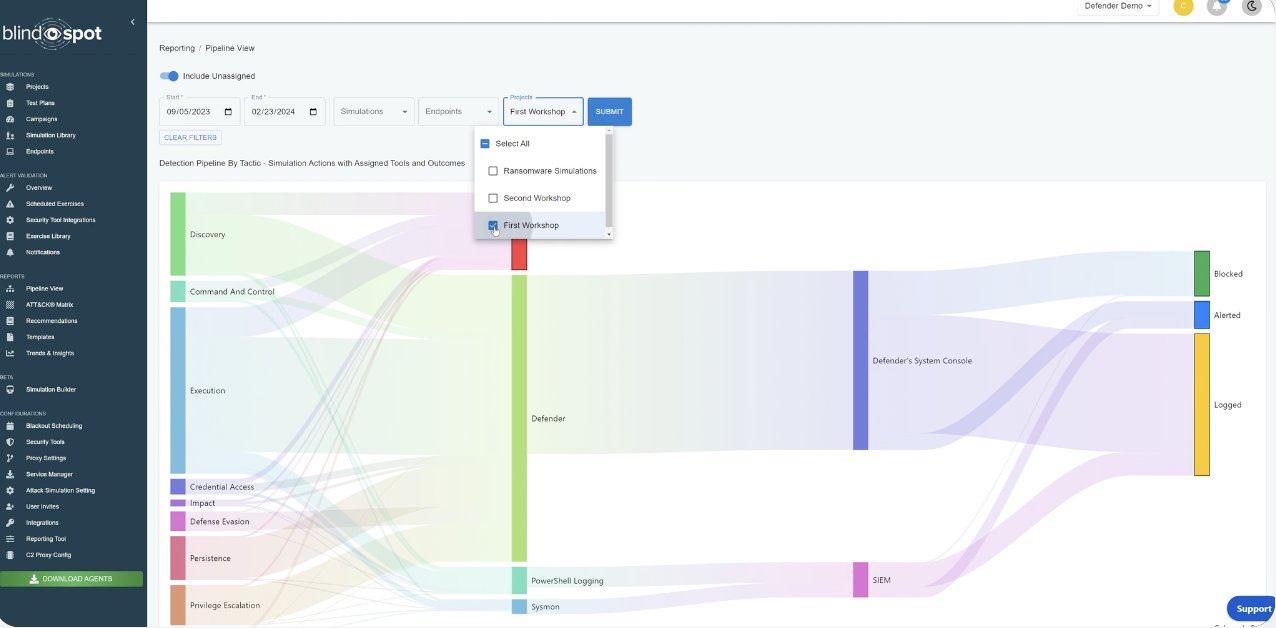
End-to-end visualizations of MITRE attack activities, security tool telemetry, and security control outcomes.
Optimize Your Pipeline
Visualize where your security tools fail and succeed, identify tool overlap, and demonstrate the need for additional security investment.
Contact UsActionable Reporting
Your automated and customizable report visualizes your security coverage successes and gaps, along with a prioritization of remediation recommendations.
Reporting Made Easy
BlindSPOT's reporting provides actionable direction to your technical team, along with the graphics necessary to deliver value to non-technical corporate stakeholders.
Contact UsAll Attacks Welcome
Select from our automated library of ransomware strains, ATP’s and other threats, build your attack chains from scratch using your tradecraft and execute manual attack activity via our C2 Integrations.
Contact UsAutomated & Manual Options
BlindSPOT integrates with EDR, SIEM, and other tools for automated result scoring, or you can manually score the results.
Contact UsOptimize Your Pipeline
Visualize where your security tools fail and succeed, identify tool overlap, and demonstrate the need for additional security investment.
Contact UsReporting Made Easy
BlindSPOT's reporting provides actionable direction to your technical team, along with the graphics necessary to deliver value to non-technical corporate stakeholders.
Contact Us
Value Delivered

Find Your Security Tool Coverage Gaps Before They Are Exploited
With Attack Simulations, your team is empowered to regularly practice, tune tools and create advanced alerting rules to detect real-world attack activity.
Ready to automatically exercise and validate your detection and alerting rules every day, check out our Alert Validation page.
SMART. CAPABLE. RELIABLE.
Super-Charge Your Business.
Contact us today to expand your security offering, meet market demand and secure our world.
Contact Us