A Note from the CTO:
Building BlindSPOT is fun, full stop.
Both the development and tradecraft teams get the chance to solve difficult challenges and puzzles with the direct goal of making BlindSPOT a better tool for you to answer the question “What would happen if…”.
Of course, because we are performing the same behavior that attackers do, the same defenses that get put in place to stop them, stop us. We don’t just end up building simulations that mimic the same behavior that threat actors do, we end up acting like threat actors through the whole development lifecycle.
A lot of the updates we do to agents, payloads, and other components are all geared to making sure that BlindSPOT provides an effective tool in your toolbox.
- Effective to build realistic simulations, encapsulating the tradecraft we bring (or the tradecraft you bring).
- Effective at being easy to execute and fast to get results from.
- Effective to rapidly deploy and scale testing across your environment.
- Effective to generate useful metrics that help you understand how you will perform against real adversaries.
We’re excited to see how the new features help you improve your defenses, and what ideas they generate for you. As always, we’d love to hear from you on what you think about BlindSPOT, and where we can help you answer the question “What would happen if…”.
OK, on to the show!
-Ben Finke, OnDefend Co-Founder/CTO
New PowerShell Module
We’ve added a new PowerShell module to the list of payload modules. Previously the run module was the most common way to execute any PowerShell activity, but that meant every step that ran PowerShell started a brand-new PS process, executed the command, and then exited the process. Our new PowerShell payload module starts a PS process and then lets you interact with it throughout the simulation. So, if you set a variable in step 8, you can reference it again in step 17! And if you bypass a security control (cough AMSI cough), you get to take advantage of that work for the rest of the simulation.
You’ll see the PowerShell module already listed in the Simulation Builder, and we’re adding lots of new simulations that take advantage of this new feature.

New Alert Validation Dashboards
Alert Validation has been under development in all phases, but the new dashboard helps you zero in on any issues with your detection uptime, and understand how long it takes to resolve any issues, once found:

Learn More About Alert Validation
New Agent Builds Available (in Beta)
We’ve completely rebuilt the BlindSPOT agents from scratch, enhancing functionality and adding some additional tradecraft to make them easier to deploy and run. Available now as the “Beta” option in your agent builder, give it a try!
One Last Thing….
Thank you for taking the time to read our newsletter. We are committed as an organization to continue pushing boundaries within the world of innovation, BlindSPOT is the product of that.
If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
A note from the CTO – Ben Finke
If you haven’t heard about our Alert Validation module yet, let me be the first to (happily) tell you what it is and why you should care. Alert Validation isn’t designed to help you identify gaps or “blindspots” (that’s what Attack Simulations are for). Alert Validation helps you focus on ensuring that your detection capabilities are working as expected today. That means ensuring that telemetry arrives, alerts fire, and it all happens in a time frame that you find acceptable.
Alert Validation is fully automated, executing the activity on an endpoint in the environment, then connecting to the security tools and watching for the alerts to fire. Once you’ve set up the Alert Validation Exercise, it takes over from there. You get defect reporting (one or more alerts didn’t fire as expected, or it took longer than you wanted) when the testing fails, and over time we build a detection uptime report.
Sending a canary event through the pipeline gives you the assurance that the detection capabilities you rely on work, with much more certainty than simply monitoring the components of that same pipeline. Any failures that would prevent your alerts from working against a real attacker will be identified and let you address them without the mess of having missed a real event.
And we don’t have to stop at the first alert. If you have an MSSP or MDR provider, we can include them in the automation too. Now you can have daily validation that your security provider can see activity in your environment, and exactly how long it took for them to see it. Oh, and Alert Validation can automatically close the alerts created through testing, keeping that load off of your team and without impacting your service delivery metrics.
Alert Validation can be done on its own or is a great second step after you’ve spent time using the Attack Simulations to tune your tools and want to make sure they stay tuned.
If you’re interested in seeing what Alert Validation can do for you, let us know, and we’d be happy to get you set up! Learn More
-Ben Finke, OnDefend Co-Founder/CTO
Updated Alert Validation Details Page
Keeping the Alert Validation talk going, we recently refurbished our Alert Validation detail page to make it easier for you to see the results of each Alert Validation Exercise.

Each alert that is setup in the Exercise is shown with the Pass or Fail grade, and drilling into each you can see exactly how long it took the alert to get there, once that activity happened on the system.
Updated Campaigns Page
Our Campaigns page was recently renovated too, making it easier to see exactly which campaign is which:

Learn More About Attack Simulation
BlindSPOT Customer Success: Healthcare & Ransomware
Learn how an enterprise hospital system used BlindSPOT to validate the effectiveness of their security controls, allowing the hospital to focus on what matters most: patient care.
Read The Customer Success Story
Partner Announcement: BDO Digital integrates BlindSPOT into Active Assure Security Service
“We are proud to empower BDO Digital with our attack simulation tool BlindSPOT, providing organizations visibility into the effectiveness of their security controls and proving the value of these investments,” said Chris Freedman, Co-Founder of OnDefend. “It is no longer a question of if but when a company will face an attack. While organizations invest in technical security controls to prevent, protect, and prepare, we’ve found that security programs needed a way to validate those tools will work during those critical moments.”
One Last Thing….
Thank you for taking the time to read our newsletter. We are committed as an organization to continue pushing boundaries within the world of innovation, BlindSPOT is the product of that.
If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
A note from the CTO – Ben Finke
Our goal is to build tools that let you test your security controls – quickly, thoroughly, and safely. Most of what we execute via BlindSPOT is intended to look just like malicious activity. After all, that’s our purpose here (excluding the actual nasty impact). In some ways, we find ourselves facing similar problems that real threat actors probably do (although we certainly don’t sympathize with them). In this newsletter, we will share some recent updates to the platform that are designed to make it easier for you to leverage BlindSPOT as part of your processes, including testing tools, detections, and the teams’ ability to use those tools.
By the way, if you couldn’t make it to our recent webinar featuring CISA supervisory agent Kirby Wedekind, FBI agent Paul Magnusson, and myself, I highly recommend checking it out. We delved deep into the major threats of the year, covering everything from prevention to response strategies and available resources. You can catch it all here: CISA Year In Review: A deep dive into the biggest threats, an outlook into the new year and how to prepare. > OnDefend
Alert Validation – Crowdstrike Falcon Beta!
In our last newsletter, we announced that our new Alert Validation feature was live for Microsoft Defender and Sentinel. Today, I am thrilled to announce that we have added CrowdStrike Falcon to that list (in Beta). With this integration, you can automatically exercise Crowdstrike Falcon detection and alerting, without any manual intervention from your team, and be alerted when an issue occurs. Alert Validation is an excellent way to put a detection into “maintenance” mode, allowing you to use the Attack Simulation tools to identify more gaps and blind spots in your detection program.
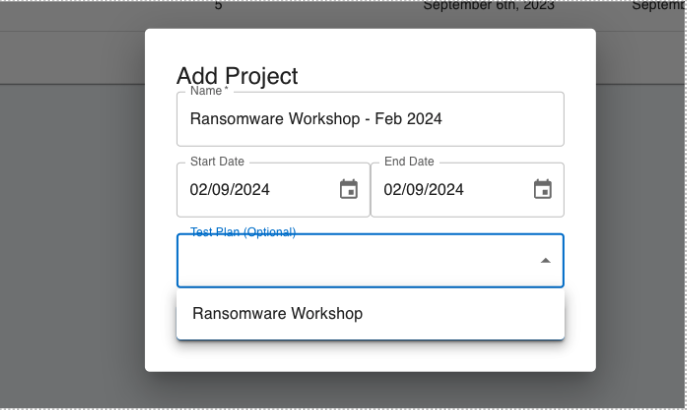
Test Plans
If you need to run the same set of campaigns across a large group of endpoints, Test Plans will save you time and make the setup easier. Test Plans allow you to configure the specific campaigns you want to run, create a project, and simply select the endpoints to include. Test Plans will take care of building out all the individual campaigns for you.
New Simulation – Alert Validation Monitoring
If you want to run a campaign that triggers numerous alarms from a wide variety of techniques, check out our new simulation, Security Monitoring Validation v1.0. Inspired by various reports of the Top 10 TTPs used by attackers, this simulation covers a variety of techniques and procedures in a single simulation.

Sneak Peek into the Dev Channel
Here are some exciting projects we are cooking up in the lab that we will be able to share with you shortly:
- BlindSPOT Satellite – a purpose-built system to serve as a target for exfiltration, Command and Control, and File Downloads – letting you change the Internet facing target and expand the ability to test your network perimeter systems.
- Attack Simulation AutoScoring – Soon to be released for both Microsoft Defender and Crowdstrike Falcon – with more tools on the way.
- SentinelOne Alert Validation – yep, will have it in the lineup shortly.
One Last Thing….
We have been thrilled to see the simulations our users have been creating in the sim builder, and we are working on a way to let the BlindSPOT community share some of this incredible tradecraft and simulations (if you choose to share it). Thank you for using BlindSPOT as the platform to help you with your security testing work, and we look forward to continuing to build features that make this platform easier and more capable for you!
If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
The newly released 2023 CISA year in review is out and we’re taking a deep dive into the biggest threats, an outlook on the forecasted trends for this year, and a discussion into whether these trends are inevitable or solvable.
Join CISA supervisory protective security advisor Kirby Wedekind, FBI supervisory agent Paul Magnusson, and OnDefend CTO Ben Finke for this interactive discussion where they’ll:
- Analyze the biggest trends, threats, and industries targeted in 2023.
- Explain why they believe these threats topped the list.
- Delve into steps organizations can take to prevent an attack and what to do if they are attacked, including analysis and forensics.
- Compliance, regulations, and reporting- what is that going to look like in the new year?
- Reveal the common patterns discovered within organizations after a breach.
- Look forward to 2024 and how to develop an IR plan for the new year.
You can watch the full recording now:
Speakers:
Ben Finke, OnDefend Co-Founder/CTO
Ben Finke has almost 2 decades worth of experience in cybersecurity, starting as a communication officer in the U.S. Air Force. Over the course of his career Ben worked with organizations ranging from government agencies to fortune 500 companies including, being embedded in development teams in SaaS companies, overseeing a red team for testing critical infrastructure systems, and running the security practice for a managed security provider. In 2016, Ben Co-founded OnDefend where he currently serves as the Chief Technology Officer. Ben also is the creator of BlindSpot, a purple team testing automation tool. Ben has a bachelor’s degree in computer science from Florida State University.
Kirby Wedekind, CISA Supervisory Advisor Protective Security Advisor
Kirby Wedekind serves as the Cybersecurity and Infrastructure Security Agency’s Supervisory Protective Security Advisor in northeast Florida. Based in Jacksonville, his duties include serving as a liaison from CISA to local government agencies and private industry; fostering community awareness on security topics ranging from cybersecurity to active shooter preparedness; conducting vulnerability assessments of critical infrastructure; and sharing security-related information with communities of interest across northeast Florida. Dr. Wedekind supervises the Protective Security Advisors in North Carolina and South Carolina.
Paul Magnusson, FBI Supervisory Agent
Paul Magnusson serves as a Supervisory Special Agent with the Federal Bureau of Investigation in Jacksonville, Florida. SSA Magnusson started his law enforcement career in 1998 as a Deputy Sheriff with the Washtenaw County Sheriff’s Office in Michigan, where he led all cyber investigations and computer forensics examinations. In 2005, Magnusson entered on duty with the FBI as a Special Agent assigned to the Minneapolis Division Cybercrimes Task Force and became a member of the FBI Computer Analysis Response Team, conducting computer forensics examinations. In 2008, he was promoted to Supervisory Special Agent of the Tactical Operations Section within the FBI Operational Technology Division. In 2018, SSA Magnusson transferred to the FBI Jacksonville Division, where he has managed various programs, including the National Security and Criminal Cyber, Computer Forensics, Surveillance, Aviation, Electronic Technicians, and Technically Trained Agent programs. SSA Magnusson earned his Bachelor of Science in Criminology and Masters in Information Security & Technology from Eastern Michigan University.
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world threats. From ensuring compliance with industry standards to building out mature security programs our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results.
Originally published in Hotel Executive: Hotel Executive Article
A quality guest experience and a hotel’s success go hand in hand, but at what cost? Ease of access around the hotel, instant connection to Wi-Fi, almost every aspect between the check-in to check-out process requires some form of technology. However, each of those access points is a prime target for cybercriminals to exploit and one of the reasons why attacks are only expected to increase.
Why Target Hotels?
Hotels have become appealing targets for cybercriminals for several reasons, including the data they collect, the volume of credit card transactions they make, the complex system of vendors, guest Wi-Fi networks, the proprietary and 3rd party apps and platforms they use, as well as the constant journey to make the customer experience as smooth and easy as possible.
The primary driver of attacks on hotels have historically been driven by financial gain, data theft, or causing disruption to hotel operations. One of the primary objectives is to steal payment card data, including credit card numbers, names, and security codes, which can be used for unauthorized transactions or sold on the dark web for profit.
Identity theft and fraud are also common goals, with cybercriminals aiming to use stolen personal information to commit various fraudulent activities. Ransomware attacks seek to encrypt critical hotel data, such as guest reservations or financial records, with attackers demanding a ransom in exchange for the decryption key, disrupting operations until payment is made.
Additionally, attackers may target a hotel’s financial systems, corporate espionage may occur in luxury or corporate hotels, and data exfiltration can be used for extortion, selling information to competitors, or intelligence gathering. Some attacks aim solely to disrupt hotel operations, causing financial losses and reputational damage. Opportunistic attackers may seek any vulnerability to exploit for financial gain.
Hotels are seemingly easier to infiltrate than other industries such as healthcare or financial. Historically, the hospitality industry is not known for building and incorporating a robust cybersecurity program. Which leaves hotels as low hanging fruit for these cybercriminals.
In fact, within the hospitality industry are likely unaware of how vulnerable their organization could be to an attack. A joint study from Cornell and FreedomPay revealed that of the 300 hospitality specific enterprises surveyed nearly all, 96% said they are confident in their companies internal risk assessment processes. Yet, nearly one-third (31%) experienced a data breach in their company’s history, the majority – 89% – having experienced more than one breach attempt in a year and 69% attacked more than three times in a year.
Top 3 Hotel Attack Vectors
We’ve covered why cybercriminals target hotels but how do they do it? While there are countless of ways for an attacker to get into a system, there are three primary points of access that every executive should be aware of.
The most common method is phishing attacks. Cybercriminals send deceptive emails to trick hotel staff, guests, or third-party partners into revealing sensitive information or downloading malware. You’ve likely received one of these emails in the last month, offering a “free” gift card or an “urgent” message from the IRS.
This method was the cause of the recent “vishing” attack on MGM Casino where hackers had access to the organizations system for 10 days. The adversary impersonated a fellow MGM employee on a phone call and persuaded the information technology helpdesk to provide them access into the MGM environment. From there, they gained access to other systems and eventually executed a ransomware with a total cost yet to be finally calculated, but you can be assured, it will be in the tens of millions.
Another common attack method is point-of-sale and payment cards which commonly pose the biggest threat to the hospitality industry. Threat actors find point of sale (POS) systems to be the most direct route to credit card information and financial gains. These systems are often configured improperly, with weak passwords and/or insecure remote access, opening the door for cybercriminals to easily infect them with card-skimming malware. The problem is compounded by the fact that hotels typically delegate their POS security to third-party vendors, offering threat actors yet another potential attack vector. Hotel POS systems are complex because they have multiple POS terminal locations – front desk, on-site shops, spas, restaurants, parking etc. – and thus the possible entry points are dispersed and more accessible. In 2017, Hyatt Hotels Corporation reported a data breach that impacted approximately 41 of its properties in 11 different countries. The breach involved the theft of customer payment card information from the hotel’s POS systems. The attack occurred due to malware that was installed on the POS systems, allowing cybercriminals to capture payment card details during transactions.
Finally, I couldn’t imagine staying at a hotel now a days that doesn’t offer Wi-Fi, unfortunately, this has opened yet another vector for hackers to infiltrate. Public Wi-Fi networks have fewer security levels than private networks. And many attacks on hotel systems are made possible by human error – for example, if an unaware hotel employee configures a secured network as “open,” they have effectively created a rogue access point (AP). Cybercriminals can use this rogue AP to attack the network from the hotel lobby or even a nearby building.
The Cost of a Cyber Breach
A cyber breach can bring about substantial legal and financial consequences for those involved. From a financial perspective, organizations can face direct costs such as expenses associated with investigating the breach, notifying affected individuals, offering credit monitoring services, and implementing security fixes.
According to IBM’s Cost of a Data Breach Report 2023 (2) the average cost of a breach for the hospitality industry was $3.36 million dollars, up from just under $3 million dollars the year before.
Indirect costs may include revenue loss due to downtime, damage to the organization’s reputation causing reduced business, and increased insurance premiums. Moreover, various regions have data protection regulations that demand compliance. Failure to do so can lead to substantial fines and penalties. Legal liabilities could arise as breach victims initiate legal actions, resulting in lawsuits, settlements, and legal fees. Organizations must also bear the cost of remediation, including upgrading security systems, forensic investigations, and implementing enhanced security measures.
Reputation damage can have long-lasting financial effects, leading to diminished customer trust, lower sales, and customer attrition. Lastly, the financial impact can extend beyond the immediate aftermath, affecting stock prices, investment prospects, and long-term financial stability.
Five Notable Hotel Breaches and How the Hackers Got In
InterContinental Hotels Group (2016): InterContinental Hotels Group (IHG) disclosed a data breach that affected more than 1,200 of its properties in the United States. The breach occurred due to a malware attack on the hotel chain’s payment card processing systems, which compromised guests’ payment card information.
Marriott International (2018): One of the largest hotel data breaches in history, the Marriott breach involved the exposure of data of approximately 500 million guests. It was discovered that unauthorized access to the Starwood guest reservation database had occurred, potentially compromising personal information, including names, addresses, phone numbers, passport numbers, and payment card data. The breach was ongoing for several years before being detected.
Hilton Worldwide (2019): The Hilton Worldwide data breach affected over 4.5 million guests. The breach was caused by a phishing attack that targeted Hilton employees. The phishing attack tricked employees into revealing their login credentials, which were then used by cybercriminals to access the Hilton reservation system. The cybercriminals were able to steal guest data, including names, addresses, phone numbers, email addresses, and passport numbers.
Wyndham Hotels & Resorts (2020): The Wyndham Hotels & Resorts data breach affected over 600,000 guests. The breach was caused by a malware infection in the Wyndham Rewards loyalty program. The malware was able to steal guest data, including names, addresses, phone numbers, email addresses, and Wyndham Rewards member numbers. For some guests, the malware also stole payment card numbers and expiration dates.
Wyndham Hotels & Resorts (2022): The May 2022 Wyndham Hotels & Resorts data breach affected over 1 million guests. The breach was caused by a malware infection that was able to steal guest data, including names, addresses, phone numbers, email addresses, and passport numbers.
Compliance Does Not Mean You Are Cyber Secure
Part of being an executive is making the hard decision about where to cut costs to keep a business profitable. Over the years, I’ve noticed a trend when it comes to organizations investing in cybersecurity. If the company meets compliance standards then they are protected but that’s not entirely true. Compliance standards within the realm of cybersecurity has a long way to go.
A Deloitte survey of 500 c-level executives found that 85% of chief information security officers said they can measure and demonstrate compliance (3). If that’s the case, why are companies still struggling with major breaches? That’s because current compliance standards only scratch the surface when it comes to being secure. Without getting technical, let’s look at your home security system in terms of cybersecurity compliance. It would be like, proving to your insurance company that you have door and window sensors that should go off if someone we’re to break in, but never really knowing if those sensors worked until someone was actually breaking in, but at that point it’s too late. Many compliance standards within cybersecurity can lead to the same outcome. An organization is required to have certain programs, training, or certifications but whether they are working and proving to be effective is another story. Now, that’s not to say that every organization does this but organizations that rely solely on “checking the box” are much still vulnerable to an attack.
Things to Focus on to be More Cyber Secure
- Educate and Empower All Staff Members
In more cases than not, a cybersecurity issue starts with human error. This is not to put fault on employees but primarily the lack of training and awareness. As we saw with the most recent MGM hack, most of these attacks begin with phishing, so training employees to be aware and prepared for phishing tactics is crucial.
Our firm was once hired to run phishing training for the entire organization. We sent out phishing emails to see who would respond and click the exploitable link. The CEO of the company, who knew we we’re running the training forwarded the entire email to the company believing there we’re actual changes from HR that everyone needed to be aware of.
It goes to show even if you are prepared and warned of an attack, it is so easy for something to slip by. These criminals are extremely tricky and good at preying on an individual’s emotions or finances to get them to open or download an email.
Regular training empowers employees to make informed decisions and act as the first line of defense. It’s important to remind everyone that safeguarding your companies most sensitive information is not just as “IT” issue.
- Bolster Network Infrastructure
Hotels must patch and update their systems as frequently as possible to mitigate their vulnerabilities. When a network is left unpatched, hackers can exploit these weaknesses to attack the system. In particular, hotels should direct their utmost attention for patching and updates to POS systems. Here are a few steps hotels should take to ensure their POS systems are secure:
- Use complex passwords on POS systems.
- Use two-factor authentication.
- Ensure antivirus or endpoint protection is up-to-date.
- Separate the POS network from other networks and investigate anomalies.
- Filter which external IP addresses can reach the remote-access mechanism of the POS controller.
- Use PCI-Validated Point-to-Point Encryption (P2PE) to encrypt credit card data immediately upon payment.
- Segment Wi-Fi networks by making guest Wi-Fi and business networks separate.
- Deploy Wireless Intrusion Prevention Systems (WIPS) to detect and prevent hacking attempts against the Wi-Fi network.
- Assess Vendors’ Security Capabilities
Many cyberattacks are carried out through third-party vendors. Third-party vendors are part of any organization’s attack surface and pose a huge risk to overall security. To assess third-party vendors, start by conducting a thorough risk assessment. Identify the criticality of their services to your organization, the type of data they handle, and their security practices. Request and review their security policies, compliance certifications, and incident response plans. Evaluate their past performance and reputation through references or industry reviews. Assess their financial stability to ensure long-term viability. Lastly, establish clear contractual obligations regarding security, data protection, and compliance to mitigate risks associated with third-party relationships. Regular monitoring and audits should also be part of your vendor management strategy to ensure ongoing compliance and security.
- Perform Internal Threat Hunting
Hotels have massive digital footprints because of all the different systems they use. Hackers often try to gain entry into a network and then move around within the system to find data they find valuable. Thus, security teams need to monitor their own internal network traffic to identify suspicious activity and discover potentially unauthorized access.
Threat hunting with a breach and attack simulation (BAS) solution is a proactive cybersecurity approach that helps organizations uncover potential threats and vulnerabilities within their networks. This process involves carefully planning and preparing objectives, selecting the right BAS tool, and assembling a dedicated threat hunting team. Data collection, including logs and network traffic, is crucial to the analysis. BAS tools simulate various attack scenarios, and the results are scrutinized for anomalies and unusual patterns. When potential threats are detected, they are investigated, and if confirmed, immediate action can be taken to contain and remediate them.
- Develop and Incident Response Plan
Hotel security teams cannot afford to sit around and wait for attacks to happen. They need to assume it’s a matter of when, not if, they’ll be targeted.
According IBM’s Cost of a Data Breach Report 2023, on average it took organizations 204 days to identify a breach and another 73 days to contain it (4). Every hotel should have an incident response plan in place if a data breach does occur to help streamline the communication and mitigation process.
One way to stress test your incident response plan it through tabletop exercises which hold significant value for organizations as they provide a structured and cost-effective way to assess and improve their incident response capabilities. These exercises simulate various crisis scenarios, allowing executives and key stakeholders to collaborate, identify weaknesses, and refine their response plans. By doing so, organizations can better prepare for real-world emergencies, minimize the impact of incidents, and protect their reputation and assets.
At the end of the day, even if a security team had an unlimited budget, there is no way to 100% prevent a cyberattack. However, with the right tools, training, and response plans in place, companies can at least take steps in the right direction.
Resources:
Cost of a data breach 2023 | IBM
The Future of Cyber Survey | Deloitte US
Cost of a data breach 2023 | IBM
Media Contact:
Lauren Verno, OnDefend VP of Communications: Media@ondefend.com
Welcome to 2024! As we take on this new year, we’d like to reintroduce our company, OnDefend.
We are a cyber security firm with a unique, human-centric approach. We understand that every challenge is different and that one-size-fits-all solutions don’t always cut it.
At OnDefend, we stand out from the crowd with our agility and innovation. We’re quick on our feet, ready to design customized security solutions based on the threat actors targeting your organization. But we don’t just adapt; we innovate. You’ll find us at the front lines, tackling challenges head-on, and devising innovative strategies. We don’t believe in impossible, only in finding the right solution.
We emphasize customization – understanding that every company’s budget, timeline, and security needs are unique. Thus, we deliver tailored solutions designed to meet your specific requirements. Our reporting isn’t just insightful, it’s actionable. We provide clear, easy-to-understand reports with strategies you can implement immediately to enhance your security posture.
Connecting with our clients is at the heart of what we do. We prioritize communication, ensuring regular updates and prompt responses. We value the human element and put people first, resulting in exceptional project management and enhanced client satisfaction.
This new year, join us on our journey to prepare for and defend against threats for years to come. With OnDefend, you’re not just complying – you’re preparing to defend. Let’s take on 2024 together, and strengthen your company’s security infrastructure with our tailored, agile, and innovative solutions.
Contact us today, and let’s make 2024 the year of unshakeable defense.
A Note from the CTO
What a year this has been! If you’ve been with us throughout 2023 I hope you’ve been able to enjoy all of the new features, content, and improved performance of the BlindSPOT platform!
I’d like to thank everyone who has had a hand in helping us make BlindSPOT better – whether you gave us feedback during an exercise, sent in a suggestion, or shared some of the stories of your executions in the platform – thank you.
To the development team and the content team, I am honored to work with each of you every day, and I continue to be amazed at your creativity and determination to build something we are so proud of.
Alright, let’s get to some of the highlights of the last couple of months!
-Ben Finke
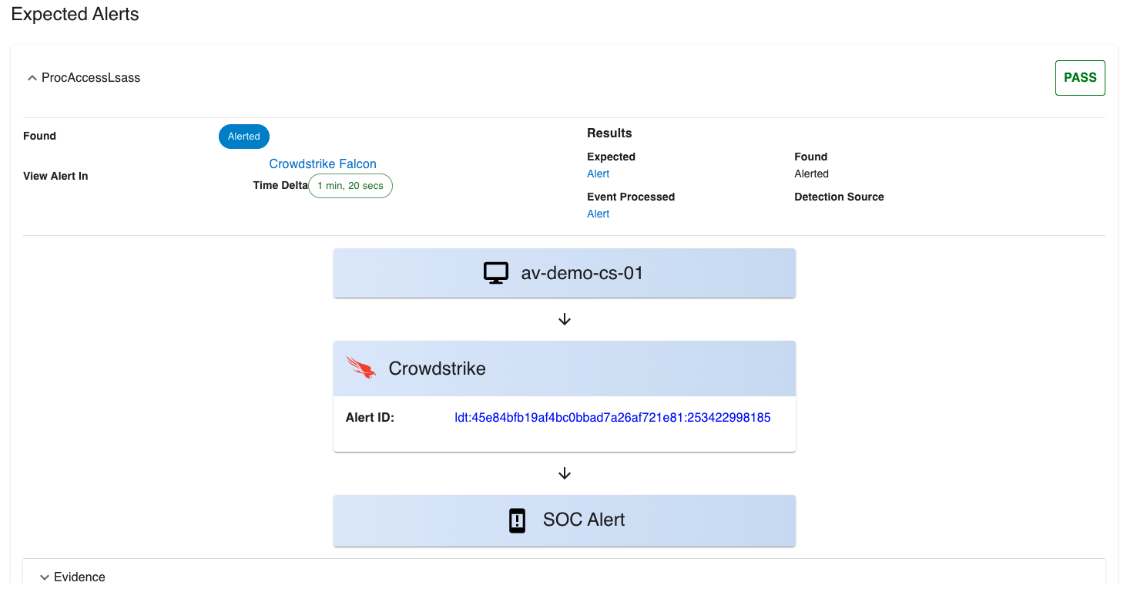
Alert Validation is Live!
BlindSPOT has always provided a way for you to find, well, your blindspots, with our Attack Simulation capability. But once you get those tools tuned and alerts just the way you want, how can you make sure those tweaks remain ready? And arguably just as important, how do you know you are getting the right data into your pipeline for those alerts to fire? Enter Alert Validation!
We leverage the Attack Simulation capability within BlindSPOT to execute attack activity on endpoints in your environment, then connect to your security tools and find the alerts you expect to fire – and give you all the details about them:
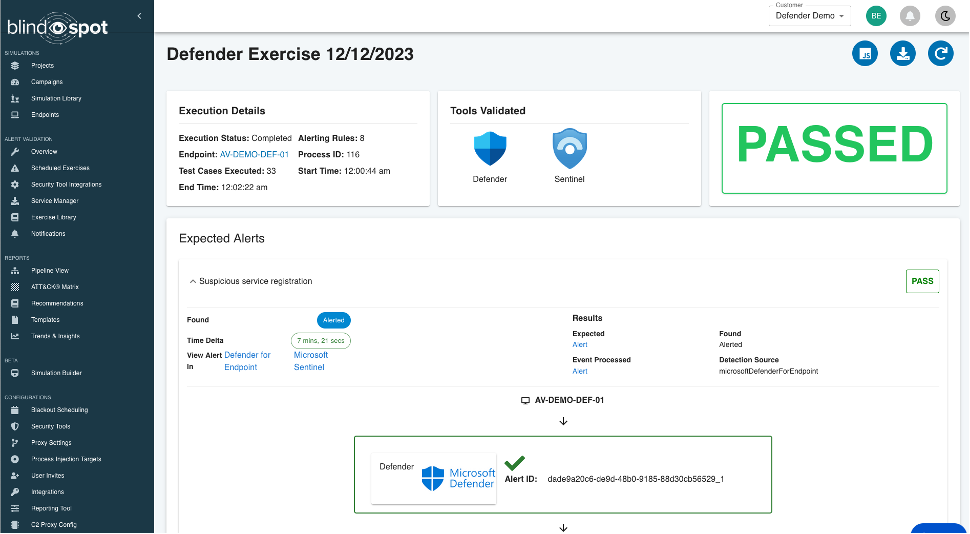
We’ll show you the exact alerts firing in your tools, and how long it took for them to fire (in this case, just over 7 minutes). If any alerts you were expecting don’t fire, we’ll let you know.
All this means you get proactive testing of your detection capabilities, end to end, fully automated and over time you get a Detection Uptime report!
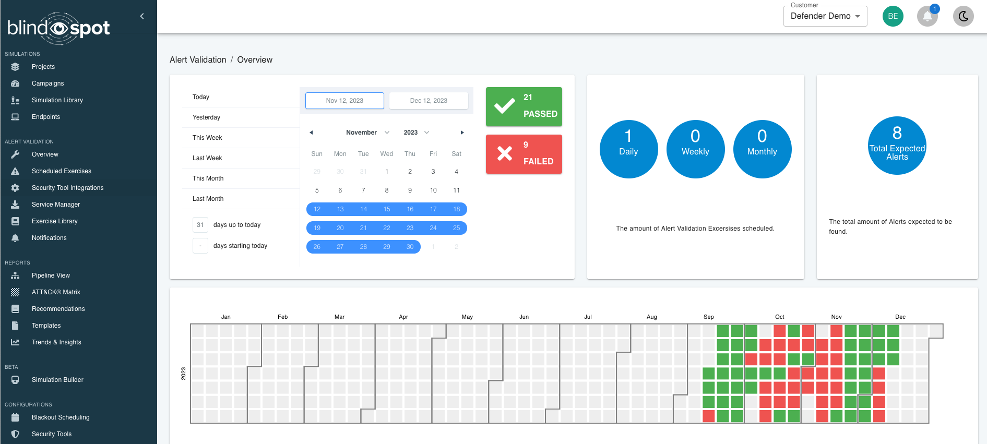
We’re starting with Microsoft Defender for Endpoint and Sentinel, and plan to expand those capabilities to include more tools in the very near future.
Already a BlindSPOT user and want to check out Alert Validation? Let us know if you’d like to try it out.
P.s. we’d love to know what tools you’d like for us to include in our next update!
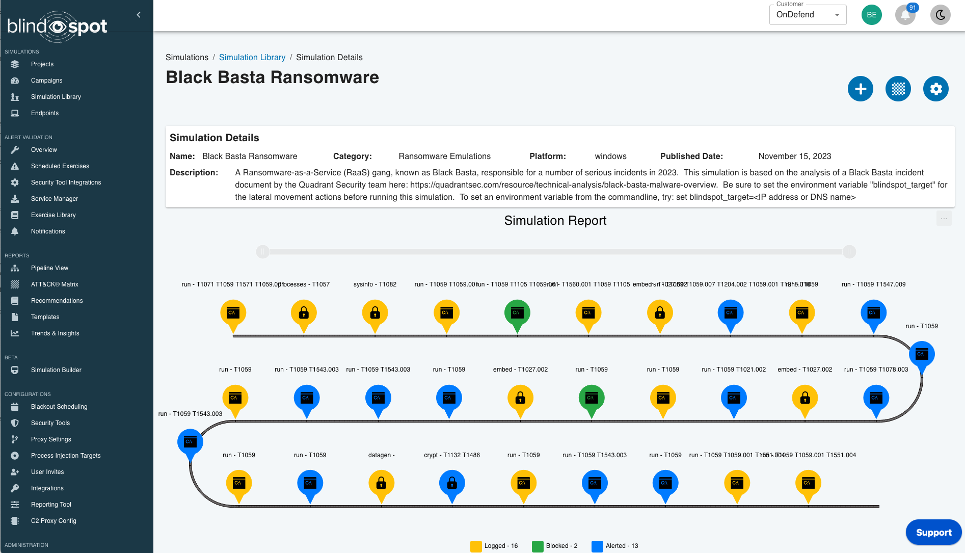
New Simulation: Black Basta Ransomware
In the last BlindSPOT newsletter, we told you about our newly redesigned simulation library that streamlines the process when you want to find a specific simulation you need.
We continue to build out that simulation library and wanted to highlight a new release, the Black Basta Ransomware simulation.
Based on the excellent write-up by our friends at Quadrant Security this simulation includes lots of new tradecraft not seen in other ransomware intrusions, including, a chained LNK -> JS -> CMD -” regsvr32 executing a malicious DLL, all packed in an ISO image file.
Phew!
New Service-Based Agent
The standard BlindSPOT agent was designed to be easily placed on target systems, quick and flexible to execute, with simple cleanup (just delete the file!), but sometimes you may want a more persistent version of the agent, one that can always be ready to run a campaign, even surviving reboots. Enter our new BlindSPOT Service Manager:
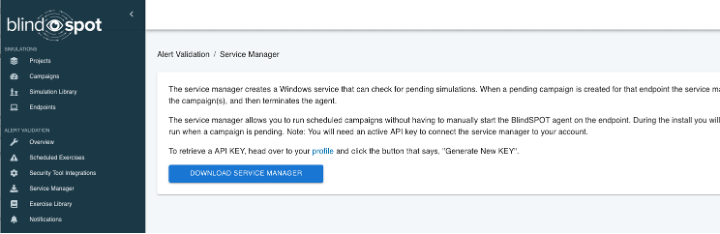
Download the Service Manager, grab an API key (oh yeah, did I mention our API is live too!), and run the downloaded MSI. You’ll see a new app on the machine, the BlindSPOT Service Manager. Enter your API key, and now you can install the service, specifying the specific BlindSPOT agent you want to use to run any campaigns you assign to that endpoint:
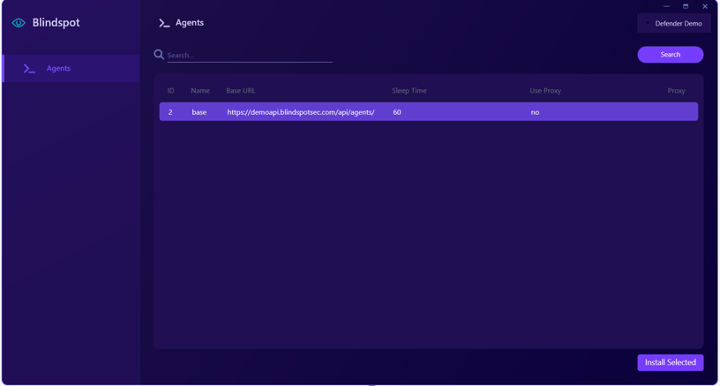
Pick the agent you want, click on “Install Selected” and you’re ready to install your BlindSPOT agent service:
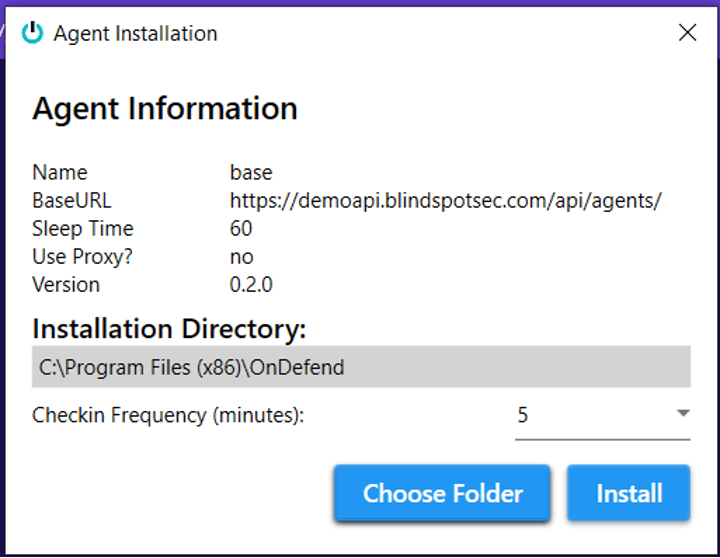
The service will check in with BlindSPOT, and when it sees you’ve got a campaign ready to run it will download and/or start the agent, execute the campaign, and then put the agent back to sleep until the next one. Works great for running Attack Simulations, and pairs nicely with the Alert Validation feature too!
What We’re Working On
BlindSPOT Satellite: We’re building an integrated utility that you can use to test data exfiltration techniques, execute different Command and Control traffic patterns (C2), and source downloads to execute tool ingress techniques. You’ll be able to use our satellites, or deploy your own on your own custom systems, using any domain you want.
Attack Simulation Autoscoring: Building on the success of our Alert Validation feature, we’ll soon have fully automated autoscoring for Attack Simulation campaigns too. (I know many we are all excited for this one.)
One last thing…
BlindSPOT was always a dream of ours and seeing it run successfully in organizations around the world is the best present we could ever ask for. From the bottom of our hearts, We want to thank you for joining this BlindSPOT journey and am looking forward to the new year. Happy Holidays everyone!

If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
Can you smell the turkey cooking? Before the holidays begin, let’s catch up on the latest cyber threats, a wrap up of cybersecurity awareness month, and BlindSPOT developments.
Cybersecurity Awareness Month
Let’s start off with the obvious, every month should be cybersecurity awareness month.

We kicked off the month at WJXT News4Jax, highlighting easy and free ways to keep your data safe.
Cybersecurity Awareness Month: OnDefend Explains How You Can Keep Your Data Safe > OnDefend
—
Cybersecurity companies are not just made up of hackers. From project managers to product development, we wanted to give an inside look at who actually works at a cybersecurity company.
Getting To Know The Different Roles Within A Cybersecurity Company > OnDefend
—
While not everyone who works at OnDefend is a hacker, we wouldn’t be able to offer our red-team capabilities without a few. In the Pentester Roundtable, we sat down with two ethical hackers and deep dived into getting into and staying in this career.
Pentester Round Table- Part 1 – YouTube
—
We’re lucky enough to work with some pretty interesting partners and industry leaders. It’s safe to say they have seen a few interesting moments throughout their career. While we could never cover them all, here’s a highlight of some of the worst ” Cybersecurity Horror Stories.”
Cybersecurity Horror Stories > OnDefend
Cybersecurity Roundup: Top Stories from the Digital Frontlines
Ransomware attacks are stealing more than just data, but potentially lives. In the beginning of 2023, The US Department of Health and Human Service Office for Civil Rights was hit with a total of 327 reported data breaches. The massive increase of over 100 percent from the 160 breaches they had on record by mid-2022.
Ransomware: The Unseen War Holding Lives Hostage (thecyberexpress.com)
—
Having trouble getting ChatGPT to work? Open AI, the parent company of ChatGPT confirmed the outages can be linked to ongoing distributed denial-of-service (DDoS) attacks. While OpenAI has yet to publicly confirm who exactly is behind the attacks, a threat actor known as Anonymous Sudan claimed to be behind them due to the ongoing conflict in Israel.
OpenAI confirms DDoS attacks behind ongoing ChatGPT outages (bleepingcomputer.com)
—
The US government has launched a new campaign to promote critical infrastructure security and resilience, focusing on broad, strategic strategies. The Shields Ready campaign complements CISA’s Shields Up campaign, which focuses on specific, time-sensitive actions.
US launches “Shields Ready” campaign to secure critical infrastructure | CSO Online
—
Okta is blaming the recent hack of its support system on an employee who logged into a personal Google account on a company-managed laptop, exposing credentials that led to the theft of data from multiple Okta customers. According to the company, the username and password of the service account had been saved into the employee’s personal Google account.
Okta Hack Blamed on Employee Using Personal Google Account on Company Laptop – SecurityWeek
OnDefend in the Spotlight
OnDefend CTO Ben Finke shares his thoughts and recommendations for cybersecurity compliance standards with Forbes Technology Council.
Billions of dollars are spent on cybersecurity every year, yet the problem of ransomware outbreaks, data breaches, and identity thefts continues to grow.
How do you raise the bar without adding unnecessary regulations?
You can check out Finke’s recommendations here: Why Cybersecurity Compliance Standards Still Have A Long Way To Go (forbes.com)
—
OnDefend is celebrating its second consecutive year as one of the fastest-growing companies on the First Coast. Despite the challenges of the past few years, we are proud to announce that we have achieved the 14th spot!
OnDefend named 14th fastest growing company on the First Coast
BlindSPOT

Did you miss our inaugural BlindSPOT newsletter? We are constantly updating the product from simulation libraries to new reporting graphics. This bi-monthly newsletter is meant to give every user an understanding of what’s new and what to expect in regard to updates. Here’s a sneak peek of what to expect in next month’s newsletter from OnDefend CTO Ben Finke:
“We’re always looking to build tools that helps you keep your organization safe. BlindSPOT attack simulations do a great job helping you find “blindspots”, but once you have those fixed, how do you make sure they stay fixed? Stay tuned for our next newsletter where we tell you all about Alert Validation.”
Missed out on last months? Catch up now.
BlindSPOT Newsletter: The Inaugural Edition > OnDefend
Anybody else feel like we just scratched the surface? That’s because we did. Stay tuned for this bi-monthly newsletter, for all of OnDefend’s latest and greatest.
If you want to stay in the loop about what’s happening at OnDefend, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
There is no doubt plenty of horror stories working in cybersecurity. For cybersecurity awareness month and Halloween, we teamed up with industry leaders and partners and asked them a simple question, “tell us a cybersecurity horror story.”
” When I first got into the field as an admin, I was informed that one of our Domain Admin accounts was a user called ‘hdesk’ and the password was ‘help’ and everyone in the company was aware of it. And I mean EVERYBODY! You can imagine how that went over at our security audit. Suffice to say, it was changed shortly after that.” – Daniel Lowrie, IT Pro TV
” I once got a call from one of our vendors telling us they found the entire code of one of our critical applications including secrets in clear text in an open GitHub repository. The developer thought the GitHub repo was secure by default. This became an escalated incident of course but also a great opportunity to educate developers on secure coding practices. ” – VCISO Carlos Rodriguez
” Client had serious concerns regarding the physical security controls of their main campus. My team was engaged to attempt to breach the primary building with no stated limitations.
The client’s facility was a large campus comprising multiple buildings supporting various corporate functions and operations. Upon completion of the reconnaissance phase, it was determined that we’d attempt to scale the first story of the target building via grappling hook and climbing gear.
Literally picture Batman & Robin slowly walking up the side of a building and that is exactly what we looked like, minus the costumes.
Upon gaining a successful foothold with the grappling gear and securing the belay lines, we began our single-story ascent. Within minutes, we noticed the beam of a flashlight slowly approaching our position and with the belay lines dangling on the ground, there was no mistaking what we were up to!
This is where the story gets good, so the security guard, Chad, approaches us and demands we come down. Once back on the ground knowing full well that our cover was about to be blown, we throw caution to the wind and tell Chad at least most of the truth, that we’re here on a consulting engagement. Fully expecting Chad to raise the alarm to call the police, we were in total shock when Chad said “Okay, cool, but please be careful not to damage the building.
Um, wait what? Chad never asked us for identification, a get of jail free letter or even our names!
So once the coast is clear, we return to our superhero’s scaling that daunting first story wall. Upon reaching the summit a solid 12-15 feet above ground, we stumble over the perimeter wall and discover an exterior glass door leading into an employee break room, adjoining what turned out to be the primary data center!
Once inside, we were successful in gaining access to pretty much the entire facility without being challenged again by Chad.
The irony of this cyber horror story is that the client was a security firm and the lack of any semblance of security awareness by their security officer underscores the fact that even security companies are vulnerable to the same tactics & techniques that malicious threat actors utilize, regardless of their target or intentions.” – Todd Salmon, Cybersecurity executive and former CISO
” During a recent Ransomware attack, we noticed threat actors stealing administrative credentials and logging on to security portals to disable EDR products within their environment. They used a weakness and privileged access management to uninstall security agents without the victim’s knowledge, until after the security incident had occurred. These attackers were even responding towards threats in the portal to avoid suspicion. Eventually they locked out the customer from their own security portal and executed Ransomware within the environment taking the company down.” – Josh Nicholson, DeepSeas VP
” One that I remember really vividly, we did some work with an insurance provider a property insurance company and we demonstrated that in the web app they put on the Internet for all their policyholders and their agents to use that it was possible to sign up for a free account, gain access to other people’s information, and then actually act as a not only an agent but actually somebody for the company to create our own claim, approve our own claim and mail ourselves a check. All that happened 5 vulnerabilities we found in the web application.” – Ben Finke, OnDefend CTO
Whether you need a Ransomware readiness assessment or advanced email phishing training, OnDefend can provide any professional service your company may need. Check out a full listing of our services here: Services > OnDefend
Many believe a cybersecurity company is filled with a bunch of people furiously typing while wearing hoodies (not completely untrue) but there is so much more!
We’re introducing you to different employees within the OnDefend company to encourage others to explore a career in cybersecurity.
Name: Ben Finke
Title: CTO, OnDefend
Name: Zac Hardy
Title: Senior Project Manager, OnDefend
Name: Lauren Verno
Title: Vice President of Communications, OnDefend
Name: Chris Freedman
Title: CEO, OnDefend
Name: Billy Steeghs
Title: COO, OnDefend
About OnDefend:
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world threats. From ensuring compliance with industry standards to building out mature security programs our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, please visit OnDefend.com.
