Originally written for RANE Network
Editors’ Note: As many companies increasingly turn to cloud providers to store proprietary and consumer data, these services are becoming attractive targets for threat actors. RANE spoke with expert Ben Finke at OnDefend to evaluate the most prevalent risks faced in the cloud environment and better understand how organizations can best protect their stored data and enhance security in the cloud.
As many companies increasingly turn to cloud providers to store proprietary and consumer data, these services are becoming attractive targets for threat actors. RANE spoke with expert BenFinke at OnDefend to evaluate the most prevalent risks faced in the cloud environment and better understand how organizations can best protect their stored data and enhance security in the cloud.
What is a “cloud” environment and why are organizations transitioning there?
A cloud environment refers to a web-based application or software that is used for particular tasks, such as website management or data storage. Broadly, there are two different types of clouds. Finke explains that “Public cloud is what most people think of when they think of cloud.” Public cloud providers create computing services, such as storage, applications, or “develop-and-deploy” environments, made available on-demand over the public internet. There are many different public providers, such as Amazon Web Services (AWS), Microsoft Azure or Google Cloud, each with its own unique products and offerings. In contrast, a private cloud can be offered over the internet, but it can also be used in a private internal network that is only available to select users rather than the general public. While a private cloud is usually fixed, a public cloud can be scaled to an organization’s preferences and adjusted to fit its needs.
Whether public or private, the primary types of cloud service models are infrastructure-as-a-service, platform-as-a-service and software-as-a-service. Organizations have the option to run an operating system as a whole and manage it as an infrastructure-as-a-service in the cloud, only paying for the resources they use, which provides cost benefits through efficient IT resource management. Platform-asa- service provides a complete platform – including hardware, software and infrastructure – which organizations can use to build and design their own cloud environment by developing, running and managing applications over the internet without the cost and complexity generated by on-premises platforms. However, Finke argues that software-as-a-service, a model that allows users to access software applications over the internet, is the most beneficial option as it requires the least organizational management . It is especially useful because it automatically integrates patches or other security updates for an operating system rather than putting the burden on the organization to manage.
Organizations are increasingly adopting cloud environments for cost savings and flexibility, especially as many companies have moved to remote work following the COVID-19 pandemic. Finke says that one of the main benefits of using the cloud is to save money. Many cloud providers, such as those that offer platform-as-a-service, enable organizations to get rid of most of their on-premises hardware and software, which can be costly and inconvenient to maintain. Additionally, cloud computing offers centralized data security. This means that organizations no longer need to expend resources to maintain on- or off-site data backups because cloud providers centralize data backups in their own data centers. This also minimizes the risks of data being lost due to physical damage, such as flooding or natural disasters. Instead, cloud providers can restore data from copies stored in their cloud storage.
What are the most prevalent risks in the cloud migration process?
As companies increasingly opt for cloud computing environments and shift away from traditional IT infrastructure, it requires a new approach to security. Finke describes this as a “total paradigm shift.” He says that there is a major risk in the fact that old security tools, such as network firewalls, which teams used when everything was held in on-premises data centers, have become irrelevant in many ways. “When we think about it from the old school security side, most of the tools that security teams used 10 years ago just don’t even work on the cloud anymore… and so a lot of the security folks kind of found themselves kind of out of their depth a little bit,” Finke says. Part of this is due to the fact that cloud configuration is largely dependent on coding, which is not a skillset that all IT security professionals have, especially older professionals who previously focused on developing skills for building complex firewalls and endpoint detection and response.
Many IT security experts are operating under a new way of thinking and cloud environments are often misconfigured, meaning they can accidentally leave access open to unauthorized third parties. Finke notes that the “cloud is all about configuration” and it is common for these environments to be misconfigured, even by experts. This is partly due to the abundance of offerings that many cloud providers have, as it is unlikely for an in-house IT professional to know how to properly set up hundreds of different offerings. The wide range of offerings can also lead to confusion about which service an organization uses and how they do or do not interact with each other. Finke says that “the problem is that they’re constantly adding new services into these things,” and they are all different in terms of default settings and configuration requirements. Some services allow organizations to segment how they pay for various services. However, Finke notes that a risk with this is not only that cloud environments are misconfigured but also that IT security professionals may look into which subscriptions an organization runs and be unable to identify which applications they belong to or which department is operating them. This means that if an employee went into the service and turned it off, there is no certainty whether doing so would go unnoticed or if it would cause a considerable disruption to business operations. It also makes it more difficult for IT security teams to inform the correct departments within an organization and respond to an incident if they find an issue within a particular application.
Additionally, default configurations can pose problems for organizations because using the cloud eliminates natural security boundaries that organizations may have previously relied upon, and many are unaware that they have to build these defenses back up since default cloud configurations do not come with the same kind of security measures. Finke states that the cloud is, by definition, accessible by the internet, which means that often the default configuration allows public access to anyone. Organizations need to take specific measures to prevent unauthorized parties from being able to enter the system. This is another consequence of a shift from traditional data centers and on-premises IT infrastructure; prior to the cloud, an organization’s network had a certain level of inherent protection, and access was only granted to those whom organizations explicitly granted permission. Without this kind of built-in security, there are inherent risks that organizations’ systems or information held on cloud servers are left exposed if not properly configured to prevent unwanted access. Finke says that “in the older style of networking where we had everything on-site in a data center, we used network ranges as boundaries, and in the cloud, that kind of doesn’t exist anymore. Everything can talk to everything if you let it…it was really helpful that you just didn’t make networks available to each other, and that instantly protected you, whereas the cloud is set up to automatically talk to each other.” Finke also notes that IT security teams now have to shift their thinking to be “more fine-grained with how they give permissions and roles,” because “in the cloud a lot of times, we do not think of networks as security boundaries; it is more like identity.” This means that organizations need new security frameworks that emphasize identity credentials and authentication more than the built-in security that comes with onpremises infrastructure.
Even once the cloud is properly configured and secured, default settings can still pose risks for organizations if they do not change default credentials. Finke warns that breaches frequently occur due to poor access control, saying that organizations will often use the default credentials and create a database that is automatically accessible over the internet and can be found through a brief online search of open database boards. “That is how a lot of cloud breaches happen. It wasn’t that they broke into something; the data just happened to be there,” Finke says.
Along with unintentionally leaving systems publicly accessible, there are problems with understanding which people in an organization do and do not have access to certain services, even if cloud environments are properly configured. This can lead to overlap or miscommunication surrounding security protocols, ultimately reducing their effectiveness. Finke says he frequently sees companies with on-premises IT security staff following one reporting line but cloud security teams reporting into a different group. The problem here stems from the fact that once an organization begins its cloud transition, it “then has to build a whole new [IT security team] for the cloud, and they never really connect the two.” Though he says this challenge has lessened, it nonetheless presents risks when combined with existing confusion around cloud security protocols and access.
Because of the ambiguity surrounding cloud services and the heightened risks of default settings, organizations will sometimes overcorrect in their security practices, causing delays that might incentivize employees to try to bypass lengthy security procedures. Finke says that in contrast with leaving cloud environments publicly accessible, he also sees “overreaction [in] the other direction where everyone is going to be very deliberate and thoughtful.” He says this can slow people down because “nothing can go [into the cloud] without something like three approvals.” This also contributes to confusion around proper configuration and access controls, as Finke highlights that “another thing we’ll see is that IT security teams will go in and they’ll build all these hard rules about things that have to comply with security standards in order to be created, but then the tools themselves don’t give you good feedback.” In other words, if something is not functioning properly in the cloud, there will often be an error message but no clear instructions as to the root of the issue or how to fix it. Because of this, employees may bypass security protocols to immediately begin working on a project using cloud services. This speaks to one of the benefits of cloud computing software, which is the ease that it offers. However, there is a tradeoff between user-friendliness and security that many providers have yet to sufficiently address. On this topic, Finke says, “what we also observe is that the cloud made it super easy to just put down a credit card and start doing stuff.” He says this has manifested in a phenomenon where “most companies, whether they know it or not, have departments in the organization that got tired of waiting for corporate IT and just went and signed up for something and the next thing you know business data is running outside of the company’s scope.” He says that in this case, “you know for sure the cloud environments are misconfigured because there are not even IT people involved.” In this case, a department may be attempting to move forward but faces obstacles when IT does not approve the request or the request may be outside the organization’s budget. When this happens, company data is potentially put at risk, oftentimes without leadership or IT security’s knowledge.
Finke often encounters another common vulnerability when individuals connect cloud services to other applications, often granting extended permissions without realizing it. He goes on to say that “it used to be that if you were an attacker and you wanted to gain persistent access to somebody’s email, you would convince them to give up credentials or run your payload.” However, these tactics have evolved as organizations increasingly move most of their information onto the cloud and individuals connect cloud services to apps to which they subsequently grant permissions. Finke says, “we see a lot of malicious apps where you only click once to grant it permissions, and it can gain send, receive and read access to your mailbox. And then an attacker never needs to touch your computer again because they can access it all in the cloud.”
How can organizations mitigate these risks?
In order to best protect against these risks, Finke shares some best practices: First, he suggests that organizations implement a plan of action for managing the new environment, including monitoring activity inside the cloud and tying it back to identity. One suggestion he makes is to utilize tagging within the cloud, which can help organizations track which departments use particular services. He also recommends regular reviews using these tags to ensure that aspects of the cloud that an organization is subscribed to are still necessary and in use. This can help avoid unnecessary costs or overlapping services and ensure costs are charged to the correct department.
Organizations can also use this planning process to help balance the tradeoff between user-friendliness and security. Finke recommends that IT teams guide employees through the cloud process, showing them the different offerings and how to implement them safely. He also recommends that IT security teams are involved from the very start of when organizations consider how to incorporate cloud services, saying organizations should “make sure that the IT security function is pushed out and embedded into other groups so that if they go to the cloud, they have somebody who is representing the IT security team in the planning and building stages.” He goes on to explain “it cannot really be centralized,” rather, “security functions should be included within groups that are going to consume the technology so that there is a security person there with them.” This is so that when a group decides to build something within the cloud, an IT security professional monitors the plan that is being created to ensure that it upholds proper security standards.
Finke also recommends that organizations invest in an outside consultant that can utilize third-party tools to validate the true state of their cloud environments. This can help organizations ensure that all data and services in the cloud have been properly secured. However, if organizations choose to bring in third-party validators, they must be sure that they uphold all data privacy commitments and do not inadvertently share client information or any personal information on employees without their knowledge, especially if they are operating in locations where regulations would require them to obtain permission before doing so. Finke notes that firms like OnDefend typically are not granted extensive permissions in the cloud when hired for security consultations, saying, “the good news is that…we don’t have access to any of the data; we only have access to the services they are using in the cloud environment that holds the data.” Thus, organizations must be sure that they are not inadvertently giving permissions to third-party validators and that they have performed due diligence to ensure they are abiding by the relevant legislation and regulations. For example, if an organization maintains any biometric data on a cloud database, such as employee fingerprints, and it operates in a state that regulates how organizations handle such biometric data, it must ensure that this information is not made available to a third-party consulting firm in this process without employee consent. This measure can help organizations avoid potential legal action like fast food chain White Castle, which, as covered in a prior RANE Advisory, is currently facing potential class action damages of up to $17 billion under Illinois’s Biometric Information Privacy Act after sharing employee fingerprints with a third party validator.
About the expert: Ben Finke is a co-founder and CTO of OnDefend. Ben has almost two decades’ worth of experience in cybersecurity, starting as a communication officer in the U.S. Air Force. Over the course of his career, Ben worked with organizations ranging from government agencies to Fortune 500 companies, including being embedded in development teams in SaaS companies, overseeing a red team for testing critical infrastructure systems and running the security practice for a managed security provider. In 2016, Ben Co-founded OnDefend, where he currently serves as the Chief Technology Officer. Ben also is the creator of BlindSpot, a purple team testing automation tool. Ben has a bachelor’s degree in computer science from Florida State University.
OnDefend is a cybersecurity consulting firm based in Jacksonville, Florida, that assists firms in reducing their cyber risk through preventative security testing and consulting services. OnDefend’s information security services include network penetration tests, attack simulation tests, application security tests, vulnerability assessments, incident response readiness, ransomware readiness assessments, compliance consulting and other security consulting services.
OnDefend Media Contact: Lauren Verno, Lauren.verno@ondefend.com
In today’s digital age, cybersecurity is a critical concern for every organization. However, it’s important to understand that cybersecurity is not just a technical issue—it’s a business problem.
Unlike IT issues, which can often be resolved with technical solutions, cybersecurity requires a comprehensive approach that involves understanding, managing, and mitigating risks. This means that we need to constantly evaluate our risk posture, which is always changing due to the dynamic nature of threats and vulnerabilities.
Threats are potential harms that cybercriminals and adversaries can inflict on our organizations. These threats are like the weather, always changing and unpredictable. As business leaders, we need to be aware of the current threat landscape, just as a weather person keeps us informed about potential storms.
Vulnerabilities are weaknesses or exposures in our organization that allow threats to manifest. With our technology environment always evolving, new vulnerabilities can emerge at any time. It’s crucial to stay informed about these vulnerabilities and take necessary actions to address them.
The key to effective cybersecurity management is regular communication. Just as we regularly update our teams about business performance and market trends, we need to keep them informed about our current risk posture. This includes discussing potential threats, vulnerabilities, and the potential impact of a security breach.
Remember, cybersecurity is not a static problem and cannot be addressed with a fixed budget. Like our legal and risk and compliance departments, our cybersecurity budget needs to be flexible to accommodate changes in threats and vulnerabilities throughout the year.
In conclusion, cybersecurity is a business function that requires a proactive approach to risk management. It’s not just about buying firewalls or other security devices—it’s about understanding and managing risks, communicating regularly with our teams, and being prepared to adapt to changes. Let’s embrace this approach to ensure the security of our organizations in the digital age.
About OnDefend
OnDefend empowers the information security industry through its cutting-edge technological innovations and battle tested professional services team. By solving the problems that the cyber security industry has not solved, OnDefend has become a critical partner of security service firms and corporations throughout the US and around the world. Whether it’s their next generation SaaS offerings of BlindSPOT and Confirm4Me or their seasoned security team leveraged by partners to meet market service demand, OnDefend has enabled cyber security firms to extend their capacities and corporations to secure their future. To learn more, visit ondefend.com.
It’s already May, and I know I’m not alone when thinking, “how did we get here? ” It’s been a hot minute since we last caught up, and there’s a lot to go over. From our threat-informed pentest webinar, BlindSPOT updates, and OnDefend in the news, let’s get started.
Threat-Informed Pentest Webinar Recap

Whether you’re new to OnDefend or have been around for a while, you’ve likely heard the phrase “traditional pentesting is no longer enough.” Budgets are thinner than ever, and hackers are as skilled as ever, which means companies need to be tactical about their investments. Traditional pentesting is necessary, but focusing those efforts on industry-specific threat actors is what we believe will give companies that edge. Go ahead and check it out for yourself; the full webinar recording is up right now.
Watch here: Threat-Informed Pentesting: Preparing for Threats Targeting Your Industry
Better Together
We’re off the ball in the game! OnDefend CEO Chris Freedman and CTO Ben Finke met with our partner DeepSeas in Cincinnati last month. OnDefend co-sponsored a night out to the Cincinnati Reds game, where we got to discuss how BlindSPOT enables Deepseas customers with breach & attack simulation capabilities.
If you’re ready to dive deeper into BAS, Deepseas VP Josh Nicholson & OnDefend CTO Ben Finke explore breach & attack simulations on “Cyber Control Testing: New Purple Teaming Revolution.” You can listen to the full podcast on Cyber Security America here: Cyber Control Testing: New Purple Teaming Revolution
——
Supply chain attacks might be one of the most elusive, engaging, and relevant cyber-attacks to talk about. This is why we obviously had to jump at the chance when ITProTV reached out to talk all things supply-chain. Check out CTO Ben Finke’s conversation with ITProTV’s Daniel Lowrie here: ITPro LIVE with Daniel Lowrie and Ben Finke
OnDefend In The News
A huge congratulations are in order for OnDefend CTO, Ben Finke being named one of Jacksonville’s 2023 Ultimate Tech Leaders!
“ The past few years have been a challenging time for those that are tasked with guiding their organizations as they implement new solutions, take advantage of new opportunities, and figure out a path to the future. The work these leaders do is vital, both to their organizations and for the growth of the local economy.” – Jacksonville Business Journal
First Coast Inno – Here are Jacksonville’s 2023 Ultimate Tech Leaders (bizjournals.com)
—
A not-so-elaborate cyber-attack could cost taxpayers 1.4 million. OnDefend CEO Chris Freedman spoke with Fox13 Tampa Bay about how scammers were able to pull off the attack and why it’s unlikely the money will be recovered.
Manatee County falls victim to cybercrime that could cost taxpayers $1.4 million (fox13news.com)
—
You’ve likely heard the phrase, “If the app is free, you are the product being sold.” While we never recommend giving away sensitive information, we realize that sometimes giving your name or even email address is inevitable when signing up for an app. But, when WJXT News4Jax reached out about a new app that seemed to ask for everything under the sun, CTO Ben Finke has a warning for the viewers at home.
A warning from cyber security experts about the TEMU app (news4jax.com)
—
The White House Cybersecurity Directive was released earlier this year. As a cybersecurity company, we are genuinely excited and optimistic about the plan, but actions speak louder than words. The main question in the end is, will it make a difference? Check out our full take on Forbes.
Other News featuring OnDefend:
16 Effective Strategies To Collect Feedback On New Internal Tech (forbes.com)
14 Specialized Tech Leadership Roles That May Emerge In The Next Decade (forbes.com)
16 Business And Consumer Tech Tools Experts Say Everyone Will Be Using Soon (forbes.com)
16 Leaders’ Tips To Help Tech Pros Better Communicate With Non-Tech Experts (forbes.com)
BlindSPOT
I could go on for days about why BlindSPOT is one of the best BAS tools in the market today. It’s a one-stop shop tool that allows partners to simulate cyber-attacks, visualize a company’s security control “blind spots,” and remove security risks. One of the many reasons Plextrac and Market Research Access Services recently recognized the tool for its innovation.
30+ of the Most Popular Penetration Testing Tools in 2023 – PlexTrac
And now a word from the BlindSPOT guru himself, CTO Ben Finke…
Hello! Tons of things happening in the BlindSPOT world, but let’s dive into a few things that you should know:
Alert Validation in Beta
We spend a lot of time using BlindSPOT to test our defenses and build alerts using our security tool data that help us find malicious activity. But, how do we make sure that detection pipeline works? Enter Alert Validation!
Alert Validation leverages the BlindSPOT capabilities you already know and love to generate real activity on an endpoint, and then BlindSPOT connects to your security tools. We check to make sure 1) the log data shows up as expected, 2) the alert analytic fires as expected, and 3) it all happened within a timeframe that is acceptable to you. This whole process is completed automated, with notifications for a failure at any step. Its uptime testing for your detection pipeline! Available now for Microsoft Defender for Endpoint and Azure Sentinel, with more security tools to be added in the future!
Automated Plextrac Runbooks V2 Integration
We’re big fans of what the team at Plextrac is doing, and we’re pleased to release our full integration with the Plextrac Runbooks V2 feature. Simply, connect BlindSPOT to your Plextrac instance, and then we can push any completed BlindSPOT campaign into Runbooks, even if you don’t have the Test Plan built for it yet (we’ll take care that for you!). No need to worry about exporting and importing files, it’s a simple button in BlindSPOT to send the campaign results into your Plextrac instance!
Updated Agent and Payload Builder
We’ve rebuilt our Unified Payload Builder, allowing us to begin chaining additional transformation capabilities for agents and payloads. We’ve already added an automated obfuscation feature for both payloads and agents, and we’ve got a lot more improvements on the way (packed PE files, DLL unhooking, and more!).
Anybody else feel like we just scratched the surface? That’s because we did. Stay tuned for this bi-monthly newsletter, for all of OnDefend’s latest and greatest.
If you want to stay in the loop about what’s happening at OnDefend, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
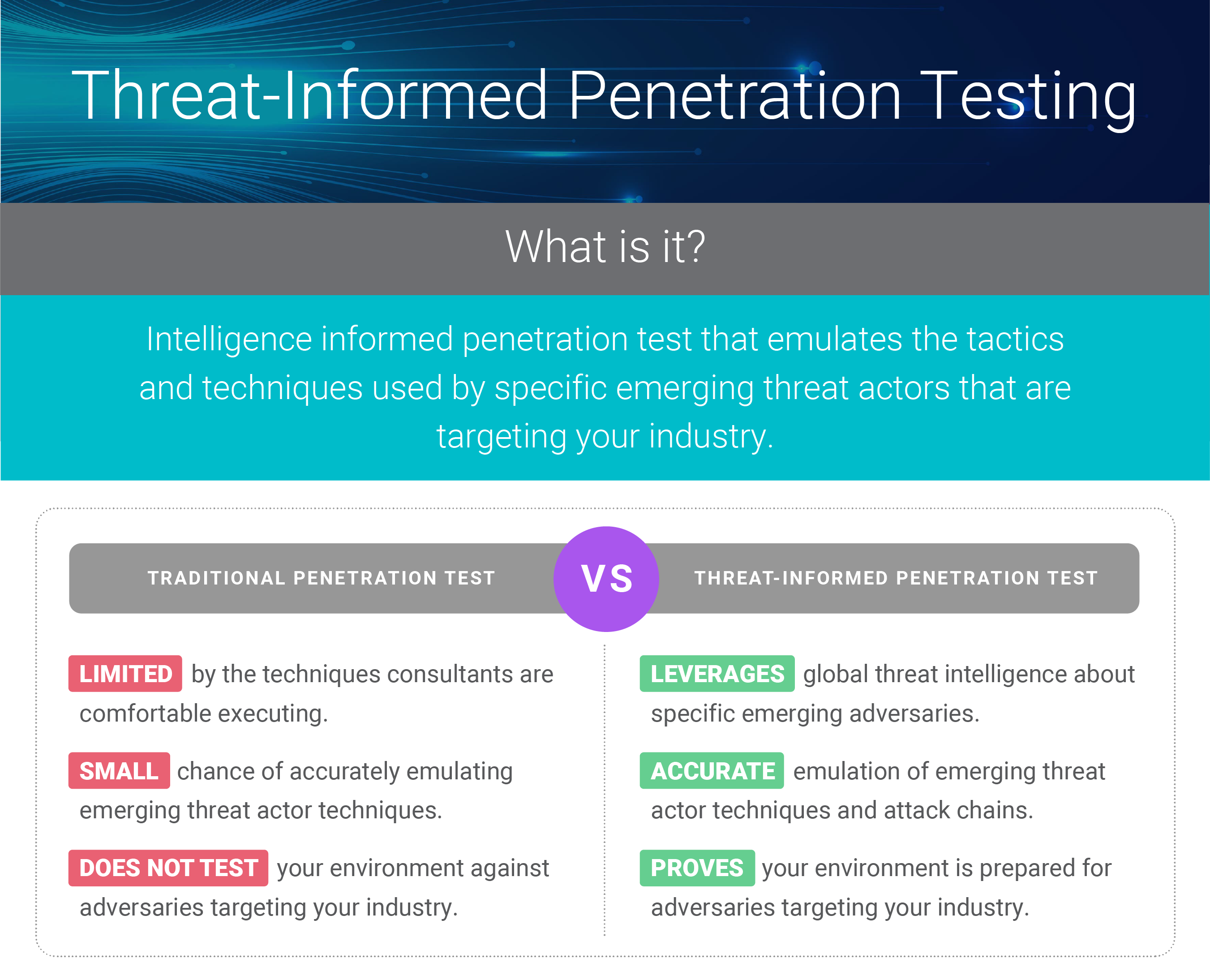
Traditional pentesting is no longer enough. Leadership and board of directors hear about the latest cyber breaches and question if their security team is prepared for that specific threat actor targeting their industry. Not having a definitive answer is no longer acceptable.
The best way to win the war against these cyber criminals is by testing your organizations defenses against real-world threats. There’s no better way to do that then by emulating the tactics and techniques of these known adversaries on your real production network. Threat-informed pentesting (TIP) is the first step to covering these defenses.
TIP leverages global threat intelligence about specific emerging adversaries and one-to one tests your environment against their exact tactics and techniques. TIP can be catered to your specific environment to demonstrate your ability to detect and respond to entire attack chains. TIP is a versatile offering that can be added on to an existing pentest or as a stand-alone exercise to meet a company’s budget and security posture. This isn’t going to be a traditional year, don’t limit your company to a traditional pentest.
Join OnDefend CEO Chris Freedman and CTO Ben Finke for an expert crash-course on threat-informed pentesting. Throughout the cast — moderated by Emmy award winner Lauren Verno — you’ll learn:
- What is threat-informed pentesting and its benefits compared to traditional pentesting techniques
- How OnDefend executes TIP scenarios to emulate real-world threats, and how this approach can improve your organization’s security posture
- Engagement options for threat-informed pentesting, and how to determine the best approach for your organization
- How to answer leadership’s questions about threat actors targeting a specific industry, and how to prepare your organization for potential threats
- Discover BlindSPOT technology and how it can help implement TIP in a continuous assessment strategy, providing ongoing visibility into your organization’s security posture
You can watch the full webinar here:
Speakers:
Ben Finke, OnDefend Co-Founder/CTO
Ben has almost 2 decades worth of experience in cybersecurity, starting as a communication officer in the U.S. Air Force. Over the course of his career Ben worked with organizations ranging from government agencies to fortune 500 companies including, being embedded in development teams in SaaS companies, overseeing a red team for testing critical infrastructure systems, and running the security practice for a managed security provider. In 2016, Ben Co-founded OnDefend where he currently serves as the Chief Technology Officer. Ben also is the creator of BlindSpot, a purple team testing automation tool. Ben has a bachelor’s degree in computer science from Florida State University.
Chris Freedman, Co-Founder/CEO
Chris is a highly accomplished business leader with a diverse background in diplomacy, business, and philanthropy. Chris began his career serving as a diplomat with the Atlantic Treaty Association and founding a regional real-estate development firm. He continued his career by founding and managing various corporations in the U.S. including, MyBenefitsLab, a national online provider of diagnostic testing with the nation’s largest laboratories and national physician’s network. In 2016, Chris Co-Founded OnDefend, an international cyber security firm, where he currently serves as the CEO. Civically, Chris has also served several charitable organizations, including Best Buddies Jacksonville and the American Red Cross of Northeast Florida. Chris graduated with the highest honors from the University of Florida.
About OnDefend
OnDefend empowers the information security industry through its cutting-edge technological innovations and battle tested professional services team. By solving the problems that the cyber security industry has not solved, OnDefend has become a critical partner of security service firms and corporations throughout the US and around the world. Whether it’s their next generation SaaS offerings of BlindSPOT and Confirm4Me or their seasoned security team leveraged by partners to meet market service demand, OnDefend has enabled cyber security firms to extend their capacities and corporations to secure their future.
Cybercriminals are always on the lookout for vulnerabilities to exploit, and no industry is safe from their attacks.
This is why it’s crucial for organizations to stay one step ahead by proactively identifying and addressing potential security risks before they can be exploited by malicious actors. One effective way to do this? Threat-informed pentesting – a comprehensive security testing approach that focuses on identifying and mitigating real-world threats that specifically target your industry.
It’s a proactive approach to cybersecurity that helps you sleep better at night knowing you’re taking the necessary steps to protect your organization from cyber attacks.
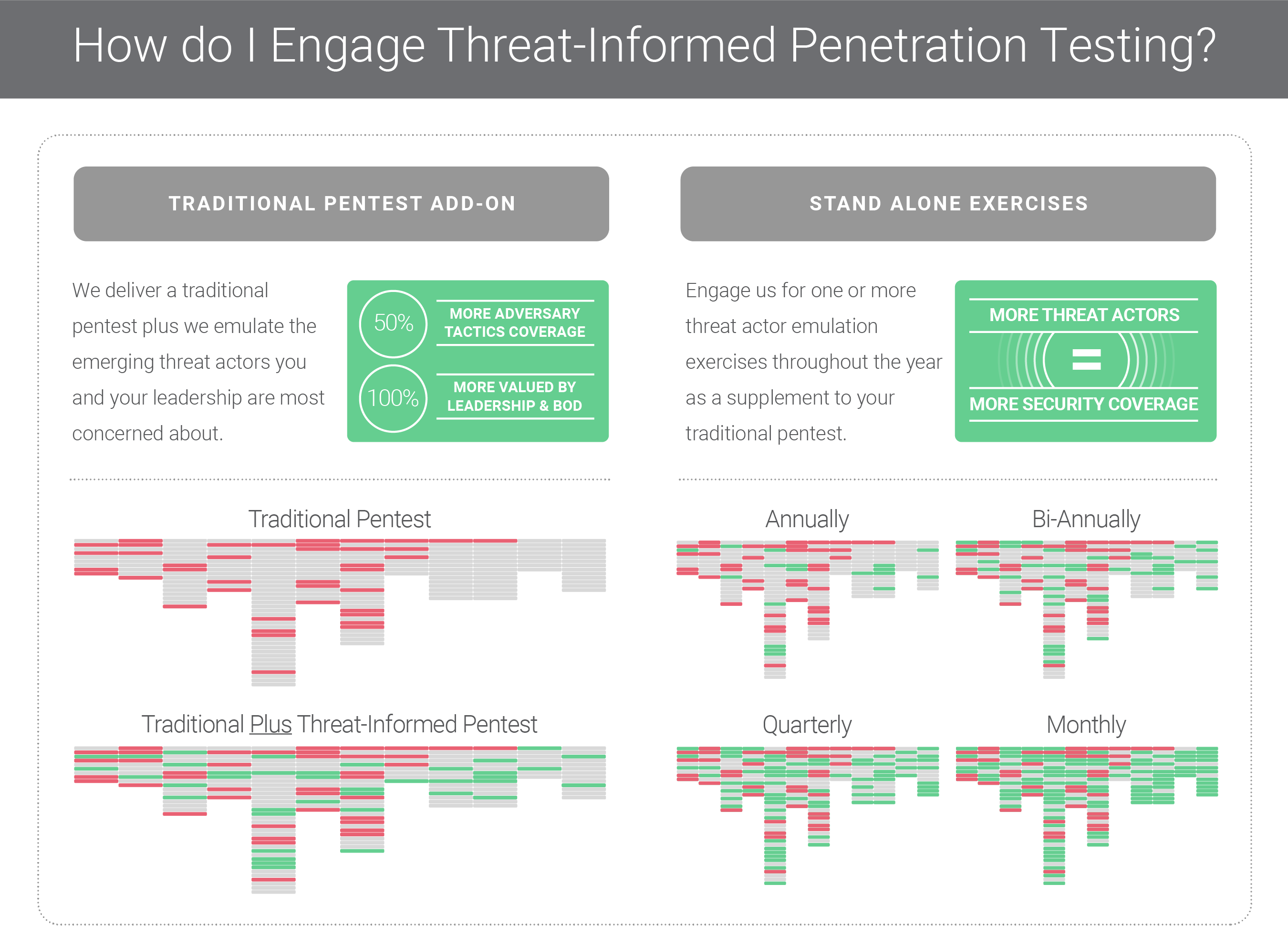
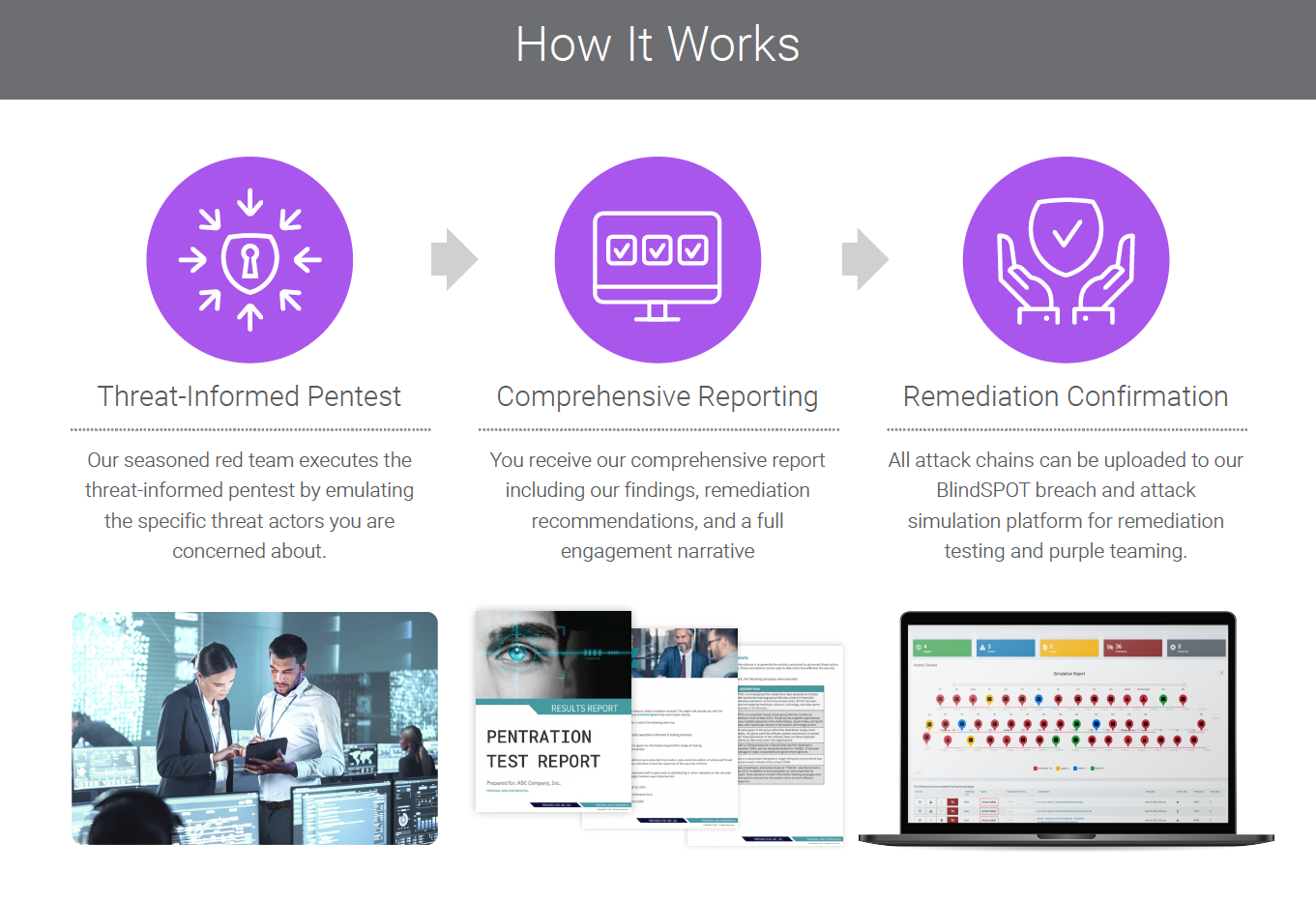
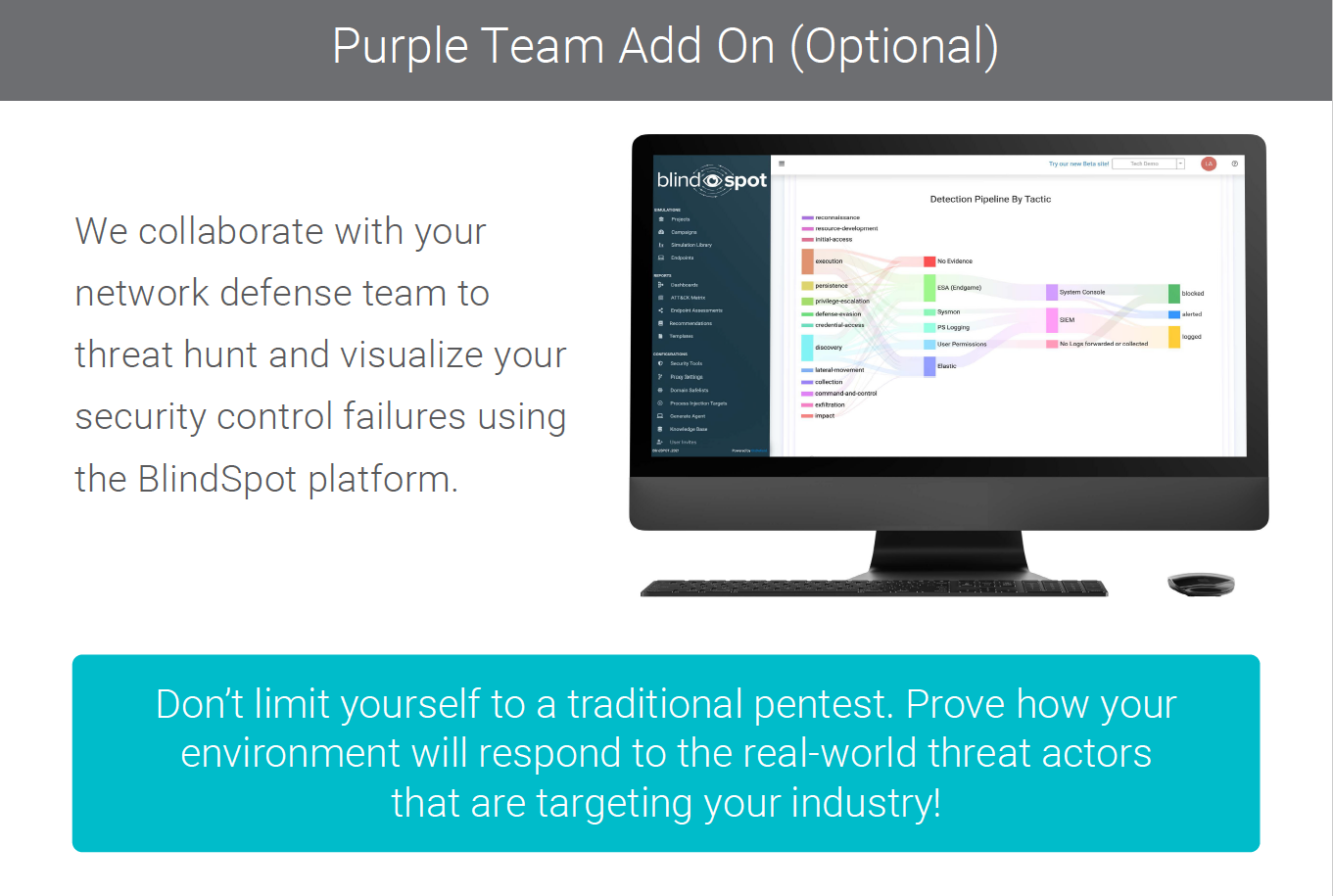 This isn’t going to be a traditional year, don’t limit yourself to a traditional pentest. Contact OnDefend today to learn more about how threat-informed pentesting can help protect your organization.
This isn’t going to be a traditional year, don’t limit yourself to a traditional pentest. Contact OnDefend today to learn more about how threat-informed pentesting can help protect your organization.
Our experienced team of cybersecurity experts can provide you with a customized approach to threat-informed pentesting that fits your specific industry and organization.
OnDefend Company Newsletter: Creating a Culture of Understanding and Solutions
Have you ever heard the phrase, the days are long but the months are short? That is the only way I know how to describe the first few months of 2023. Between launching a new set of featured services, rolling out more BlindSPOT updates, and keeping up with the news, it has been a rollercoaster for our company. Which is why we are launching this newsletter, to keep everyone up to date with what’s going on with OnDefend and the latest cybersecurity trends. So, before I bore you to death with anymore long winded metaphors, let’s go ahead and get started.
Better Together

OnDefend is proud to call ourselves a partner first company. While we can’t name every company who private-labels our services we are excited to announce some recent partnerships, including PlexTrac. Check out our most recent webinar with PlexTrac CEO Dan Decloss & OnDefend CTO Ben Finke.
Learn More: OnDefend Integrates with PlexTrac to Deliver Threat-Informed Pentest
Threat- Informed Pentest
Are you limiting yourself to a traditional pentest? Traditional pentests are great but they don’t always answer leaderships question “are we prepared for this specific threat actor that we read about in the news? TIP solves that problem.
Learn More: Threat-Informed Pentesting: What Is It?
OnDefend In The News

It is always an honor to be recognized for achievements within your community. From being recognized for growth in the tech sector to Inno On Fire, there has been plenty of reasons to celebrate our companies success. Personally, I love the fact that one publication used our CEO’s picture and made him look like a character out of the hunger games.
Learn More:
Flurry of activity in 2022 has Jax’s tech sector prepared for coming year
2022 Class of Fast 50: OnDefend
Bylines By Ben

We are proud to announce our CTO Ben Finke was accepted into the Forbes Technology Council. What does this mean? Forbes accepts members based on their background, experience, and achievements within tech. Ben was accepted into this elite group of leaders and innovators to share advice and write meaningful content which is shared across Forbes’s platform. Check out his first article, breaking down the basics of a supply chain attack.
Learn More:
You Don’t Need To Be In IT TO Understand A Supply Chain Hack (Forbes)
15 Expert-Recommended Ways For Consumers To Better Protect Their Privacy Online (Forbes)
13 Tech Industry Leaders Discuss Their Top Internal Initiatives For 2023 (Forbes)
16 Tech Leaders’ Tips For Managing The Day-To-Day Work Grind (Forbes)
CMMC Deadline
DoD contractors are required to become CMMC complaint by the end of May, but this process won’t happen over night. Our experts say your company needs 60-90 days to complete all requirements. Aka let us help you now!
Learn More: CMMC 2.0 Basics: The 101 of Getting Compliant
BlindSPOT Updates

We are constantly working on new BlindSPOT features to make the platform as user friendly as possible. We believe in making these changes as easy and understandable as possible, so with that being said here are the latest BlindSPOT updates for 2023, so far…
BlindSPOT Updates: January Edition
Anybody else feel like we just scratched the surface? That’s because we did. Stay tuned for this bi-monthly newsletter, for all of OnDefends latest and greatest. In the meantime if you have any questions feel free to reach out at contact@ondefend.com.
JACKSONVILLE, FLORIDA and BOISE, IDAHO — February 15, 2023 — OnDefend, a critical partner of security service firms and corporations throughout the US and around the world, using the power of PlexTrac, the premier cybersecurity reporting and collaboration platform, presents a groundbreaking security offering to customers and partners through threat-informed penetration testing (TIP).
TIP is the next generation in penetration testing that leverages global threat intelligence about specific emerging adversaries targeting your industry to provide valuable insight on how your environment will respond. TIP safely tests the exact tactics and techniques of the threats your leadership and organization are concerned about.
Through an in-depth API integration, OnDefend can now offer customers their automated breach and attack simulation (BAS) solution, BlindSPOT, with seamless remediation management and retesting through PlexTrac Runbooks. OnDefend’s BlindSPOT enables you to execute attack activity on your client’s production network environments for more consistent and real-world practice against adversaries. PlexTrac’s Runbooks supports the planning, execution, reporting, and remediation tracking of your red teaming, purple teaming, or adversary emulation activities.
Using OnDefend and PlexTrac together make TIP actionable for your team by
- Leveraging OnDefend’s seasoned red team to emulate the specific threats actors of your company’s choosing
- Automatically delivering results via API to PlexTrac for comprehensive reporting and remediation management
- Performing remediation retesting via PlexTrac Runbooks, selecting BlindSPOT, OnDefend’s Breach and Attack Simulation solution, to guide the testing
“The partnership between OnDefend and PlexTrac provides companies invaluable insight into whether their security network will withstand an attack from an emerging adversary using threat-informed penetration testing. In addition, organizations need to know their controls will work throughout the year, which is where PlexTrac and OnDefend’s proprietary tools — BlindSpot and Runbooks respectively — will help leadership of those companies sleep well at night knowing their security tools work,” said OnDefend CEO Chris Freedman.
“We are excited to promote this deep integration and partner with OnDefend to help them make threat-informed penetration testing accessible and valuable for any security team,” said PlexTrac Founder and CEO Dan DeCloss. “Using threat intelligence to guide your offensive testing is a great way to become more proactive and move toward a continuous assessment strategy.”
Watch an on-demand webinar from OnDefend and PlexTrac to learn more about the value of threat-informed pentesting and see the BlindSPOT/Runbooks integration in action.
Watch Threat-Informed Pentesting: The First Step to Continuous Assessment:
About OnDefend
OnDefend empowers the information security industry through its cutting-edge technological innovations and battle tested professional services team. By solving the problems that the cyber security industry has not solved, OnDefend has become a critical partner of security service firms and corporations throughout the US and around the world. Whether it’s their next generation SaaS offerings of BlindSPOT and Confirm4Me or their seasoned security team leveraged by partners to meet market service demand, OnDefend has enabled cyber security firms to extend their capacities and corporations to secure their future. To learn more, visit ondefend.com.
About PlexTrac
PlexTrac, Inc. is the premier penetration test reporting and proactive cybersecurity management platform driven by a mission to help teams win the right cybersecurity battles. PlexTrac makes security data aggregation, red and blue team reporting, purple team collaboration, and remediation tracking more effective and efficient so security teams can become more proactive and demonstrably improve security posture. To learn more, visit plextrac.com.
Originally written for Forbes.
Once you understand a supply chain attack, it’s hard not to question whether you might have already been a part of one. We are all familiar with direct cyberattacks, which is why your company’s IT department consistently warns of phishing emails. The attackers need to find a way inside. But what if they were able to find a way in where their malware got brought in by the target themselves? Welcome to the world of supply chain attacks.
Supply chains are a fact of life for every aspect of any IT system and enterprise. Most of the software that we run was made by another company. The hardware it runs on is manufactured by hundreds of different vendors and, in many cases, is hosted and managed by a third party. Even the software we build internally relies heavily on libraries and other software components that are simply imported from other sources. An attacker who can modify anything in the upstream supply chains in any of these scenarios would find themselves already inside hundreds or thousands of environments without having to exert any effort. Scary right?
I’ll give you an example. In 2020, attackers targeted many businesses and organizations, including one notable attack involving SolarWinds. You can read more about this attack via extensive reporting from several media outlets, including Forbes and The Washington Post. A company called Kaseya, which makes another remote monitoring and management (RMM) tool, had something similar occur.
If you’re not in cybersecurity or IT, don’t worry if you don’t completely understand the significance of what could happen in a supply chain attack. Hackers can break into the internal systems used by an organization and add their own malicious code to the real software. When a vendor like this then updates the software used by their customers, they unknowingly send out the malicious code with it.
In some cases of supply chain attacks, thousands, if not tens of thousands, of companies are affected. That’s thousands of separate companies that these attackers are able to sneak their malware into by simply attacking a single organization. Once those companies install an update (which is what security wonks like me are constantly telling folks to do!), the attackers can gain access to those companies’ information technology systems and are able to install even more malware. Think of it as a trickle-down effect. The really scary part is that hacks like these are often undetected for months, gaining access to both government and private entities.
These hacks can be stealthy, where they avoid detection for months, or the attacker can choose to take more noticeable actions with it, perhaps by delivering ransomware. In the case of ransomware, the impact is obvious, but the source is elusive, as these tools are often seen as the defense, not the attack vector.
The impacts of a supply chain attack vary from data breaches to malware installation and financial loss. Detecting this malicious code can be incredibly difficult. And removing the malicious code can be even more challenging, if not impossible.
Attribution is incredibly difficult in these cases, but given the rewards available to a successful operation, it is believed that nation-states and organized cybercrime groups are actively pursuing supply chain attacks to further their own interests.
If only we could go back to only worrying about those phishing emails.
So, what can you do to reduce your own exposure to a supply chain attack? Supply chain attacks may be the most challenging cybersecurity risks we are going to face. But here’s a start.
- Baseline what normal behavior is. “Should our server monitoring software be making connections to the internet?”
- Avoid the temptation to omit any activity executed by “trusted” applications from your threat detection process. That software should behave reliably. You must understand normal to understand abnormal.
- Use software that receives third-party security verification and ensure the vendor can provide up-to-date information like a software bill of materials
- Build an incident response playbook for what to do if one of your trusted utilities is suddenly unavailable to you, especially during a security incident investigation.
- Supply chain attacks are the initial access for these attackers. Plan on catching them when they start moving to the next phase of their operation.
We’ve just scratched the surface of what you can do about supply chain attacks. Stay tuned for the next chapter in our supply chain series, including a deeper dive into what companies can do to block these hackers and an answer to the question, “Will cybersecurity ever be solved?”
Read the original article here: You Don’t Need To Be In IT To Understand A Supply Chain Hack (forbes.com)
OnDefend Media Contact: Lauren Verno, Lauren.verno@ondefend.com
Cybersecurity Maturity Model Certification is a U.S. Department of Defense (DoD) program that applies to Defense Industrial Base (DIB) contractors. It is collective standard and new certification model to ensure DoD contractors protect sensitive unclassified information.
In layman’s terms the government is setting ground rules when it comes to the cybersecurity of organizations they work with.
Why do companies need to take meeting CMMC guidelines seriously? To start, its government mandated and it’s not going away. If anything, CMMC may apply to all non-DoD government contractors in the future. CMMC is not just is not just a bunch of paperwork, such as policies and procedures, the purpose of meeting these standards is to make sure your organizations security tools are working. Finally, CMMC is not something to ignore; it will affect your future in winning bids.
The Basics:
The Department of Defense (DoD) released the CMMC framework to reduce the risk posed by cyber criminals. This framework is set to assess and improve the cybersecurity posture of an astounding 300,000 companies that contribute to DoD systems, networks, installations, capabilities and services.
It is also intended to increase the security of DoD’s supply chain by promoting compliance from all companies that are part of it.
Yet, a recent survey revealed 87% of DoD contractors don’t meet the basic cybersecurity requirements. (Tech.co)
According to the Department of Defense, The CMMC 2.0 program has three key features:
- Tiered Model: CMMC requires that companies entrusted with national security information implement cybersecurity standards at progressively advanced levels, depending on the type and sensitivity of the information. The program also sets forward the process for requiring protection of information that is flowed down to subcontractors
- Assessment Requirement: CMMC assessments allow the Department to verify the implementation of clear cybersecurity standards.
- Implementation through Contracts: Once CMMC is fully implemented, certain DoD contractors that handle sensitive unclassified DoD information will be required to achieve a particular CMMC level as a condition of contract award.
National Industry of Standards and Technology NIST
It provides a comprehensive mapping system that connects specific controls and processes associated with various cybersecurity standards to three distinct maturity models, ranging from basic (Level 1) cyber hygiene to advanced (Level 3).
Some examples of these controls are:
- Do you limit access to authorized users only?
- Do you perform Security Awareness Training for all your users?
- Do you retain and monitor system logs?
- Do you have and exercise an Incident Response plan?
- Do you perform recurring Security Assessments
- Do you limit physical access and monitor the facilities?
- And more…
Drafting policies and procedures, creating system documentation, and implementing technical solutions to close the gaps is a time-consuming and costly process. Cybersecurity consulting firms can help you understand exactly what to implement without going overboard and tailor the implementation to your requirements, needs, and budget.
All DoD contractors and Subcontractors are required to achieve within their level of CMMC 2.0 by end of May with CMMC guidelines and requirements on DoD bids this July.
Find out how OnDefend can assist your company to meet CMMC compliance. Get started today contact@ondefend.com
Want to learn more? https://ondefend.com/blindspot/