Reimagining Ransomware Defense: Revealing and Removing the Hidden Risks of Security Control Failures
Are Your Security Controls Working Right Now? Let’s Prove It.
Inspired by real-world conversations between Baptist Health CISO James Case and OnDefend CEO Chris Freedman, Ransomware Defense Validation (RDV) was built as a proactive solution tailored to the unique challenges healthcare systems face every day.
When asked if their security controls are working properly and effective, we’ve often heard many security leaders respond, “Yes we think so… but there’s no good way to regularly validate it.” Without the right tools to continuously test and validate these security defenses, organizations are relying on the bad guys to do the testing for them.
Join us for this webinar where James and Chris will:
- Dive into the ransomware pandemic from a CISO’s perspective.
- Reveal how & why prevention, detection & response security control failures occur.
- Explore how Ransomware Defense Validation was innovated to solve this problem.
- Demonstrate real results & outcomes within a healthcare system implementing RDV
- Share actionable steps to prove your security controls work and provide a real-world ROI
Stop hoping your controls are working, proactively prove they are.
Download the case study here: Case Study: Prominent Healthcare System Implements Ransomware Defense Validation to Safeguard Patient Safety and Data Security
Watch the full webinar here:
Speakers:
James Case: James Case has worked in IT within the health care industry for nearly 30 years. His tenure at Baptist Health began in 2005 when he served as a senior product manager for two years. Throughout his career, he has held information security roles both within Baptist Health and outside of the organization.
In 2021, he assumed his current senior leadership position, where he is responsible for leading day-to-day operations for information security, including incident response, the education of team members, vulnerability management, risk assessment and intrusion prevention. He is also tasked with protecting clinical information and the confidentiality of patients, as well as with delivering an effective cybersecurity program.
Chris Freedman: Chris Freedman, Co-Founder and CEO at OnDefend – With a career spanning over two decades in business leadership and cybersecurity innovation, Chris leads OnDefend’s strategic vision and go-to-market strategies. His efforts have helped establish OnDefend as a trusted partner in the global cybersecurity industry, including the development of BlindSPOT, a cutting-edge Breach and Attack Simulation (BAS) platform designed to enhance clients’ security posture through proactive validation and testing. – Visit Chris’s LinkedIn Profile Here – Chris also serves as an active member of several charitable organizations, including Best Buddies and American Red Cross reflecting his commitment to both business excellence and community engagement.
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world threats. From ensuring compliance with industry standards to building out mature security programs our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. OnDefend.com
What We Learned from Nine CISOs on Ransomware Defense Strategies
Ransomware continues to be one of the most devastating and expensive cybersecurity threats. Global ransomware damages are projected to reach billions annually1, leaving Chief Information Security Officers (CISOs) and security leaders under increasing pressure to ensure their organizations are prepared. Despite sophisticated tools and strategies, blind spots in detection and response capabilities can leave even the most mature security programs vulnerable.
The OnDefend team had the rare opportunity to be a fly on the wall as nine healthcare CISOs discussed their security programs. As a group, we identified their top ransomware challenges and collaborated on strategies for how tech vendors and security leaders can work together to address these issues.
From misconfigured tools to ineffective threat responses, blind spots in ransomware defense can have devastating consequences. This blog gives you a behind the scenes look at the top challenges these CISOs face in ransomware defense and the actionable insights discussed to overcome them.
1. Operational Assurance: Ensuring Security Controls Work as Intended
The Challenge
Security leaders face the critical challenge of ensuring that detection and response tools, such as Secure Email Gateway (SEG), Endpoint Detection and Response (EDR), Network Detection and Response (NDR), and Security Information and Event Management (SIEM), are fully optimized and functioning as intended. Without operational assurance, misconfigurations, policy drift, and untested updates can leave organizations vulnerable to ransomware threats and other cyber risks.
When asked “How do you test and verify that your controls are functioning right now?”
One CISO responded, ” I don’t have enough of a team to be able to test, so I’m not aware whether these things are working correctly.”
Well, another CISO responded, ” the bad guys are technically testing us every day, right?”
But, they all agreed, they could do more.
Why It Matters
Misconfigurations and blind spots caused by outdated policies, incorrect thresholds, software updates, integration failures between tools, or unintended changes leave critical gaps that allow threat actors to operate undetected. This leads to increased dwell times, heightened risk exposure, and the potential for significant operational disruptions. Additionally, misconfigured controls can generate excessive false positives or negatives, overwhelming security teams and leading to missed detections of legitimate threats.
The Solution
CISOs and security leaders can take several proactive measures to ensure that security controls function as intended and deliver the protection their organization needs.
- Establish a Continuous Validation Program: Regularly (monthly or quarterly) test and validate security controls using tools like Breach and Attack Simulation (BAS) or managed services like OnDefend’s Ransomware Defense Validation (RDV) to ensure they are properly configured and capable of detecting and responding to real-world threats.
- Regularly Audit and Tune Configurations: Conduct routine audits of rules, thresholds, and integrations to ensure configurations are up-to-date and aligned with evolving threat landscapes. Validate that patches, updates, or policy changes do not inadvertently create vulnerabilities.
- Foster Cross-Departmental Collaboration: Collaborate with IT, DevOps, and other business units to ensure security measures are embedded into workflows and aligned with operational needs. Work closely with procurement teams to assess vendor capabilities and meet SLA commitments.
- Develop Incident Response Playbooks: Create detailed playbooks that include validated escalation paths, response protocols, and tool configurations to effectively handle various incident types. Test these playbooks through simulated exercises to ensure they work as intended during real incidents.
- Promote a Security-First Culture: Train internal teams and stakeholders on the importance of proper configurations and adherence to security protocols. Encourage a culture of vigilance where security practices are seen as critical to the organization’s success.
By taking these steps and working closely with trusted security vendors, CISOs can build a proactive, resilient cybersecurity posture that ensures security controls function as intended and evolve to meet new and emerging threats.
2. Quantifying Third-Party Vendor Efficacy: Holding Vendors Accountable
The Challenge
Managed Security Service Providers (MSSPs) and Managed Detection and Response (MDR) solutions are critical components of a ransomware defense strategy. However, these providers often fail to meet Service Level Agreement (SLA) requirements due to:
- Resource constraints
- Skill gaps
- Outdated response protocols.
5 in 10 threat response assessments result in a notification response delay or failure – (Data Collected from OnDefend Services between 2020-2024)
Why It Matters
Measuring vendor performance can be difficult due to a lack of transparency, inconsistent reporting, and limited actionable data on real-world incident response capabilities. Without clear metrics to evaluate whether vendors meet SLA commitments or effectively mitigate threats, organizations risk extended dwell times, unaddressed vulnerabilities, and reduced resilience to cyberattacks. The inability to quantify vendor efficacy leaves security leaders in the dark, undermining confidence in their security posture and complicating vendor selection, retention, or replacement decisions.
The Solution
- Regularly evaluate MDR, NDR, MSSP service providers, and other security vendors to ensure they meet SLA commitments and perform as expected. Use metrics such as Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) to measure vendor effectiveness and identify areas for improvement.
- Conduct regular, controlled threat detection and response exercises to measure real-world SLAs and detection and response times.
- Simulate real-world ransomware incidents to evaluate how quickly vendors detect, alert, and respond to threats.
Use these findings to hold vendors accountable or identify alternative solutions that deliver better performance.
3. Demonstrating Preparedness to Executives and Boards
The Challenge
CISOs face increasing pressure to assure executives and boards that their organizations are prepared to defend against and respond to ransomware and other cyber threats. However, demonstrating this preparedness is often hampered by the complexity of translating technical security measures into business-relevant insights.
Why It Matters
Without clear, quantifiable metrics—such as MTTD and MTTR—and tangible evidence of operational assurance, conveying the effectiveness of security controls and demonstrating cyber resilience becomes difficult. This lack of transparency can lead to uncertainty among stakeholders and diminished confidence in the organization’s cybersecurity posture.
The Solution
- Beyond traditional penetration testing: Penetration testing lacks real-world threat simulation, only provides a snapshot of vulnerabilities at a specific point in time and does not account for ongoing changes in the environment. Penetration testing reports are often technical and detail-oriented, making it challenging for CISOs to translate findings into business-relevant insights or quantifiable metrics that resonate with executives and boards. Invest in BAS tools or a managed service like Ransomware Defense Validation (RDV) to provide ongoing assurance.
- Provide Stakeholder Transparency: Communicate the status and effectiveness of security controls to executives and board members using data-driven insights and provide tangible results that stakeholders can understand. Regularly demonstrate how investments in security controls and continuous validation reduce risk and enhance organizational resilience.
By providing measurable metrics, testing real-world scenarios, and proving that security controls and processes are both resilient and effective, CISOs can ensure stakeholders that their cybersecurity efforts support operational continuity and organizational resilience.
4. Proving ROI on Cybersecurity Investments
The Challenge
CISOs are under constant pressure to secure budgets and demonstrate the value of their cybersecurity investments. However, proving ROI in cybersecurity is uniquely challenging because success is often measured by what doesn’t happen—prevented breaches, mitigated risks, and avoided costs.
Why It Matters
Without quantifiable metrics like MTTD or MTTR, and tangible proof that tools and services are functioning as intended, it becomes difficult to communicate the effectiveness of security investments to executives and boards. This lack of clarity can lead to skepticism about the necessity of new investments, underfunded security initiatives, and reduced stakeholder confidence in the organization’s ability to manage cyber risks effectively.
The Solution
Use results-driven validation to demonstrate ROI:
- Continuously test and validate existing security tools and service providers to show where investments are working and where they fail.
- Present quantifiable metrics, such as SEG filtering rates or detection improvements, to justify budget decisions.
- Use data to prioritize high-performing solutions and replace ineffective tools and service providers.
When CISOs demonstrate clear, measurable value, security becomes a business enabler rather than a cost center.
5. From Reactive to Proactive: Reducing Cybersecurity Risks
The Challenge
For many organizations, cybersecurity efforts remain largely reactive, focusing on responding to incidents after they occur rather than preventing them. Many organizations only test their defenses after an incident or during annual compliance audits. This reactive approach leaves significant gaps for adversaries to exploit.
“Ransomware is the #1 risk for most hospitals, including ours. We already subscribe to the standard legacy testing practices, but we don’t have a way to continuously test and validate our defensive controls to prove they are working.” – Healthcare CISO
Why It Matters
Security teams are perpetually in crisis mode, addressing vulnerabilities and threats only after they have already impacted the organization. CISOs face the challenge of shifting to a proactive strategy that continuously identifies and mitigates risks before they are exploited. Without proactive measures, organizations remain vulnerable to evolving threats, extended dwell times, and operational disruptions, making it difficult to build a truly resilient security posture.
The Solution
Achieving this requires regular validation of security controls, real-world testing of detection and response capabilities, and actionable insights to address gaps in coverage.
- Emulate ransomware scenarios continuously to identify weaknesses across prevention, detection, and response.
- Implement Breach and Attack Simulation (BAS) tools or a managed service like Ransomware Defense Validation (RDV) to regularly validate readiness against real-world threats.
- Conduct frequent, comprehensive risk assessments to identify and prioritize vulnerabilities based on their potential impact on the organization. Leverage frameworks like NIST or MITRE ATT&CK to systematically evaluate and address risks.
- Ensure tools like EDR, NDR, and SIEM are properly configured, updated, tuned, and integrated to detect threats proactively.
- Validate incident response workflows through regular tabletop exercises and real-world simulations.
A proactive approach builds resilience and ensures defenses evolve alongside the threat landscape.
Why Continuous Validation is Essential for Ransomware Defense
For CISOs, overcoming these challenges requires moving beyond assumptions and validating defenses against real-world ransomware attacks. By demonstrating preparedness, holding vendors accountable, and continuously validating controls, CISOs can build confidence across technical teams and executive leadership, mitigate current risks, and ensure their organizations are well-prepared for the threats of tomorrow.
We learned so much by just listening to these CISOs. While they all agreed these were the biggest technical challenges they faced, the one thing that stood out most prominently when discussing ways to solve these was LIMITED BANDWIDTH. The resources needed to check all these boxes are extremely limited and they have competing priorities.
That’s why OnDefend collaborated with CISOs and security leaders to develop Ransomware Defense Validation (RDV), a fully managed service designed to do this heavy lifting for security teams.
Discover how this healthcare organization successfully implemented RDV and the positive outcomes they achieved in this case study.
Take the Next Step
Ready to prepare your organization against ransomware? Schedule a consultation today to learn how OnDefend’s Ransomware Defense Validation (RDV) can eliminate blind spots, optimize your security tools, and ensure vendor accountability.
Watch our webinar: Reimagining Ransomware Defense: Revealing and Removing the Risks of Security Control Failures with Baptisth Health CISO James Case as he breaks down the need behind proactive security validation.
About OnDefend:
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world cyber threats. From ensuring compliance with industry standards to building out mature security programs our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, contact us.
Source: (Financial Times)
A Note from the CTO:
One year ago, the OnDefend team launched what could be put into the category of a ‘newsletter,’ but in reality, it’s our commitment to transparency in showcasing the latest updates and features of the BlindSPOT product. So many times, a tool you already have implemented in your system has a cool, new, and exciting feature, but no one ever told you (the user).
One year later, we’re taking the opportunity to look back at the last year and pull some of our favorite items. While it’s a lot like picking your favorite child, we picked three features to highlight, which we think reflect the growth of the BlindSPOT capabilities over the past year.
Everything on our roadmap is designed to make BlindSPOT the best option for you to safely and quickly test your defenses, and a lot of the ideas we’ve featured in these updates have come from customer feedback and suggestions, so thank you!
-Ben Finke, OnDefend Co-Founder/CTO
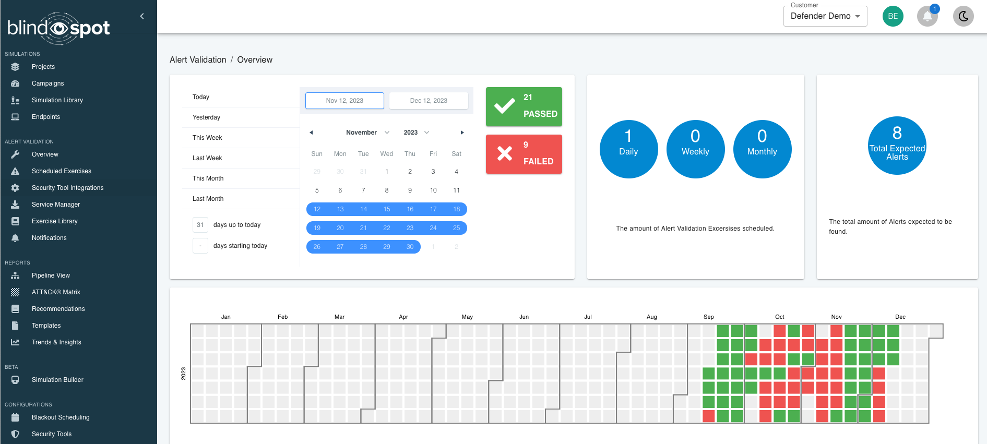
1. Alert Validation is Live
In the spirit of Halloween, it’s impossible not to say ‘Alert Validation is alive’ without putting a Frankenstein tone on it. Back to the point.
Alert Validation went live in December 2023. This feature powered by BlindSPOT automates end-to-end security tool testing to verify your detection rules are working & will successfully alert your team when you need them most.
The mission of BlindSPOT is to help you test the assumptions you have about your defenses. One assumption everyone makes is that the alerts you depend on work, and that if an attack is detected it will happen quickly!
Alert Validation is specifically built to help you answer this question, in a completely automated way.
We leverage the Attack Simulation capability within BlindSPOT to execute attack activity on endpoints in your environment, then connect to your security tools and find the alerts you expect to fire – and give you all the details about them:

We’ll show you the exact alerts firing in your tools, and how long it took for them to fire (in this case, just over 7 minutes). If any alerts you were expecting don’t fire, we’ll let you know.
All this means you get proactive testing of your detection capabilities, end to end, fully automated and over time you get a Detection Uptime report!
2. New PowerShell Module
Powershell is such a powerful tool, but to really take advantage of it (and demonstrate whether you have visibility into it) we really wanted to construct a way for you to start a Powershell process and interact with it throughout the simulation.
Launched in June 2024, this module is just one example of the improvements being made to allow your BlindSPOT simulations to look as realistic as possible.

We added a new PowerShell module to the list of payload modules. Previously the run module was the most common way to execute any PowerShell activity, but that meant every step that ran PowerShell started a brand-new PS process, executed the command, and then exited the process.
Our PowerShell payload module starts a PS process and then lets you interact with it throughout the simulation. So, if you set a variable in step 8, you can reference it again in step 17! And if you bypass a security control (cough AMSI cough), you get to take advantage of that work for the rest of the simulation.
Catch Up on BlindSPOT’s Summer Updates
3. Offline Scoring Sheets
From our famous “Speed” newsletter, we wanted to highlight the creation of the scoring sheets, to help with the understanding of the campaign activity and turbocharge the ability to rapidly score your assessments, even if you can’t use our integration directly to your tools.
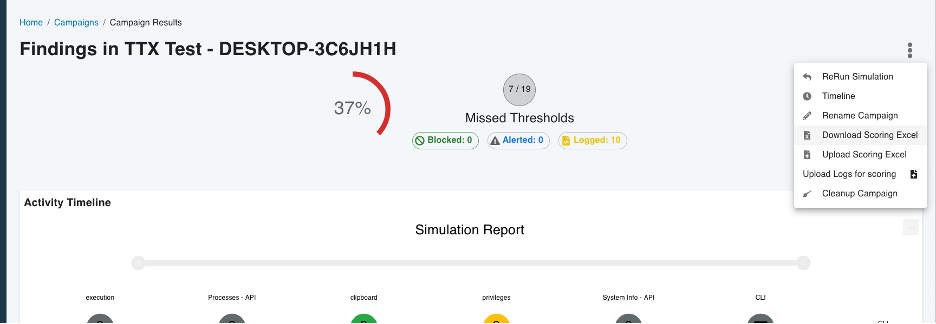
One of the biggest friction points with purple team exercises is how long it takes to get through a workshop, and BlindSPOT is here to speed that up – letting you run more (and better) exercises, more often.
The spreadsheet file that you download has all of the details you’re used to seeing in BlindSPOT, and even has dropdowns for you to select the outcome and the security tool:
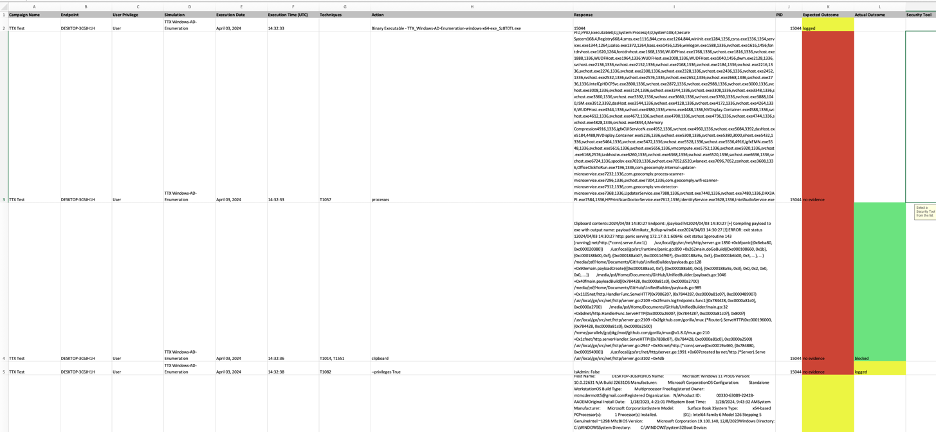
When you are done, just save the spreadsheet file, and upload it back into the campaign from the same menu, and BlindSPOT will update the campaign score for you, from the spreadsheet.
Oh, and it works for entire projects too, in one sheet! That’s what we call speed and funcitonality.
. 
One Last Thing….
Whether this if your first time diving into BlindSPOT’s updates or you’ve been on this journey for a while, thank you. We plan to continue making progress and sharing those updates with you. We are committed as an organization to continue pushing boundaries within the world of innovation, BlindSPOT is the product of that.
If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
I am a firm believer that we can clean up a lot of our technological problems, most of which we’ve caused ourselves, but the real question remains: Can we actually “solve” cybersecurity?
We can take a historian’s view on how the security arc closed in a hypothetical future to see how we might approach this problem in our present.
Passwords
Let’s start with passwords. It turns out passwords aren’t a great security measure because people generally use (and reuse) passwords that are easy to guess. Making this problem worse, many of the apps we use do a poor job of keeping these passwords secure. Once a password is leaked as part of a breach on one site, attackers begin trying it on others. If we’re going to make any meaningful progress, we’re going to have to fix this.
Actually, there is already really good progress on this front. We’ve figured out how to get rid of passwords as the main method of proving that people are who they say they are, such as by using hardware tokens (like FIDO keys), multifactor authentication and federated authentication (like OpenID Connect).
In the future, I believe these technologies will take over as the standard, and the days of using a password that you create yourself are coming to an end.
Software Vulnerabilities
Another major problem creating the security situation we have today is the staggering volume of vulnerabilities in the software we use—vulnerabilities that often allow attackers to gain full access to the system or our data.
So, how can we make it so that these software products are not as easily exploitable? One change is the use of memory-safe languages (such as Rust or Go), eliminating whole classes of software vulnerabilities.
We’ll also need to implement robust security controls that are used during software development and that can identify flaws and provide direct feedback to the developers while they are working. Another solution, better controls and governance over third-party components in use, whether open source or commercial, will cut down on “inherited” vulnerabilities (like Log4J).
Observability
The next problem that needs to be solved is an issue called observability: Do we have the ability to identify “malicious” or “unauthorized” activity within the system? This doesn’t just have to be a security feature. Too often, this logging is configured to only show errors or critical problems.
Even if a more verbose logging mode is available, the information conveyed is often incomplete or lacking in context. Organizations rarely consider this step an important component in selecting a software product or consider it “production ready.” Ask what a “normal session” looks like from the logs, and you get blank stares. Without this ability to baseline normal, we have a really tough time telling abnormal.
In our hypothetical future, we’ve come to realize that if a digital tree falls in a cyber forest, we’d better be able to hear it. Future systems will provide useful and detailed logs by default. This enhanced data collection also makes it easy to baseline “normal operations.”
Security analytic tools (a much-improved version of what used to be called SIEMs) can consume all this data in real time and apply hundreds of different AI-powered digital analysts to hunt for malicious activity, with the ability to respond when unusual activity is detected. Make sure the bells and whistles go off when they need to, uncovering a company’s security control blind spots.
If an attacker today can’t guess your password or exploit one of your internet-facing systems, they’ll resort to the most common initial access vector—email. It is hard to distinguish these targeted phishing attacks from real emails for a variety of reasons.
Whether the attacker sends a link to trick you into disclosing your password or downloading an attachment and running it, the goal is the same: get this message past all the security controls and convince you to respond.
In our future world, email follows very strict adherence to security guardrails, and an unsolicited email doesn’t even make it to the user’s inbox anymore. Very little traffic flows directly via standard SMTP email channels, most of coming through a specific app (like for your bank) and is verified before showing in your “inbox.” Today, the inbox is the quickest path to success, as we see over and over again that phishing emails are the source of many breaches.
And what about those attachments that contain the first stage of the attacker’s malware?
Well, in our more secure world scenario, almost everyone uses computers that can only install software from an app store, and these apps run in their own separate spaces, kind of like iOS and Chromebook devices today. No longer can software just be downloaded from any site on the internet and then installed or executed.
Solving Security
Here’s the million-dollar question, even if we make enormous strides by implementing all the above, technically speaking, in the security space: Have we solved security?
Sadly, the answer is no.
There will always be scams. People will still fall for fraudulent requests for money, give access to people who aren’t authorized and configure apps for convenience, not security. After all, people ignore plenty of red flags in other parts of their lives; why should this be any different?
Our best shot at solving security is to take as much of the human element into account as possible. In addition to employee training, we should build better apps to make the secure option the default, make it harder for attackers to pretend to be legitimate parties and make it easier to protect our accounts and data.
I’m certain we will continue building better technical solutions, but that won’t be enough to solve our cybersecurity problem. But we can all take steps to be more cyber secure; little fixes can make big impacts.
Often, these vulnerabilities exist in systems we expect to be internet-facing and, as a result, secure enough to perform that role. It’s hard to create a secure system when the pieces you use to build it turn out to have trapdoors in them.
Read the original article here: Forbes Tech Council: Can Cybersecurity Be Solved
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world cyber threats. From ensuring compliance with industry standards to building out mature security programs, our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, please visit http://www.ondefend.com/
OnDefend Media Contact:
Lauren Verno, Vice President of Communications & Marketing
904-299-3669
A Note from the CTO:
Speed. That’s what I want to focus on today.
The main issue we see with organizations being able to effectively leverage their purple team testing program is speed. It just takes so long to execute a proper purple team exercise – the research, the planning, the execution, the scoring and analysis, and then implementing new detections and mitigations.
If it takes three months for the team to work through this process, best case scenario you get four exercises done in the year.
But I am guessing you’d like to do more than that. Me too.
While the team has been busy building a lot of new features and improvements into BlindSPOT, today we’re going to focus on those items that we’ve targeted to help with speeding up your purple team exercises. Our goal is to trim down those time-consuming tasks that are so necessary to execute a purple team while still giving you the ability to simulate the real threat actor activities you are worried about.
-Ben Finke, OnDefend Co-Founder/CTO
Offline Scoring Sheets
Sometimes it’s just not feasible to conduct all of the scoring directly in the BlindSPOT interface. Our scoring sheets export the data from the campaign you are working on, and allow you to score the campaign inside of Excel:

The spreadsheet file that you download has all of the details you’re used to seeing in BlindSPOT, and even has dropdowns for you to select the outcome and the security tool:

When you are done, just save the spreadsheet file, and upload it back into the campaign from the same menu, and BlindSPOT will update the campaign score for you, from the spreadsheet.
Oh, and it works for entire projects too, in one sheet!
Our BlindSPOT consulting team has seen an enormous increase in speed using these sheets to score the campaigns. Very helpful for team members who can help score, but don’t have access to BlindSPOT.
Autoscoring for Microsoft Defender for Endpoint from Export
One of the most time intensive parts of a purple team exercise is the scoring – how did our tools handle those attack activities? As you may have noticed, we’ve been busy building integrations to enable autoscoring (BlindSPOT will connect to your security tools and extracts all of the alerts and logged data, and automatically score your BlindSPOT campaigns), which are very useful. But sometimes the integration just isn’t possible.
Until now…… (sorry for the cheesiness.)
We’ve built a file upload input for Microsoft’s Defender for Endpoint. MDE makes it very easy to export an entire incident to a file. BlindSPOT will now let you upload that file into a campaign and will use that file to autoscore the campaign.
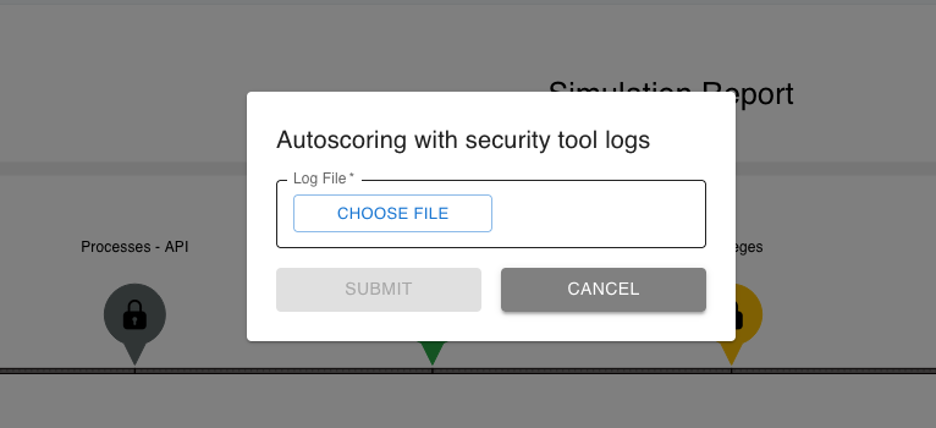
This is useful in situations where a direct integration with Defender is not possible, but you’d still like to hurry up the scoring. Just find the incident (or walk the team member with access to MDE) through the process of exporting just the data you need.
Our initial testing shows this can save up to an hour per campaign, depending on your experience scoring in BlindSPOT.
New Reporting Engine
While not the biggest time saver that we will talk about today, it is a whole lot faster!
Our new reporting engine is able to generate reports about 400% faster than our previous engine, generating large and complex reports in under 30 seconds.
We’ve also improved the resolution of the images and charts and have refactored the base version of the BlindSPOT report template.
You don’t need to do anything to start using this, it’s already in production.
One Last Thing….
Thank you for taking the time to read our newsletter. We are committed as an organization to continue pushing boundaries within the world of innovation, BlindSPOT is the product of that.
If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
A Note from the CTO:
Building BlindSPOT is fun, full stop.
Both the development and tradecraft teams get the chance to solve difficult challenges and puzzles with the direct goal of making BlindSPOT a better tool for you to answer the question “What would happen if…”.
Of course, because we are performing the same behavior that attackers do, the same defenses that get put in place to stop them, stop us. We don’t just end up building simulations that mimic the same behavior that threat actors do, we end up acting like threat actors through the whole development lifecycle.
A lot of the updates we do to agents, payloads, and other components are all geared to making sure that BlindSPOT provides an effective tool in your toolbox.
- Effective to build realistic simulations, encapsulating the tradecraft we bring (or the tradecraft you bring).
- Effective at being easy to execute and fast to get results from.
- Effective to rapidly deploy and scale testing across your environment.
- Effective to generate useful metrics that help you understand how you will perform against real adversaries.
We’re excited to see how the new features help you improve your defenses, and what ideas they generate for you. As always, we’d love to hear from you on what you think about BlindSPOT, and where we can help you answer the question “What would happen if…”.
OK, on to the show!
-Ben Finke, OnDefend Co-Founder/CTO
New PowerShell Module
We’ve added a new PowerShell module to the list of payload modules. Previously the run module was the most common way to execute any PowerShell activity, but that meant every step that ran PowerShell started a brand-new PS process, executed the command, and then exited the process. Our new PowerShell payload module starts a PS process and then lets you interact with it throughout the simulation. So, if you set a variable in step 8, you can reference it again in step 17! And if you bypass a security control (cough AMSI cough), you get to take advantage of that work for the rest of the simulation.
You’ll see the PowerShell module already listed in the Simulation Builder, and we’re adding lots of new simulations that take advantage of this new feature.

New Alert Validation Dashboards
Alert Validation has been under development in all phases, but the new dashboard helps you zero in on any issues with your detection uptime, and understand how long it takes to resolve any issues, once found:

Learn More About Alert Validation
New Agent Builds Available (in Beta)
We’ve completely rebuilt the BlindSPOT agents from scratch, enhancing functionality and adding some additional tradecraft to make them easier to deploy and run. Available now as the “Beta” option in your agent builder, give it a try!
One Last Thing….
Thank you for taking the time to read our newsletter. We are committed as an organization to continue pushing boundaries within the world of innovation, BlindSPOT is the product of that.
If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
A note from the CTO – Ben Finke
If you haven’t heard about our Alert Validation module yet, let me be the first to (happily) tell you what it is and why you should care. Alert Validation isn’t designed to help you identify gaps or “blindspots” (that’s what Attack Simulations are for). Alert Validation helps you focus on ensuring that your detection capabilities are working as expected today. That means ensuring that telemetry arrives, alerts fire, and it all happens in a time frame that you find acceptable.
Alert Validation is fully automated, executing the activity on an endpoint in the environment, then connecting to the security tools and watching for the alerts to fire. Once you’ve set up the Alert Validation Exercise, it takes over from there. You get defect reporting (one or more alerts didn’t fire as expected, or it took longer than you wanted) when the testing fails, and over time we build a detection uptime report.
Sending a canary event through the pipeline gives you the assurance that the detection capabilities you rely on work, with much more certainty than simply monitoring the components of that same pipeline. Any failures that would prevent your alerts from working against a real attacker will be identified and let you address them without the mess of having missed a real event.
And we don’t have to stop at the first alert. If you have an MSSP or MDR provider, we can include them in the automation too. Now you can have daily validation that your security provider can see activity in your environment, and exactly how long it took for them to see it. Oh, and Alert Validation can automatically close the alerts created through testing, keeping that load off of your team and without impacting your service delivery metrics.
Alert Validation can be done on its own or is a great second step after you’ve spent time using the Attack Simulations to tune your tools and want to make sure they stay tuned.
If you’re interested in seeing what Alert Validation can do for you, let us know, and we’d be happy to get you set up! Learn More
-Ben Finke, OnDefend Co-Founder/CTO
Updated Alert Validation Details Page
Keeping the Alert Validation talk going, we recently refurbished our Alert Validation detail page to make it easier for you to see the results of each Alert Validation Exercise.

Each alert that is setup in the Exercise is shown with the Pass or Fail grade, and drilling into each you can see exactly how long it took the alert to get there, once that activity happened on the system.
Updated Campaigns Page
Our Campaigns page was recently renovated too, making it easier to see exactly which campaign is which:

Learn More About Attack Simulation
BlindSPOT Customer Success: Healthcare & Ransomware
Learn how an enterprise hospital system used BlindSPOT to validate the effectiveness of their security controls, allowing the hospital to focus on what matters most: patient care.
Read The Customer Success Story
Partner Announcement: BDO Digital integrates BlindSPOT into Active Assure Security Service
“We are proud to empower BDO Digital with our attack simulation tool BlindSPOT, providing organizations visibility into the effectiveness of their security controls and proving the value of these investments,” said Chris Freedman, Co-Founder of OnDefend. “It is no longer a question of if but when a company will face an attack. While organizations invest in technical security controls to prevent, protect, and prepare, we’ve found that security programs needed a way to validate those tools will work during those critical moments.”
One Last Thing….
Thank you for taking the time to read our newsletter. We are committed as an organization to continue pushing boundaries within the world of innovation, BlindSPOT is the product of that.
If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
A note from the CTO – Ben Finke
Our goal is to build tools that let you test your security controls – quickly, thoroughly, and safely. Most of what we execute via BlindSPOT is intended to look just like malicious activity. After all, that’s our purpose here (excluding the actual nasty impact). In some ways, we find ourselves facing similar problems that real threat actors probably do (although we certainly don’t sympathize with them). In this newsletter, we will share some recent updates to the platform that are designed to make it easier for you to leverage BlindSPOT as part of your processes, including testing tools, detections, and the teams’ ability to use those tools.
By the way, if you couldn’t make it to our recent webinar featuring CISA supervisory agent Kirby Wedekind, FBI agent Paul Magnusson, and myself, I highly recommend checking it out. We delved deep into the major threats of the year, covering everything from prevention to response strategies and available resources. You can catch it all here: CISA Year In Review: A deep dive into the biggest threats, an outlook into the new year and how to prepare. > OnDefend
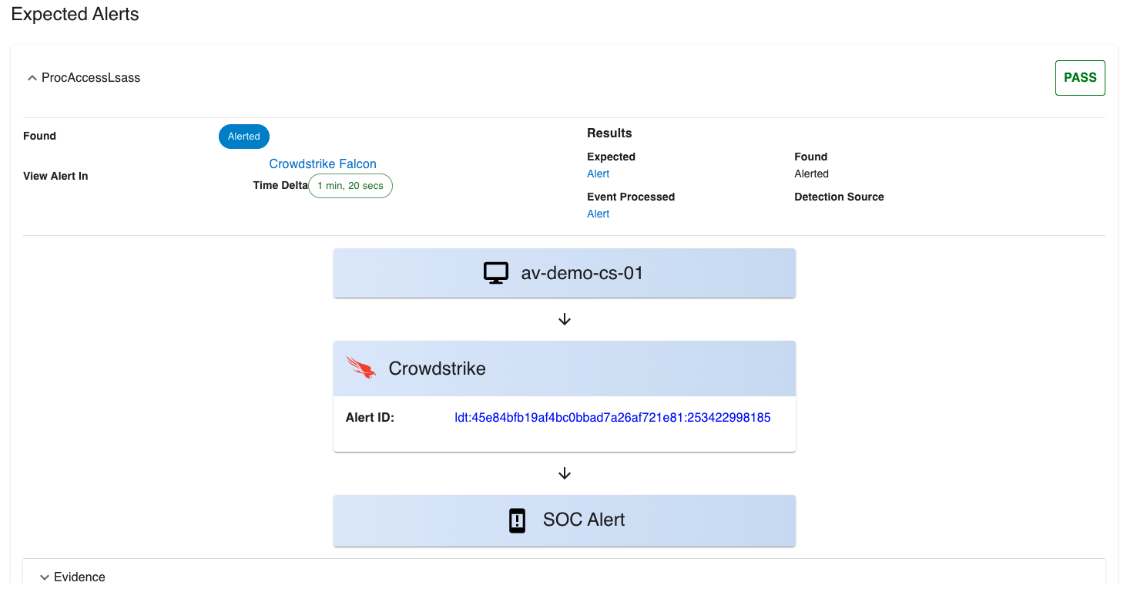
Alert Validation – Crowdstrike Falcon Beta!
In our last newsletter, we announced that our new Alert Validation feature was live for Microsoft Defender and Sentinel. Today, I am thrilled to announce that we have added CrowdStrike Falcon to that list (in Beta). With this integration, you can automatically exercise Crowdstrike Falcon detection and alerting, without any manual intervention from your team, and be alerted when an issue occurs. Alert Validation is an excellent way to put a detection into “maintenance” mode, allowing you to use the Attack Simulation tools to identify more gaps and blind spots in your detection program.
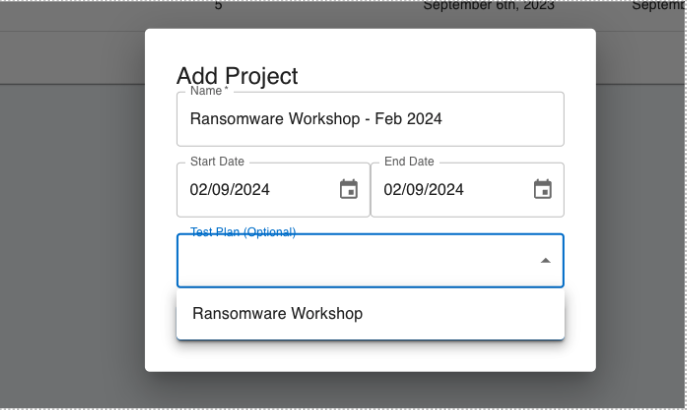
Test Plans
If you need to run the same set of campaigns across a large group of endpoints, Test Plans will save you time and make the setup easier. Test Plans allow you to configure the specific campaigns you want to run, create a project, and simply select the endpoints to include. Test Plans will take care of building out all the individual campaigns for you.
New Simulation – Alert Validation Monitoring
If you want to run a campaign that triggers numerous alarms from a wide variety of techniques, check out our new simulation, Security Monitoring Validation v1.0. Inspired by various reports of the Top 10 TTPs used by attackers, this simulation covers a variety of techniques and procedures in a single simulation.

Sneak Peek into the Dev Channel
Here are some exciting projects we are cooking up in the lab that we will be able to share with you shortly:
- BlindSPOT Satellite – a purpose-built system to serve as a target for exfiltration, Command and Control, and File Downloads – letting you change the Internet facing target and expand the ability to test your network perimeter systems.
- Attack Simulation AutoScoring – Soon to be released for both Microsoft Defender and Crowdstrike Falcon – with more tools on the way.
- SentinelOne Alert Validation – yep, will have it in the lineup shortly.
One Last Thing….
We have been thrilled to see the simulations our users have been creating in the sim builder, and we are working on a way to let the BlindSPOT community share some of this incredible tradecraft and simulations (if you choose to share it). Thank you for using BlindSPOT as the platform to help you with your security testing work, and we look forward to continuing to build features that make this platform easier and more capable for you!
If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
The newly released 2023 CISA year in review is out and we’re taking a deep dive into the biggest threats, an outlook on the forecasted trends for this year, and a discussion into whether these trends are inevitable or solvable.
Join CISA supervisory protective security advisor Kirby Wedekind, FBI supervisory agent Paul Magnusson, and OnDefend CTO Ben Finke for this interactive discussion where they’ll:
- Analyze the biggest trends, threats, and industries targeted in 2023.
- Explain why they believe these threats topped the list.
- Delve into steps organizations can take to prevent an attack and what to do if they are attacked, including analysis and forensics.
- Compliance, regulations, and reporting- what is that going to look like in the new year?
- Reveal the common patterns discovered within organizations after a breach.
- Look forward to 2024 and how to develop an IR plan for the new year.
You can watch the full recording now:
Speakers:
Ben Finke, OnDefend Co-Founder/CTO
Ben Finke has almost 2 decades worth of experience in cybersecurity, starting as a communication officer in the U.S. Air Force. Over the course of his career Ben worked with organizations ranging from government agencies to fortune 500 companies including, being embedded in development teams in SaaS companies, overseeing a red team for testing critical infrastructure systems, and running the security practice for a managed security provider. In 2016, Ben Co-founded OnDefend where he currently serves as the Chief Technology Officer. Ben also is the creator of BlindSpot, a purple team testing automation tool. Ben has a bachelor’s degree in computer science from Florida State University.
Kirby Wedekind, CISA Supervisory Advisor Protective Security Advisor
Kirby Wedekind serves as the Cybersecurity and Infrastructure Security Agency’s Supervisory Protective Security Advisor in northeast Florida. Based in Jacksonville, his duties include serving as a liaison from CISA to local government agencies and private industry; fostering community awareness on security topics ranging from cybersecurity to active shooter preparedness; conducting vulnerability assessments of critical infrastructure; and sharing security-related information with communities of interest across northeast Florida. Dr. Wedekind supervises the Protective Security Advisors in North Carolina and South Carolina.
Paul Magnusson, FBI Supervisory Agent
Paul Magnusson serves as a Supervisory Special Agent with the Federal Bureau of Investigation in Jacksonville, Florida. SSA Magnusson started his law enforcement career in 1998 as a Deputy Sheriff with the Washtenaw County Sheriff’s Office in Michigan, where he led all cyber investigations and computer forensics examinations. In 2005, Magnusson entered on duty with the FBI as a Special Agent assigned to the Minneapolis Division Cybercrimes Task Force and became a member of the FBI Computer Analysis Response Team, conducting computer forensics examinations. In 2008, he was promoted to Supervisory Special Agent of the Tactical Operations Section within the FBI Operational Technology Division. In 2018, SSA Magnusson transferred to the FBI Jacksonville Division, where he has managed various programs, including the National Security and Criminal Cyber, Computer Forensics, Surveillance, Aviation, Electronic Technicians, and Technically Trained Agent programs. SSA Magnusson earned his Bachelor of Science in Criminology and Masters in Information Security & Technology from Eastern Michigan University.
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world threats. From ensuring compliance with industry standards to building out mature security programs our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results.
Originally published in Hotel Executive: Hotel Executive Article
A quality guest experience and a hotel’s success go hand in hand, but at what cost? Ease of access around the hotel, instant connection to Wi-Fi, almost every aspect between the check-in to check-out process requires some form of technology. However, each of those access points is a prime target for cybercriminals to exploit and one of the reasons why attacks are only expected to increase.
Why Target Hotels?
Hotels have become appealing targets for cybercriminals for several reasons, including the data they collect, the volume of credit card transactions they make, the complex system of vendors, guest Wi-Fi networks, the proprietary and 3rd party apps and platforms they use, as well as the constant journey to make the customer experience as smooth and easy as possible.
The primary driver of attacks on hotels have historically been driven by financial gain, data theft, or causing disruption to hotel operations. One of the primary objectives is to steal payment card data, including credit card numbers, names, and security codes, which can be used for unauthorized transactions or sold on the dark web for profit.
Identity theft and fraud are also common goals, with cybercriminals aiming to use stolen personal information to commit various fraudulent activities. Ransomware attacks seek to encrypt critical hotel data, such as guest reservations or financial records, with attackers demanding a ransom in exchange for the decryption key, disrupting operations until payment is made.
Additionally, attackers may target a hotel’s financial systems, corporate espionage may occur in luxury or corporate hotels, and data exfiltration can be used for extortion, selling information to competitors, or intelligence gathering. Some attacks aim solely to disrupt hotel operations, causing financial losses and reputational damage. Opportunistic attackers may seek any vulnerability to exploit for financial gain.
Hotels are seemingly easier to infiltrate than other industries such as healthcare or financial. Historically, the hospitality industry is not known for building and incorporating a robust cybersecurity program. Which leaves hotels as low hanging fruit for these cybercriminals.
In fact, within the hospitality industry are likely unaware of how vulnerable their organization could be to an attack. A joint study from Cornell and FreedomPay revealed that of the 300 hospitality specific enterprises surveyed nearly all, 96% said they are confident in their companies internal risk assessment processes. Yet, nearly one-third (31%) experienced a data breach in their company’s history, the majority – 89% – having experienced more than one breach attempt in a year and 69% attacked more than three times in a year.
Top 3 Hotel Attack Vectors
We’ve covered why cybercriminals target hotels but how do they do it? While there are countless of ways for an attacker to get into a system, there are three primary points of access that every executive should be aware of.
The most common method is phishing attacks. Cybercriminals send deceptive emails to trick hotel staff, guests, or third-party partners into revealing sensitive information or downloading malware. You’ve likely received one of these emails in the last month, offering a “free” gift card or an “urgent” message from the IRS.
This method was the cause of the recent “vishing” attack on MGM Casino where hackers had access to the organizations system for 10 days. The adversary impersonated a fellow MGM employee on a phone call and persuaded the information technology helpdesk to provide them access into the MGM environment. From there, they gained access to other systems and eventually executed a ransomware with a total cost yet to be finally calculated, but you can be assured, it will be in the tens of millions.
Another common attack method is point-of-sale and payment cards which commonly pose the biggest threat to the hospitality industry. Threat actors find point of sale (POS) systems to be the most direct route to credit card information and financial gains. These systems are often configured improperly, with weak passwords and/or insecure remote access, opening the door for cybercriminals to easily infect them with card-skimming malware. The problem is compounded by the fact that hotels typically delegate their POS security to third-party vendors, offering threat actors yet another potential attack vector. Hotel POS systems are complex because they have multiple POS terminal locations – front desk, on-site shops, spas, restaurants, parking etc. – and thus the possible entry points are dispersed and more accessible. In 2017, Hyatt Hotels Corporation reported a data breach that impacted approximately 41 of its properties in 11 different countries. The breach involved the theft of customer payment card information from the hotel’s POS systems. The attack occurred due to malware that was installed on the POS systems, allowing cybercriminals to capture payment card details during transactions.
Finally, I couldn’t imagine staying at a hotel now a days that doesn’t offer Wi-Fi, unfortunately, this has opened yet another vector for hackers to infiltrate. Public Wi-Fi networks have fewer security levels than private networks. And many attacks on hotel systems are made possible by human error – for example, if an unaware hotel employee configures a secured network as “open,” they have effectively created a rogue access point (AP). Cybercriminals can use this rogue AP to attack the network from the hotel lobby or even a nearby building.
The Cost of a Cyber Breach
A cyber breach can bring about substantial legal and financial consequences for those involved. From a financial perspective, organizations can face direct costs such as expenses associated with investigating the breach, notifying affected individuals, offering credit monitoring services, and implementing security fixes.
According to IBM’s Cost of a Data Breach Report 2023 (2) the average cost of a breach for the hospitality industry was $3.36 million dollars, up from just under $3 million dollars the year before.
Indirect costs may include revenue loss due to downtime, damage to the organization’s reputation causing reduced business, and increased insurance premiums. Moreover, various regions have data protection regulations that demand compliance. Failure to do so can lead to substantial fines and penalties. Legal liabilities could arise as breach victims initiate legal actions, resulting in lawsuits, settlements, and legal fees. Organizations must also bear the cost of remediation, including upgrading security systems, forensic investigations, and implementing enhanced security measures.
Reputation damage can have long-lasting financial effects, leading to diminished customer trust, lower sales, and customer attrition. Lastly, the financial impact can extend beyond the immediate aftermath, affecting stock prices, investment prospects, and long-term financial stability.
Five Notable Hotel Breaches and How the Hackers Got In
InterContinental Hotels Group (2016): InterContinental Hotels Group (IHG) disclosed a data breach that affected more than 1,200 of its properties in the United States. The breach occurred due to a malware attack on the hotel chain’s payment card processing systems, which compromised guests’ payment card information.
Marriott International (2018): One of the largest hotel data breaches in history, the Marriott breach involved the exposure of data of approximately 500 million guests. It was discovered that unauthorized access to the Starwood guest reservation database had occurred, potentially compromising personal information, including names, addresses, phone numbers, passport numbers, and payment card data. The breach was ongoing for several years before being detected.
Hilton Worldwide (2019): The Hilton Worldwide data breach affected over 4.5 million guests. The breach was caused by a phishing attack that targeted Hilton employees. The phishing attack tricked employees into revealing their login credentials, which were then used by cybercriminals to access the Hilton reservation system. The cybercriminals were able to steal guest data, including names, addresses, phone numbers, email addresses, and passport numbers.
Wyndham Hotels & Resorts (2020): The Wyndham Hotels & Resorts data breach affected over 600,000 guests. The breach was caused by a malware infection in the Wyndham Rewards loyalty program. The malware was able to steal guest data, including names, addresses, phone numbers, email addresses, and Wyndham Rewards member numbers. For some guests, the malware also stole payment card numbers and expiration dates.
Wyndham Hotels & Resorts (2022): The May 2022 Wyndham Hotels & Resorts data breach affected over 1 million guests. The breach was caused by a malware infection that was able to steal guest data, including names, addresses, phone numbers, email addresses, and passport numbers.
Compliance Does Not Mean You Are Cyber Secure
Part of being an executive is making the hard decision about where to cut costs to keep a business profitable. Over the years, I’ve noticed a trend when it comes to organizations investing in cybersecurity. If the company meets compliance standards then they are protected but that’s not entirely true. Compliance standards within the realm of cybersecurity has a long way to go.
A Deloitte survey of 500 c-level executives found that 85% of chief information security officers said they can measure and demonstrate compliance (3). If that’s the case, why are companies still struggling with major breaches? That’s because current compliance standards only scratch the surface when it comes to being secure. Without getting technical, let’s look at your home security system in terms of cybersecurity compliance. It would be like, proving to your insurance company that you have door and window sensors that should go off if someone we’re to break in, but never really knowing if those sensors worked until someone was actually breaking in, but at that point it’s too late. Many compliance standards within cybersecurity can lead to the same outcome. An organization is required to have certain programs, training, or certifications but whether they are working and proving to be effective is another story. Now, that’s not to say that every organization does this but organizations that rely solely on “checking the box” are much still vulnerable to an attack.
Things to Focus on to be More Cyber Secure
- Educate and Empower All Staff Members
In more cases than not, a cybersecurity issue starts with human error. This is not to put fault on employees but primarily the lack of training and awareness. As we saw with the most recent MGM hack, most of these attacks begin with phishing, so training employees to be aware and prepared for phishing tactics is crucial.
Our firm was once hired to run phishing training for the entire organization. We sent out phishing emails to see who would respond and click the exploitable link. The CEO of the company, who knew we we’re running the training forwarded the entire email to the company believing there we’re actual changes from HR that everyone needed to be aware of.
It goes to show even if you are prepared and warned of an attack, it is so easy for something to slip by. These criminals are extremely tricky and good at preying on an individual’s emotions or finances to get them to open or download an email.
Regular training empowers employees to make informed decisions and act as the first line of defense. It’s important to remind everyone that safeguarding your companies most sensitive information is not just as “IT” issue.
- Bolster Network Infrastructure
Hotels must patch and update their systems as frequently as possible to mitigate their vulnerabilities. When a network is left unpatched, hackers can exploit these weaknesses to attack the system. In particular, hotels should direct their utmost attention for patching and updates to POS systems. Here are a few steps hotels should take to ensure their POS systems are secure:
- Use complex passwords on POS systems.
- Use two-factor authentication.
- Ensure antivirus or endpoint protection is up-to-date.
- Separate the POS network from other networks and investigate anomalies.
- Filter which external IP addresses can reach the remote-access mechanism of the POS controller.
- Use PCI-Validated Point-to-Point Encryption (P2PE) to encrypt credit card data immediately upon payment.
- Segment Wi-Fi networks by making guest Wi-Fi and business networks separate.
- Deploy Wireless Intrusion Prevention Systems (WIPS) to detect and prevent hacking attempts against the Wi-Fi network.
- Assess Vendors’ Security Capabilities
Many cyberattacks are carried out through third-party vendors. Third-party vendors are part of any organization’s attack surface and pose a huge risk to overall security. To assess third-party vendors, start by conducting a thorough risk assessment. Identify the criticality of their services to your organization, the type of data they handle, and their security practices. Request and review their security policies, compliance certifications, and incident response plans. Evaluate their past performance and reputation through references or industry reviews. Assess their financial stability to ensure long-term viability. Lastly, establish clear contractual obligations regarding security, data protection, and compliance to mitigate risks associated with third-party relationships. Regular monitoring and audits should also be part of your vendor management strategy to ensure ongoing compliance and security.
- Perform Internal Threat Hunting
Hotels have massive digital footprints because of all the different systems they use. Hackers often try to gain entry into a network and then move around within the system to find data they find valuable. Thus, security teams need to monitor their own internal network traffic to identify suspicious activity and discover potentially unauthorized access.
Threat hunting with a breach and attack simulation (BAS) solution is a proactive cybersecurity approach that helps organizations uncover potential threats and vulnerabilities within their networks. This process involves carefully planning and preparing objectives, selecting the right BAS tool, and assembling a dedicated threat hunting team. Data collection, including logs and network traffic, is crucial to the analysis. BAS tools simulate various attack scenarios, and the results are scrutinized for anomalies and unusual patterns. When potential threats are detected, they are investigated, and if confirmed, immediate action can be taken to contain and remediate them.
- Develop and Incident Response Plan
Hotel security teams cannot afford to sit around and wait for attacks to happen. They need to assume it’s a matter of when, not if, they’ll be targeted.
According IBM’s Cost of a Data Breach Report 2023, on average it took organizations 204 days to identify a breach and another 73 days to contain it (4). Every hotel should have an incident response plan in place if a data breach does occur to help streamline the communication and mitigation process.
One way to stress test your incident response plan it through tabletop exercises which hold significant value for organizations as they provide a structured and cost-effective way to assess and improve their incident response capabilities. These exercises simulate various crisis scenarios, allowing executives and key stakeholders to collaborate, identify weaknesses, and refine their response plans. By doing so, organizations can better prepare for real-world emergencies, minimize the impact of incidents, and protect their reputation and assets.
At the end of the day, even if a security team had an unlimited budget, there is no way to 100% prevent a cyberattack. However, with the right tools, training, and response plans in place, companies can at least take steps in the right direction.
Resources:
Cost of a data breach 2023 | IBM
The Future of Cyber Survey | Deloitte US
Cost of a data breach 2023 | IBM
Media Contact:
Lauren Verno, OnDefend VP of Communications: Media@ondefend.com
