Security Control Validation: Why Testing Once Isn’t Enough to Stop Threats
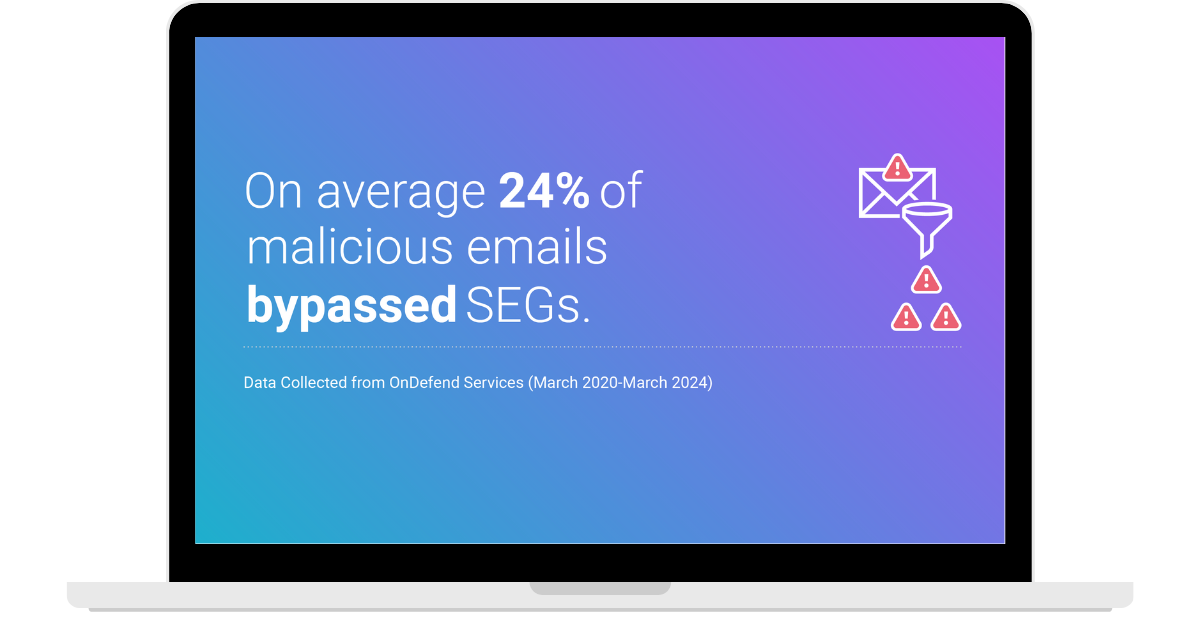
Traditional security assessments and out-of-the-box tool configurations aren’t enough to protect against adversaries. Organizations need continuous security control validation — real, ongoing testing to ensure their defenses are detecting and stopping threats before damage is done.
Read