Welcome to 2024! As we take on this new year, we’d like to reintroduce our company, OnDefend.
We are a cyber security firm with a unique, human-centric approach. We understand that every challenge is different and that one-size-fits-all solutions don’t always cut it.
At OnDefend, we stand out from the crowd with our agility and innovation. We’re quick on our feet, ready to design customized security solutions based on the threat actors targeting your organization. But we don’t just adapt; we innovate. You’ll find us at the front lines, tackling challenges head-on, and devising innovative strategies. We don’t believe in impossible, only in finding the right solution.
We emphasize customization – understanding that every company’s budget, timeline, and security needs are unique. Thus, we deliver tailored solutions designed to meet your specific requirements. Our reporting isn’t just insightful, it’s actionable. We provide clear, easy-to-understand reports with strategies you can implement immediately to enhance your security posture.
Connecting with our clients is at the heart of what we do. We prioritize communication, ensuring regular updates and prompt responses. We value the human element and put people first, resulting in exceptional project management and enhanced client satisfaction.
This new year, join us on our journey to prepare for and defend against threats for years to come. With OnDefend, you’re not just complying – you’re preparing to defend. Let’s take on 2024 together, and strengthen your company’s security infrastructure with our tailored, agile, and innovative solutions.
Contact us today, and let’s make 2024 the year of unshakeable defense.
A Note from the CTO
What a year this has been! If you’ve been with us throughout 2023 I hope you’ve been able to enjoy all of the new features, content, and improved performance of the BlindSPOT platform!
I’d like to thank everyone who has had a hand in helping us make BlindSPOT better – whether you gave us feedback during an exercise, sent in a suggestion, or shared some of the stories of your executions in the platform – thank you.
To the development team and the content team, I am honored to work with each of you every day, and I continue to be amazed at your creativity and determination to build something we are so proud of.
Alright, let’s get to some of the highlights of the last couple of months!
-Ben Finke
Alert Validation is Live!
BlindSPOT has always provided a way for you to find, well, your blindspots, with our Attack Simulation capability. But once you get those tools tuned and alerts just the way you want, how can you make sure those tweaks remain ready? And arguably just as important, how do you know you are getting the right data into your pipeline for those alerts to fire? Enter Alert Validation!
We leverage the Attack Simulation capability within BlindSPOT to execute attack activity on endpoints in your environment, then connect to your security tools and find the alerts you expect to fire – and give you all the details about them:
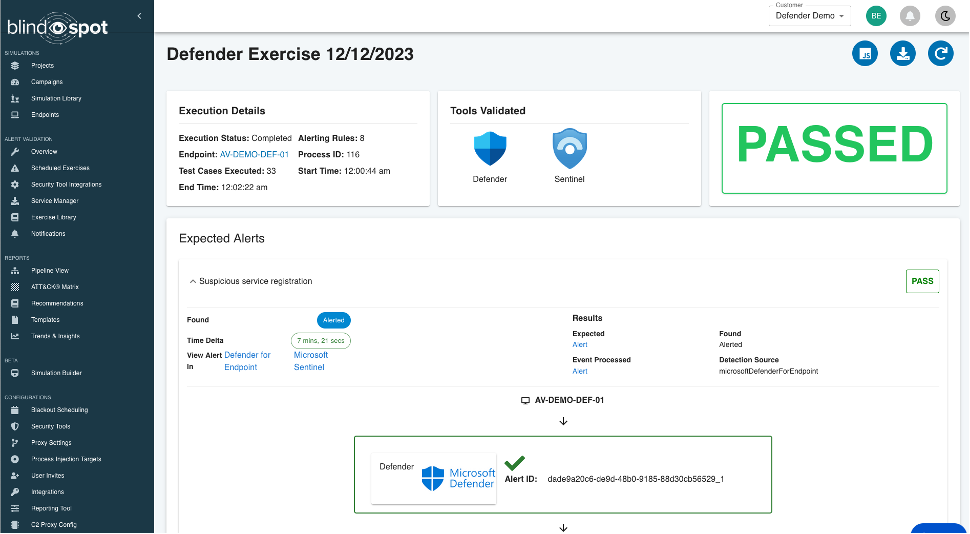
We’ll show you the exact alerts firing in your tools, and how long it took for them to fire (in this case, just over 7 minutes). If any alerts you were expecting don’t fire, we’ll let you know.
All this means you get proactive testing of your detection capabilities, end to end, fully automated and over time you get a Detection Uptime report!
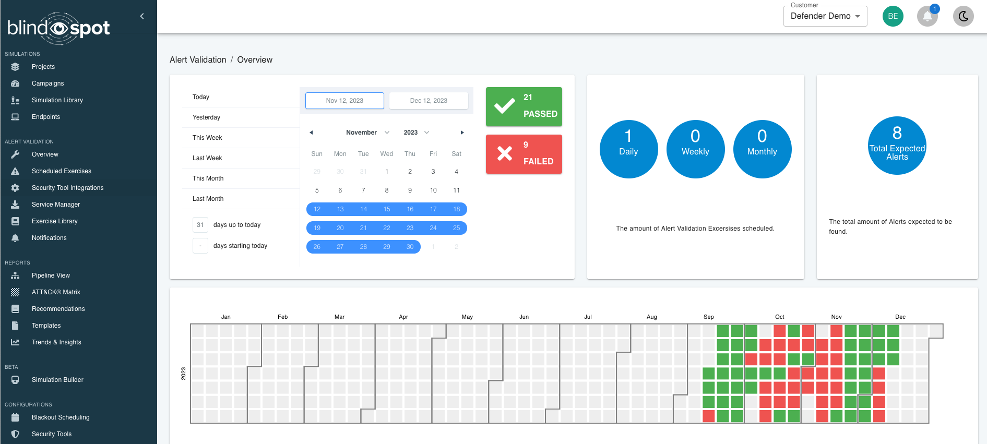
We’re starting with Microsoft Defender for Endpoint and Sentinel, and plan to expand those capabilities to include more tools in the very near future.
Already a BlindSPOT user and want to check out Alert Validation? Let us know if you’d like to try it out.
P.s. we’d love to know what tools you’d like for us to include in our next update!
New Simulation: Black Basta Ransomware
In the last BlindSPOT newsletter, we told you about our newly redesigned simulation library that streamlines the process when you want to find a specific simulation you need.
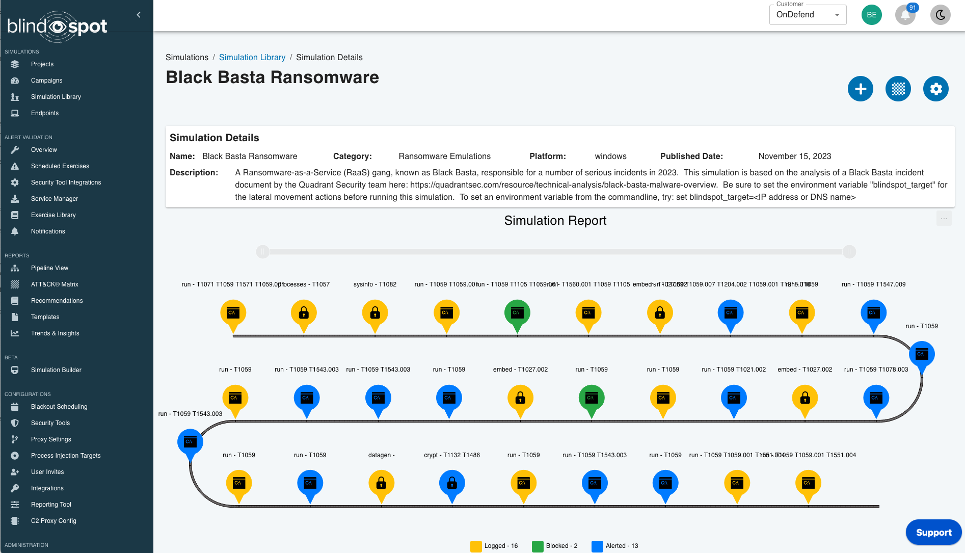
We continue to build out that simulation library and wanted to highlight a new release, the Black Basta Ransomware simulation.
Based on the excellent write-up by our friends at Quadrant Security this simulation includes lots of new tradecraft not seen in other ransomware intrusions, including, a chained LNK -> JS -> CMD -” regsvr32 executing a malicious DLL, all packed in an ISO image file.
Phew!
New Service-Based Agent
The standard BlindSPOT agent was designed to be easily placed on target systems, quick and flexible to execute, with simple cleanup (just delete the file!), but sometimes you may want a more persistent version of the agent, one that can always be ready to run a campaign, even surviving reboots. Enter our new BlindSPOT Service Manager:
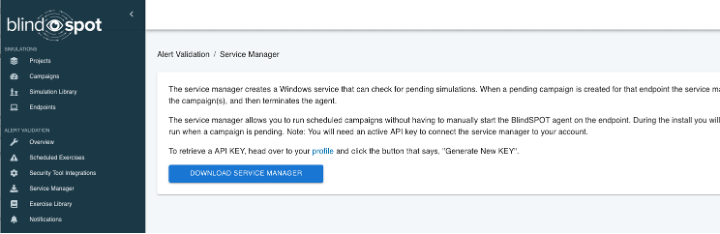
Download the Service Manager, grab an API key (oh yeah, did I mention our API is live too!), and run the downloaded MSI. You’ll see a new app on the machine, the BlindSPOT Service Manager. Enter your API key, and now you can install the service, specifying the specific BlindSPOT agent you want to use to run any campaigns you assign to that endpoint:
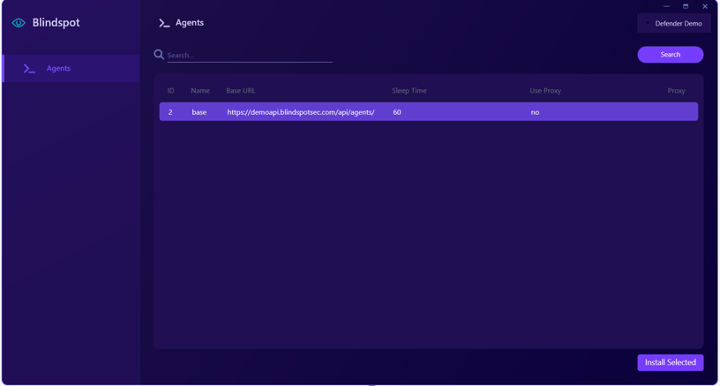
Pick the agent you want, click on “Install Selected” and you’re ready to install your BlindSPOT agent service:
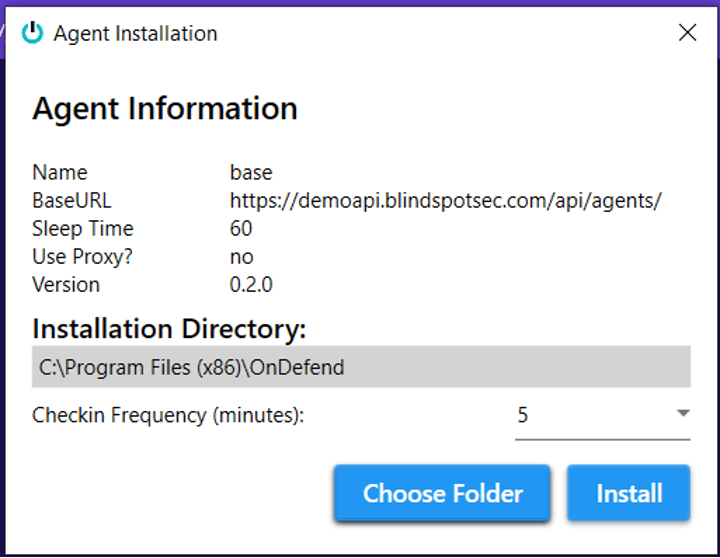
The service will check in with BlindSPOT, and when it sees you’ve got a campaign ready to run it will download and/or start the agent, execute the campaign, and then put the agent back to sleep until the next one. Works great for running Attack Simulations, and pairs nicely with the Alert Validation feature too!
What We’re Working On
BlindSPOT Satellite: We’re building an integrated utility that you can use to test data exfiltration techniques, execute different Command and Control traffic patterns (C2), and source downloads to execute tool ingress techniques. You’ll be able to use our satellites, or deploy your own on your own custom systems, using any domain you want.
Attack Simulation Autoscoring: Building on the success of our Alert Validation feature, we’ll soon have fully automated autoscoring for Attack Simulation campaigns too. (I know many we are all excited for this one.)
One last thing…
BlindSPOT was always a dream of ours and seeing it run successfully in organizations around the world is the best present we could ever ask for. From the bottom of our hearts, We want to thank you for joining this BlindSPOT journey and am looking forward to the new year. Happy Holidays everyone!

If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
Can you smell the turkey cooking? Before the holidays begin, let’s catch up on the latest cyber threats, a wrap up of cybersecurity awareness month, and BlindSPOT developments.
Cybersecurity Awareness Month
Let’s start off with the obvious, every month should be cybersecurity awareness month.

We kicked off the month at WJXT News4Jax, highlighting easy and free ways to keep your data safe.
Cybersecurity Awareness Month: OnDefend Explains How You Can Keep Your Data Safe > OnDefend
—
Cybersecurity companies are not just made up of hackers. From project managers to product development, we wanted to give an inside look at who actually works at a cybersecurity company.
Getting To Know The Different Roles Within A Cybersecurity Company > OnDefend
—
While not everyone who works at OnDefend is a hacker, we wouldn’t be able to offer our red-team capabilities without a few. In the Pentester Roundtable, we sat down with two ethical hackers and deep dived into getting into and staying in this career.
Pentester Round Table- Part 1 – YouTube
—
We’re lucky enough to work with some pretty interesting partners and industry leaders. It’s safe to say they have seen a few interesting moments throughout their career. While we could never cover them all, here’s a highlight of some of the worst ” Cybersecurity Horror Stories.”
Cybersecurity Horror Stories > OnDefend
Cybersecurity Roundup: Top Stories from the Digital Frontlines
Ransomware attacks are stealing more than just data, but potentially lives. In the beginning of 2023, The US Department of Health and Human Service Office for Civil Rights was hit with a total of 327 reported data breaches. The massive increase of over 100 percent from the 160 breaches they had on record by mid-2022.
Ransomware: The Unseen War Holding Lives Hostage (thecyberexpress.com)
—
Having trouble getting ChatGPT to work? Open AI, the parent company of ChatGPT confirmed the outages can be linked to ongoing distributed denial-of-service (DDoS) attacks. While OpenAI has yet to publicly confirm who exactly is behind the attacks, a threat actor known as Anonymous Sudan claimed to be behind them due to the ongoing conflict in Israel.
OpenAI confirms DDoS attacks behind ongoing ChatGPT outages (bleepingcomputer.com)
—
The US government has launched a new campaign to promote critical infrastructure security and resilience, focusing on broad, strategic strategies. The Shields Ready campaign complements CISA’s Shields Up campaign, which focuses on specific, time-sensitive actions.
US launches “Shields Ready” campaign to secure critical infrastructure | CSO Online
—
Okta is blaming the recent hack of its support system on an employee who logged into a personal Google account on a company-managed laptop, exposing credentials that led to the theft of data from multiple Okta customers. According to the company, the username and password of the service account had been saved into the employee’s personal Google account.
Okta Hack Blamed on Employee Using Personal Google Account on Company Laptop – SecurityWeek
OnDefend in the Spotlight
OnDefend CTO Ben Finke shares his thoughts and recommendations for cybersecurity compliance standards with Forbes Technology Council.
Billions of dollars are spent on cybersecurity every year, yet the problem of ransomware outbreaks, data breaches, and identity thefts continues to grow.
How do you raise the bar without adding unnecessary regulations?
You can check out Finke’s recommendations here: Why Cybersecurity Compliance Standards Still Have A Long Way To Go (forbes.com)
—
OnDefend is celebrating its second consecutive year as one of the fastest-growing companies on the First Coast. Despite the challenges of the past few years, we are proud to announce that we have achieved the 14th spot!
OnDefend named 14th fastest growing company on the First Coast
BlindSPOT

Did you miss our inaugural BlindSPOT newsletter? We are constantly updating the product from simulation libraries to new reporting graphics. This bi-monthly newsletter is meant to give every user an understanding of what’s new and what to expect in regard to updates. Here’s a sneak peek of what to expect in next month’s newsletter from OnDefend CTO Ben Finke:
“We’re always looking to build tools that helps you keep your organization safe. BlindSPOT attack simulations do a great job helping you find “blindspots”, but once you have those fixed, how do you make sure they stay fixed? Stay tuned for our next newsletter where we tell you all about Alert Validation.”
Missed out on last months? Catch up now.
BlindSPOT Newsletter: The Inaugural Edition > OnDefend
Anybody else feel like we just scratched the surface? That’s because we did. Stay tuned for this bi-monthly newsletter, for all of OnDefend’s latest and greatest.
If you want to stay in the loop about what’s happening at OnDefend, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
There is no doubt plenty of horror stories working in cybersecurity. For cybersecurity awareness month and Halloween, we teamed up with industry leaders and partners and asked them a simple question, “tell us a cybersecurity horror story.”
” When I first got into the field as an admin, I was informed that one of our Domain Admin accounts was a user called ‘hdesk’ and the password was ‘help’ and everyone in the company was aware of it. And I mean EVERYBODY! You can imagine how that went over at our security audit. Suffice to say, it was changed shortly after that.” – Daniel Lowrie, IT Pro TV
” I once got a call from one of our vendors telling us they found the entire code of one of our critical applications including secrets in clear text in an open GitHub repository. The developer thought the GitHub repo was secure by default. This became an escalated incident of course but also a great opportunity to educate developers on secure coding practices. ” – VCISO Carlos Rodriguez
” Client had serious concerns regarding the physical security controls of their main campus. My team was engaged to attempt to breach the primary building with no stated limitations.
The client’s facility was a large campus comprising multiple buildings supporting various corporate functions and operations. Upon completion of the reconnaissance phase, it was determined that we’d attempt to scale the first story of the target building via grappling hook and climbing gear.
Literally picture Batman & Robin slowly walking up the side of a building and that is exactly what we looked like, minus the costumes.
Upon gaining a successful foothold with the grappling gear and securing the belay lines, we began our single-story ascent. Within minutes, we noticed the beam of a flashlight slowly approaching our position and with the belay lines dangling on the ground, there was no mistaking what we were up to!
This is where the story gets good, so the security guard, Chad, approaches us and demands we come down. Once back on the ground knowing full well that our cover was about to be blown, we throw caution to the wind and tell Chad at least most of the truth, that we’re here on a consulting engagement. Fully expecting Chad to raise the alarm to call the police, we were in total shock when Chad said “Okay, cool, but please be careful not to damage the building.
Um, wait what? Chad never asked us for identification, a get of jail free letter or even our names!
So once the coast is clear, we return to our superhero’s scaling that daunting first story wall. Upon reaching the summit a solid 12-15 feet above ground, we stumble over the perimeter wall and discover an exterior glass door leading into an employee break room, adjoining what turned out to be the primary data center!
Once inside, we were successful in gaining access to pretty much the entire facility without being challenged again by Chad.
The irony of this cyber horror story is that the client was a security firm and the lack of any semblance of security awareness by their security officer underscores the fact that even security companies are vulnerable to the same tactics & techniques that malicious threat actors utilize, regardless of their target or intentions.” – Todd Salmon, Cybersecurity executive and former CISO
” During a recent Ransomware attack, we noticed threat actors stealing administrative credentials and logging on to security portals to disable EDR products within their environment. They used a weakness and privileged access management to uninstall security agents without the victim’s knowledge, until after the security incident had occurred. These attackers were even responding towards threats in the portal to avoid suspicion. Eventually they locked out the customer from their own security portal and executed Ransomware within the environment taking the company down.” – Josh Nicholson, DeepSeas VP
” One that I remember really vividly, we did some work with an insurance provider a property insurance company and we demonstrated that in the web app they put on the Internet for all their policyholders and their agents to use that it was possible to sign up for a free account, gain access to other people’s information, and then actually act as a not only an agent but actually somebody for the company to create our own claim, approve our own claim and mail ourselves a check. All that happened 5 vulnerabilities we found in the web application.” – Ben Finke, OnDefend CTO
Whether you need a Ransomware readiness assessment or advanced email phishing training, OnDefend can provide any professional service your company may need. Check out a full listing of our services here: Services > OnDefend
Many believe a cybersecurity company is filled with a bunch of people furiously typing while wearing hoodies (not completely untrue) but there is so much more!
We’re introducing you to different employees within the OnDefend company to encourage others to explore a career in cybersecurity.
Name: Ben Finke
Title: CTO, OnDefend
Name: Zac Hardy
Title: Senior Project Manager, OnDefend
Name: Lauren Verno
Title: Vice President of Communications, OnDefend
Name: Chris Freedman
Title: CEO, OnDefend
Name: Billy Steeghs
Title: COO, OnDefend
About OnDefend:
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world threats. From ensuring compliance with industry standards to building out mature security programs our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, please visit OnDefend.com.
Security Monitoring Validation was built out of a need from our customers to see how long it would take their security controls to detect an attack and then how long it would take for their 3rd party provider to respond.
We quickly found the need was not a singular event. A recent survey found the average response time for MSSPs to security incidents is 3 hours. However, the study also found that 20% of MSSPs take more than 12 hours to respond to security incidents.
By leveraging OnDefend’s breach & attack simulation solution, BlindSPOT, our professional services team is able to safely simulate ransomware, supply chain, and other adversarial tactics every month to prove a third-party security provider or internal defense team will detect, respond, and alert to real- world cyber-attacks within the organizations selected time frame.
A customer success example:
Problem: What is our mean time to detect (MTTD) and mean time to respond (MTTR)?
Background: This customer was concerned about reports of similar organizations’ internal network defense teams and outsourced 3rd party MSSP’s providers response to cyber-attacks, which resulted in critical delays and sometimes complete response failures.
Actions Taken: BlindSPOT was used to perform the service Security Monitoring Validation where various threat actor attack vectors are simulated on an environment to validate, their real-time detection, alerting, and response readiness as if it was a real event.
Result: The attack simulation report revealed the EDR was missing attack activity, when the EDR did successfully detect an attack, the logs were being directed to the EDR’s own console rather than the SIEM. The MTTD for the attacks that were logged was 5 hours. Following remediation of the of the misconfigurations the MTTD was 2 minutes.
Customer Reflection: “I was blown away by how long it took for our system to detect an event and reach the screen of the analysts who was responsible to respond. If it had been a real attack, our original detect and response time of 5 hours would have potentially cost us millions, not to mention losing that sensitive data. Now, if our EDR and SIEM have a detection or response failure, we’ll know.” – Vice President of Information Security, International Technology Corporation
Instantly download a demo here: Security Monitoring Validation
A Note from the CTO
We’ve been hard at work on all things BlindSPOT and wanted to share just a few of the highlights with you.
As you’ll see in this update, the BlindSPOT team continues to build out new features and functionality that make conducting Breach and Attack Simulation style testing easier, while reducing the time and friction to get to the results. A lot of the features and changes you’ll notice when using the platform came directly from the feedback of our customers, so thank you, and keep it coming.
-Ben Finke

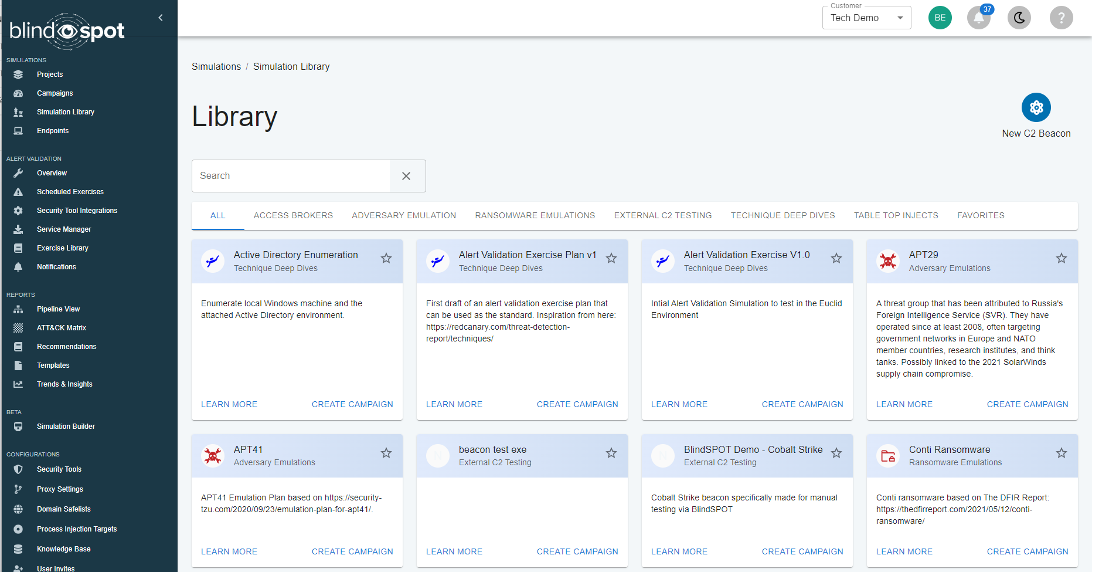
Simulation Library Updates
Our Simulation Library has been completely redesigned to make it easier to find the simulations you need to test your defenses and train your team. The new look and feel makes it easy to find and start campaigns, and you can even create your own favorites list for suture workshops.
Simulation Builder Updates
Our beta release of the Simulation Builder is getting better every day, thanks to your feedback (please, keep it coming)!
The new interface makes it easy to add new steps to your simulations and to create or modify existing steps.
Here are some of the key improvements:
- Easy step placement: You can now easily pick where you want to add new steps in your simulation. Simply click on the “+” button at the desired location, and a new step will be added.
- Cleaner and simpler step creation: Creating and modifying steps is now easier and faster. The new interface is more organized and user-friendly, so you can focus on your simulation instead of the tools.
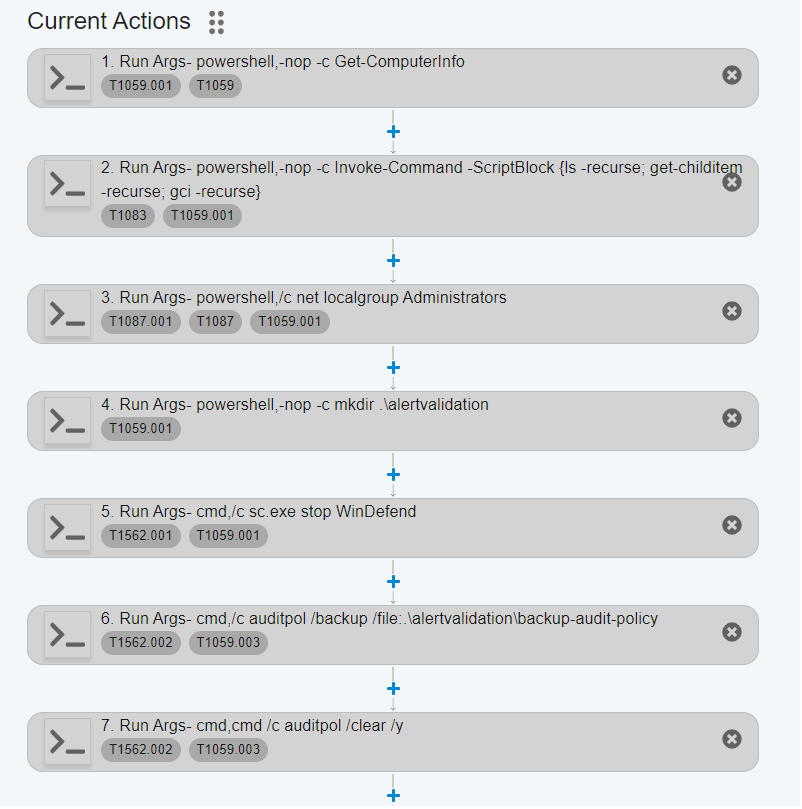

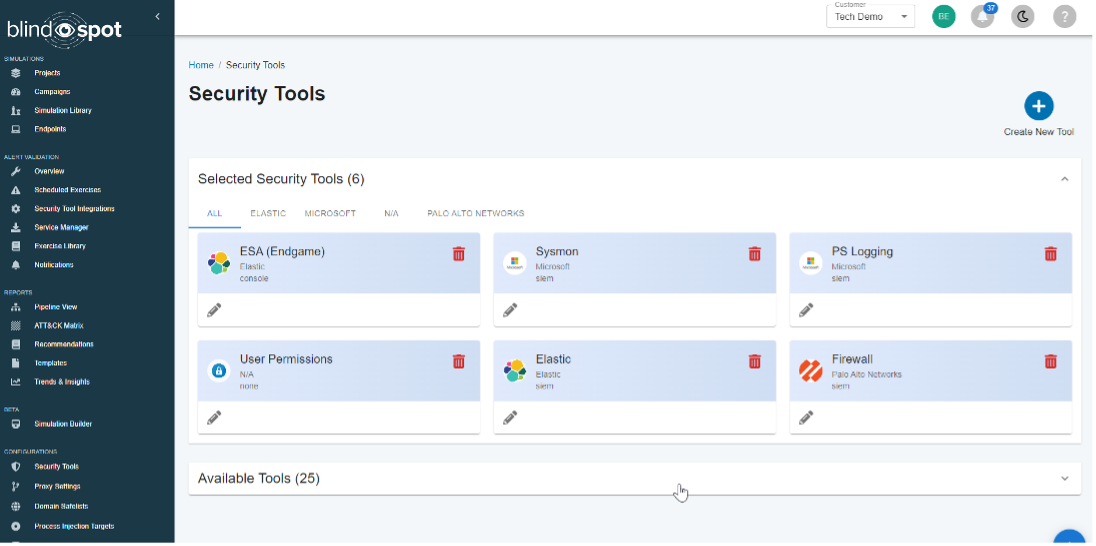
New Security Tools Catalog
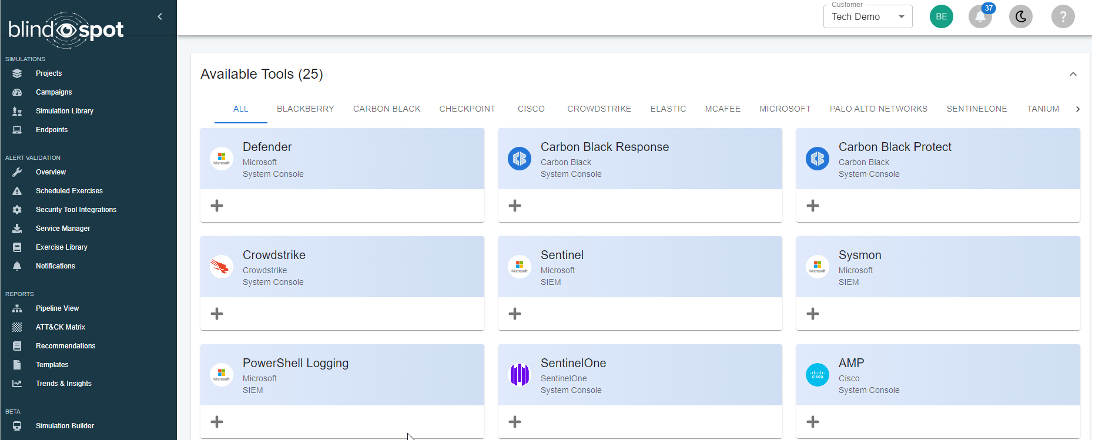
We’ve updated our security tools area to give you a better view of your current tools and to suggest new tools that you may want to consider.
Here are the key changes:
- Improved view: Your current security tools are now displayed in a more organized and easy-to-read format.
- Suggested tools: We’ve prepopulated a list of security tools that you may want to include, based on your current setup and industry best practices.
If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
Originally written for Jacksonville Business Journal by James Cannon
For more than 25 years, the Jacksonville Business Journal has identified the fastest growing companies on the First Coast.
This list has tracked companies that boomed during the good times, that grew even when the economy shrank, that stand as an example of what ingenuity, hard work and creativity can lead to.
This year’s list of honorees are drawn from a range of industries, including real estate, transportation, technology and manufacturing.
As a group, the Fast 50 honorees saw their revenue grow by more than $2 billion collectively over the past three years.
OnDefend made a significant leap up the rankings this year, taking home the coveted 14th spot, a one-position improvement from last year.
Founded in 2016 by Co-Founders Chris Freedman & Ben Finke, OnDefend started as a service company but has quickly become a leader in the SaaS space with their attack simulation tool, BlindSPOT.
In this interview with the Jacksonville Business Journal, Freedman explains what this milestone means to the company.
What led you to the point of starting or buying into a company? “I wanted to change the world in a positive way and watching companies being devastated by cyber criminals inspired Ben and myself to launch OnDefend so that we could help companies around the world secure their future.”
What has been the biggest challenge you’ve overcome as you’ve grown? Covid was not easy for any company to endure, but being followed by an economic downturn has made growth at the scale I would prefer extremely difficult.
What’s been the ‘secret sauce’ that has helped propel your growth? Identifying niche markets in our industry and executing effectively within them.
What have you done to keep your company culture strong as you grow? Our core values which are Passion, Creativity, Humility, Motivation, Integrity and Authenticity.
What advice did you receive earlier in your career that has stuck with you as you lead your company? Know what your customers want most and what your company does best. Focus on where those two meet.
What advice would you have for those who are looking to lead a fast-growing company? Find a strong niche through market research and build a team of smart people to execute your vision and mission in a sustainable way.
What challenges or opportunities do you see on the horizon and how are you preparing for them? Spinning out a SaaS business from a service-based organization and scaling both independently during an economic downturn.
Link to original article: 2023 Class of Fast 50: Ondefend
It is about to be busy season for cyber security providers around the world. From non-stop conferences and awards to new vulnerabilities and cybersecurity awareness month. Let’s get started.
OnDefend Insights
It’s likely one of the most common questions our in-house red team gets asked, “how did you become an ethical hacker?” In today’s job market it seems as if entry-level cybersecurity jobs are non-existent, but how do you become a seasoned professional without the experience? OnDefend senior tradecraft engineer Ryan Tucker created a how-to guide on becoming a hacker, and his advice to others on growing their careers.
Becoming an Ethical Hacker > OnDefend
——
A recent report revealed less than a quarter of CISO’s are participating in business strategy and decision-making processes within their organization (I know what you’re already thinking, that doesn’t shock you at all.) Here’s what you might not have expected, the report showed cybersecurity budgets are increasing but there was a catch to receiving that budget. You can read the full report here.
Cybersecurity budgets are increasing, yet CISO’s are still not invited to the boardroom. > OnDefend
——
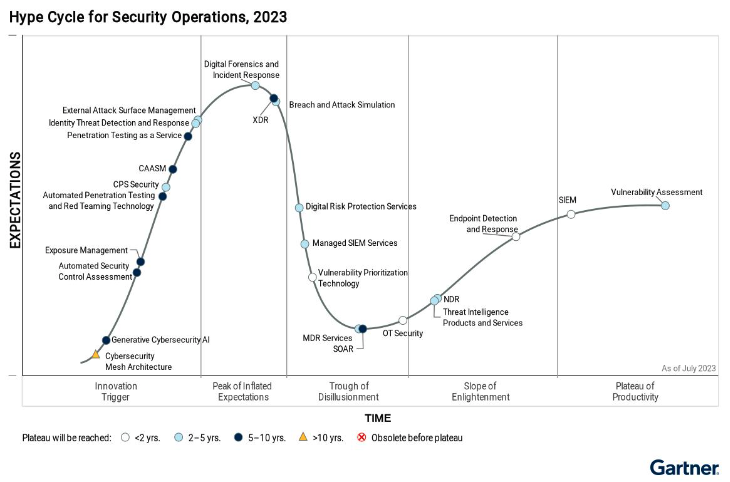
Breach & Attack Simulation or BAS technology is at peak interest according to Gartner’s 2023 security operations hype cycle. BAS technology provides automated and consistent assessment of an enterprise’s threat vectors. Frequent automated BAS assessments also enable organizations to detect gaps in their security posture due to configuration errors or reevaluate priorities of upcoming security investments.
What makes OnDefend‘s BAS tool BlindSPOT stand out from the competition?
⭐️ Can be offered as a one-time attack simulation or a fully managed service
⭐️ Competitively priced compared to other BAS products
⭐️ Allows for customized payloads, C2 integrations, and stakeholder reporting
Visualize the power of removing these “blind spots” here.
Visualizing the Power of BlindSPOT > OnDefend
Cybersecurity Roundup: Top Stories from the Digital Frontlines
Microsoft says Storm-0558 Chinese hackers stole a signing key used to breach government email accounts from a Windows crash dump after compromising a Microsoft engineer’s corporate account.
Hackers stole Microsoft signing key from Windows crash dump (bleepingcomputer.com)
—
CISA confirms the addition of Peiter ‘Mudge’ Zatko to its roster of prominent voices preaching the gospel of security-by-design and secure-by-default development principles. According to CISA director Jen Easterly Mduge was brought on to “shape a culture of security by design that is foundational to every security team, every C-suite, and every board room in the country.”
CISA Hires ‘Mudge’ to Work on Security-by-Design Principles – SecurityWeek
—
Leading cybersecurity agencies from the UK, US, Australia, Canada, and New Zealand have discovered that the Sandworm cyber actor used a new mobile malware, “Infamous Chisel,” to target Android devices used by the Ukrainian military. They have previously connected Sandworm to Russia’s GRU Main Centre for Special Technologies (GTsST), indicating state-sponsored involvement in these cyberattacks.
Infamous Chisel Malware Analysis Report | CISA
—
The patch didn’t work. The FBI warns that Barracuda Email Gateways continue to be vulnerable despite attempts at a recent solution to the zero-day bug. According to the FBI, the fixes are considered “ineffective” and that it “continues to observe active intrusions and considers all affected Barracuda ESG appliances to be compromised and vulnerable to this exploit.”
Urgent FBI Warning: Barracuda Email Gateways Vulnerable Despite Recent Patches (thehackernews.com)
OnDefend in the News
“Hard work, consistency, curiosity, a positive attitude, and a desire to grow. All qualities that are needed to ensure an organizations growth.” OnDefend Co-Founder/CTO Ben Finke reflects on his leadership after being named one of the 2023 tech leaders of the year. If you’ve ever met Ben, you recognize his leadership combined with his technological savvy is unmatched. Check out his full interview.
2023 Tech Leaders: Ben Finke of OnDefend > OnDefend
BlindSPOT

We have some very exciting news on the BlindSPOT front that we will be announcing next month, from simulation library updates to a new security tools catalog. In fact, there is such a steady flow of updates, we figured the BlindSPOT section should have a page of its own. Consider this your foreshadowing to the big announcement next month. – Ben, OnDefend CTO
Anybody else feel like we just scratched the surface? That’s because we did. Stay tuned for this bi-monthly newsletter, for all of OnDefend’s latest and greatest.
If you want to stay in the loop about what’s happening at OnDefend, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.
Originally written for Jacksonville Business Journal by James Cannon
JACKSONVILLE, Fla. –For the past five years, the Jacksonville Business Journal has honored some of the men and women whose technology leadership has helped local organizations grow, deal with challenges and shape the future.
We’re glad to have this opportunity to spotlight these leaders and their accomplishments, and we look forward to seeing the impact they and their organizations have on the community in the future.
Name: Ben Finke
Company: OnDefend
Title: Co-Founder and CTO
How has your leadership helped your organization grow? Hard work, consistency, curiosity, a positive attitude, and a desire to grow. All qualities that are needed to ensure an organizations growth. I will start by saying, the product and services our company offers has such an important need in every sector of business. A good product, like BlindSPOT will naturally lead to business growth but it was the above attributes that led to this product being built successfully and my continued desire to grow to teach others about it.
As the BlindSPOT product has gained new capabilities and we’ve expanded the content available we’ve added new customers, allowing us to reinvest that into more development and content capacity. Over the years our company has grown in employee count, financial revenue, and brand awareness. My willingness to continue to teach others and continually push the envelope has led us to where we are today and I know will only push is further to come.
What is your greatest career accomplishment? I’ve been very fortunate to work on several amazing projects and with some amazing people over my career, but in 2021 we were asked to help secure the upcoming FIFA World Cup in Qatar. In cybersecurity you’re not always allowed to mention the companies or organizations you’re working with for security reasons. This was one of those projects that for well over a year, my team worked tirelessly to make this event a success. It was one of those projects that if we did not do our job correctly, one of the most famous sporting events in the world would be in trouble. The OnDefend name was at stake, and we knew we had to get it right. In cybersecurity, no news is good news. The fact, that a cyber-attack on a global stage didn’t hit the news means we did our job correctly. To know that our company has reached a level to be selected for that kind of project and pull it off successfully is something I could have only dreamed of when I started my career.
OnDefend Media Contact: Lauren Verno, Lauren.verno@ondefend.com