[Webinar] Reimagining Ransomware Defense: Revealing and Removing the Hidden Risks of Security Control Failures
Are Your Security Controls Working Right Now? Let’s Prove It.
Read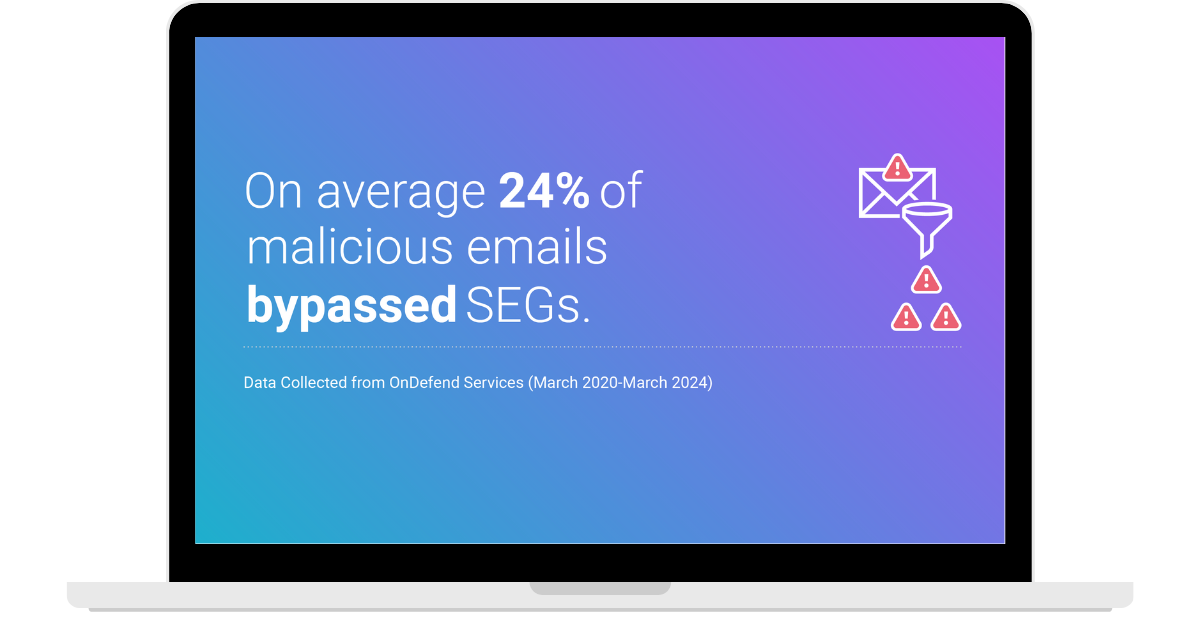
Email phishing is now the #1 ransomware attack vector—and if you’re responsible for managing a Secure Email Gateway (SEG), you know the frustration of seeing malicious emails bypass filters despite your best efforts.
You’re not alone.
Many organizations deploy industry-leading SEGs, yet they still struggle with phishing and ransomware delivery attempts slipping through. Why? Because email security isn’t a set-it-and-forget-it solution—it requires constant testing, fine-tuning, and adaptation to evolving threats.
Let’s break down why SEGs miss threats, what you can do to strengthen your defenses, and how continuous ransomware defense validation can prove whether your SEG is actually working as intended.
Today’s phishing emails aren’t the sloppy, typo-ridden scams of the past. Threat actors continuously test their payloads against multiple SEGs to find what gets through. Some of their most effective evasion techniques include:
Many organizations deploy SEGs with default settings, assuming their vendor’s out-of-the-box policies will protect them. But every environment is different, and failure to fine-tune filters leads to missed threats. Common configuration issues include:
A SEG is only as good as its last real-world test. Many organizations assume their SEG is working—until a ransomware attack proves otherwise. The only way to know for sure is through continuous validation that simulates real-world phishing and malware delivery attempts to test whether your SEG is actually blocking what it should.
In a recent webinar, Reimagining Ransomware Defense: Revealing and Removing the Hidden Risks of Security Control Failures, OnDefend CEO Chris Freedman discussed why SEGs commonly fail. Here’s a short clip:
The best way to identify weaknesses is to actively test your SEG with the same techniques attackers use. OnDefend’s Ransomware Defense Validation (RDV) includes comprehensive SEG testing, helping organizations:
Once you identify the gaps, it’s time to optimize your SEG configuration:
If your SEG consistently fails real-world attack simulations, it may be time to evaluate other vendors. Not all SEGs offer equal protection, and some provide better:
Email is still the cybercriminal’s favorite playground, and your Secure Email Gateway (SEG) is supposed to be the bouncer at the door. But let’s be real—how often do you check if that bouncer is actually stopping the bad guys?
Your SEG isn’t magic—it’s only as good as the rules and configuration you set and the tests you run. Don’t assume it’s got you covered just because it’s there. It’s definitely not a set-it-and-forget-it security control. Get hands-on, put it through the wringer, and make sure it’s actually keeping your inbox safe. Because when it comes to email security, guessing isn’t good enough.
Or better yet, let OnDefend do it for you with real-world phishing and malware testing. SEG testing is inexpensive and a super small lift on your end (just set up an inbox for our tester). Once we have access to the email, we send hundreds of malicious payloads your way. We’ll assess for the risks of spoofing, non-repudiation, and as a threat vector, and after a 7-day testing period, we’ll provide a full report. Get in touch with OnDefend today to get started.
—–
Resources: https://blog.knowbe4.com/heads-up-email-phishing-is-now-the-top-ransomware-attack-vector