Watch Full Webinar Recording
Security Monitoring Validation: We safely simulate ransomware, supply chain, and other adversarial tactics every month to prove your security provider or internal defense team will effectively detect, respond, and alert you to real- world cyber-attacks.
Special Alliance Offer: $2,000 one-time assessment.

How Security Monitoring Validation Works

Every month we safely simulate a real-world cyber-attack using our attack simulation tool, BlindSPOT.
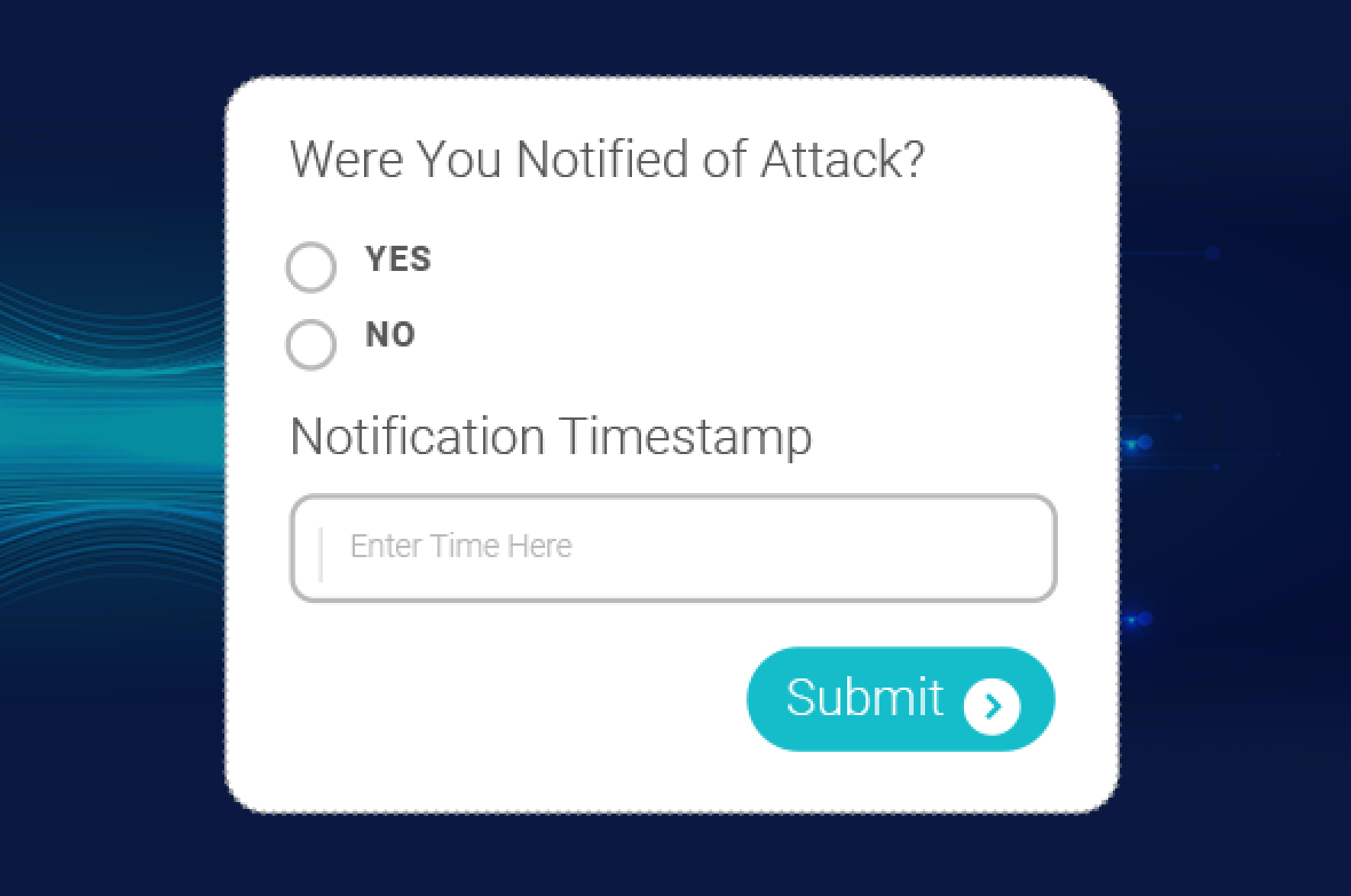
You confirm if and or when your provider responds and notifies you.

You receive a comprehensive defense success or failure report.
5 out of 10 engagements result in an attack notification response delay or failure.

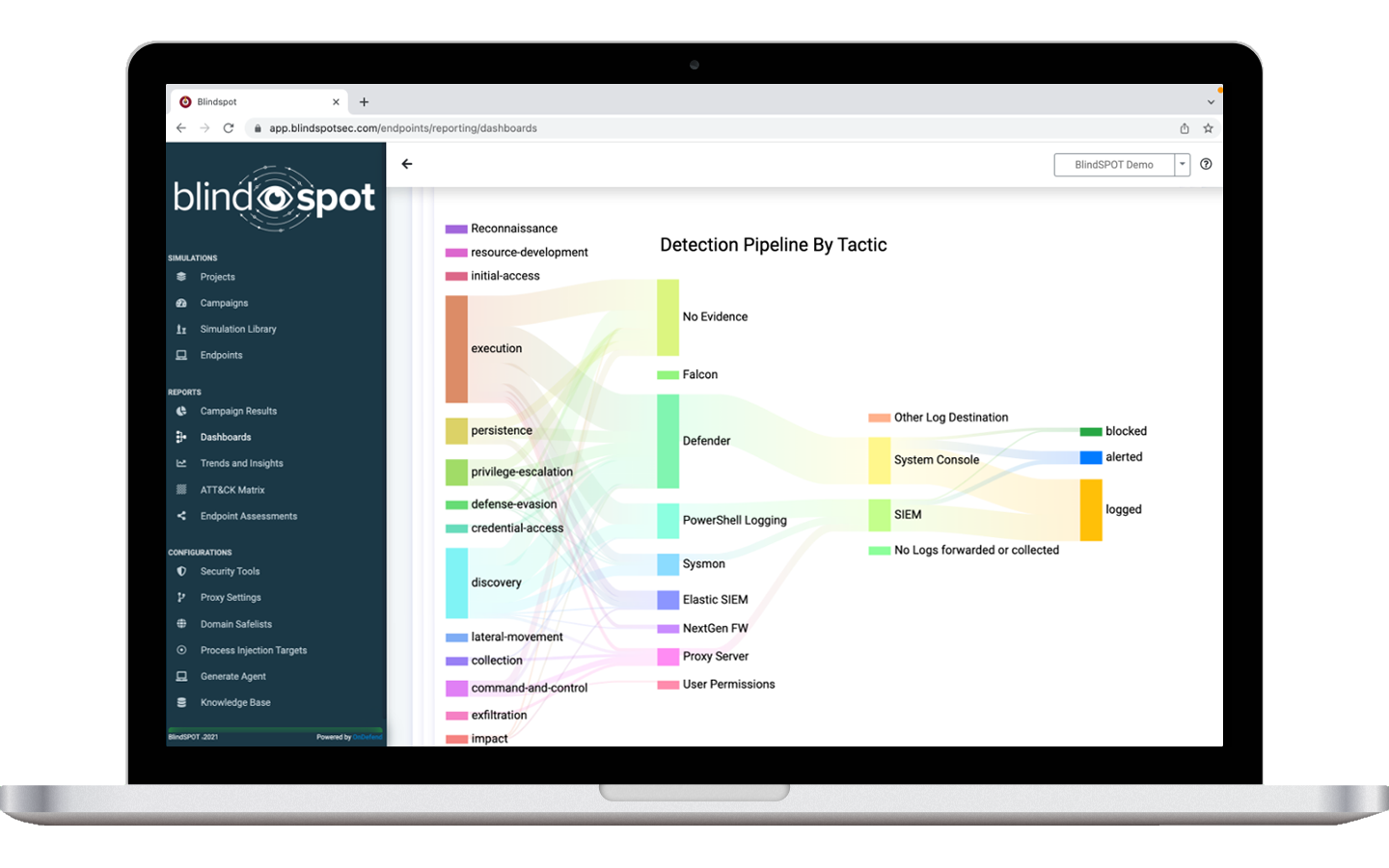
Security Monitoring Validation & BlindSPOT
About BlindSPOT: BlindSPOT is a global breach and attack simulation solution that safely simulates real-world cyber attacks and verifies an organization’s defensive investments are working.
Unlike other BAS products who typically only serve Fortune 500 companies. BlindSPOT’s Security Monitoring Validation feature provides a way for enterprises, mid-market, and SMB’s to prove their internal network defense team or 3rd party MSP, MSSP, XDR or MDR provider is protecting their organization every month.

Additional Services We Offer
- Vulnerability Management
- Comprehensive Risk Assessments
- Network Penetration Testing
- Cloud Security Assessment
- Red Teaming
- Tabletop Exercises
- Purple Teaming
- Tabletop Exercises w/ Attack Simulations
- Managed Breach & Attack Simulations
- Virtual Chief Information Security Officer
- Application Vulnerability Management
- Security Tool Rollouts
- Application Penetration Testing
- Security Tool Bakeoffs
- Cloud Vulnerability Management
- SOC Optimization Assessment
- Phishing Testing & Training
- Compliance Gap & Readiness
- Email Filter Testing
- Assessments Firewall Analysis
- Social Engineering
- IR Program Development
- Physical Penetration Testing
- Policy Development Remote
- Compromise Assessment Testing
- Access Assessments


What Our Clients Say
“It’s something I really wish I would have invested in years ago, because in my 22 years in IT. Now, for percentage points of my defensive security spend, I can get ongoing validation it is working and worth the investment.”
“I used to have limited insight into whether my technical security controls we’re working, now I have full visibility and reassurance on a continual basis.”
“You’ll be surprised by what they’re going to reveal, I promise that. But, I can say now I sleep a hell of a lot better.”