What’s New with OnDefend & BlindSPOT
Our focus for the year has never been clearer: prove the investments you pay for work as you expect.
Whether that be your email gateway, EDR, or even the response times from your third-party vendors, we understand teams lack bandwidth, that every dollar counts, and the stakes have never been higher in proving your organization is going above and beyond compliance to keeping operations safeguarded.
Here are some of the new projects we’ve been working on, including Ransomware Defense Validation and highlights that have set OnDefend and our in-house breach and attack simulation tool BlindSPOT apart from the rest.
The Hidden Risks of Security Control Failures: What Security Teams May Unintentionally Be Missing
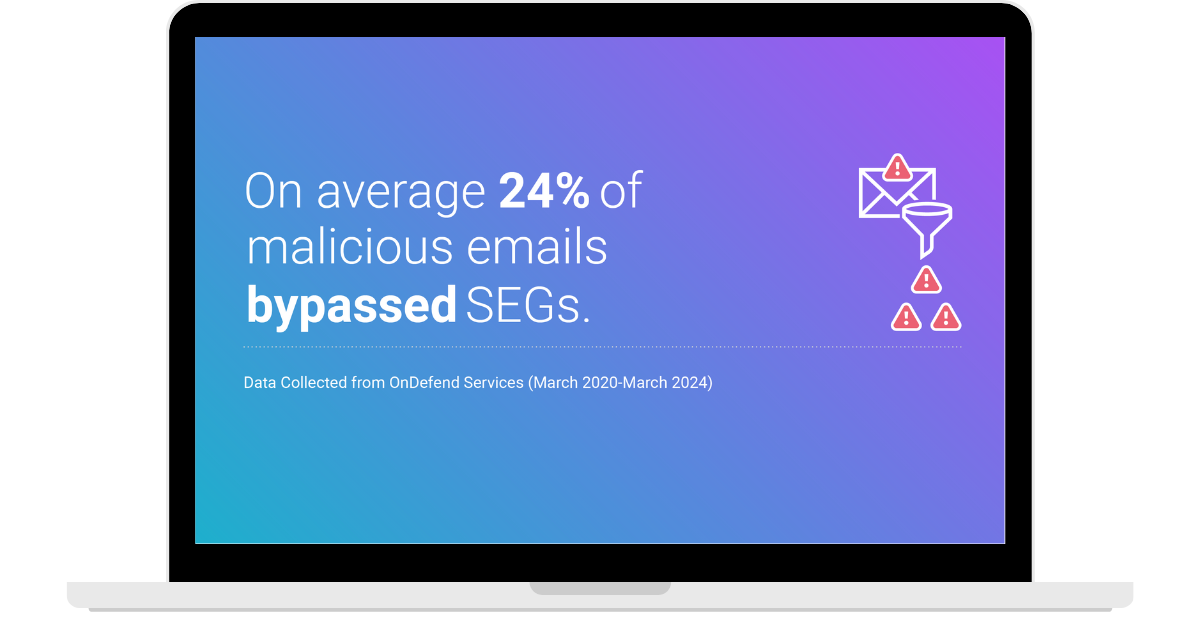
Are your security controls actually working? OnDefend analyzed security control failures across critical tools security teams rely on daily. The results:
- Secure Email Gateways (SEGs): On average, 24% of malicious emails bypass SEGs
- Threat Detection Tools (EDR, XDR, SIEM): 7 out of 10 attack simulations identified security tool misconfigurations or exploitable control failures
- Threat Response Teams (MDR, NDR, Internal Teams): 5 out of 10 of attack simulations resulted in no response or a delayed response outside SLA requirements
Read: Understanding the Root Causes of These Failures
[Webinar] Reimagining Ransomware Defense: Revealing and Removing the Hidden Risks of Security Control Failures

Did you miss our recent webinar with Baptist Health CISO James Case and OnDefend CEO Chris Freedman? Inspired by real conversations between healthcare leaders, Ransomware Defense Validation (RDV) was built as a proactive solution tailored to identifying those security control failures.
In this webinar, you’ll:
- Understand how & why prevention, detection & response security control failures occur.
- See results within a hospital system that implemented RDV
- Share actionable steps to prove your security controls work and provide a real-world ROI
Watch Here
[Case Study] Prominent Healthcare System Implements Ransomware Defense Validation
Learn how a leading U.S.-based healthcare system enhanced its ransomware resilience by validating security controls, ensuring vendor accountability, and strengthening defenses to protect critical patient data and care continuity.
“Ransomware Defense Validation plays a crucial role in building a robust, resilient, and trustworthy healthcare organization. You can’t eliminate all risk, but you can reduce it to safeguard patients and their sensitive data while maintaining their trust so we can focus on what matters most: patient care.” – Healthcare Chief Information Security Officer (CISO)

See the Results

Message from BlindSPOT’s CTO
One of the great joys in building anything is seeing the things that once existed only on a whiteboard work in the real world. I’m always amazed at how the development and tradecraft team can take a whisper of an idea and then be ready to demo it a short time later. Demo day for new features is always amazing, and one of my favorite things about writing this newsletter is that I get to share this great work with all of you.
BlindSPOT, our breach & attack simulation tool is completely written in house by our development team. That gives us incredible flexibility to add new features, change an interface, or integrate with a new tool. But the best part is that we can add these based on your feedback. If you’ve got a thought on something that would help you make BlindSPOT even more useful, we’re happy to hear it!
Project Level Security Tool Log Upload
We previously shared the ability to upload security tool logs at the campaign level. This is a great way to save time without having to go through the full API integration with a security tool.
This feature lets you export activity (in whatever the standard format for the tool is) and upload it to BlindSPOT.
BlindSPOT will then match that information with the campaign and automatically score your campaign for you. And now, we’ve introduced that at the project level too.
Let BlindSPOT handle scoring the entire project through file uploads.
Upload Security Tool Logs
You’ll see a list of all of the tools you have configured in your BlindSPOT tenant:
BlindSPOT Tenant
New Agent Software in Beta Testing
The BlindSPOT agent (or implant) is the only part of the BlindSPOT platform that must be deployed onto the system in order to execute activity on it. We’ve released a brand-new version of our implant in beta mode for you to test.
Among other things, it generates a smaller payload, improved detection evasion techniques, and runs without a front-end UI for improved execution in non-interactive modes. Try it on your next workshop.
BlindSPOT Agent- Implant
BlindSPOT Satellite
We’ve long had the ability for BlindSPOT simulations to attempt to exfiltrate data and download content from the Internet. But facilitating those actions either meant using public sources (out of our control – never a good idea) or having to stage the necessary services on the Internet to handle file hosting or uploads. We’ve been hard at work designing a way to make this easier.
The result is something we are calling Satellite – a specialized app that you can host on any Windows or Linux server and instantly be prepared to test exfiltrating files or downloading content as part of your simulations.
Best of all, you are in complete control of the execution of the Satellite – it runs on systems under your control and when you want it. It allows us to quickly move to new IP addresses and domains that have never interacted with your organization before, to see how your tools would handle that type of activity. Oh, and it will also act as a C2 relay, so your implants don’t have to phone home directly to the BlindSPOT server. Currently released in limited beta testing, we expect to have this out to all BlindSPOT customers soon.
Welcoming New Talent to OnDefend
OnDefend Welcomes Carly Sherrod as Director of Threat Intelligence and Programs

With extensive experience in cybersecurity, intelligence, and incident response, Carly will play a pivotal role in enhancing OnDefend’s threat intelligence capabilities and program development.
Previous Leadership Roles:
- Interim State Chief Risk Officer & Chief Information Security Officer (CISO) of North Carolina – Oversaw state-wide cybersecurity infrastructure.
- Former Deputy State Chief Risk Officer & Chief Information Security Officer
- Principal Consultant at CrowdStrike – Led digital forensics and incident response (DFIR) efforts against global cyber threats.
Meet Carly
Thank you for taking the time to read our updates. We are committed as an organization to continue pushing boundaries within the world of innovation. OnDefend & BlindSPOT are the products of that. If you would like to learn more or have any suggested recommendations, please reach out: Contact Us.