OnDefend: Lauren Verno, Vice President of Communications & Marketing
Media@ondefend.com | Lauren.verno@ondefend.com | 904-299-3669
JACKSONVILLE, Fla.–(BUSINESS WIRE)– OnDefend, a leader in preventative cybersecurity testing and advisory services, today announced the launch of its Ransomware Defense Validation (RDV) service. Developed with direct input from prominent healthcare Chief Information Security Officers (CISOs) and launched in collaboration with major healthcare systems, RDV addresses the pressing need for organizations to proactively defend against ransomware threats.
The healthcare community faces a new pandemic—a cyber one—and the risks to patient safety, data security, and operational continuity have never been greater. As a managed service, RDV, powered by BlindSPOT, OnDefend’s proprietary Breach and Attack Simulation (BAS) platform, equips organizations to regularly test and validate the effectiveness of their prevention, detection, and response security controls against known and emerging threats.
Data collected from OnDefend’s global security testing services found:
RDV originated from conversations between OnDefend’s security teams and healthcare leaders who shared concerns about common security control failures and the lack of regular visibility and validation.
“Cybersecurity isn’t about setting up defenses and hoping for the best. It’s about constantly testing, adapting, and staying ahead of threats. If you’re not testing your security, the attackers will do it for you,” said Larry Whiteside Jr., former CISO at Spectrum Health and Women’s Care OBGYN.
These discussions highlighted the need for a proactive solution tailored to the unique challenges of healthcare cybersecurity, going above and beyond current healthcare standards and regulations.
RDV is delivered by OnDefend as a managed service using BlindSPOT to safely simulate real-world ransomware attacks on a healthcare systems’ defenses to prove their:
Secure Email Gateways (SEGs): effectively filter malicious emails from reaching employee inboxes.
Threat Detection Tools (EDR, SIEM): effectively identify and alert security teams to real-world attack activity.
Threat Response Teams (SOC,MDR,NDR): immediately respond and neutralize real-world cyber threats in real-time.
“Ransomware Defense Validation provides security leaders with critical visibility into their defensive investments, ensuring they are resilient against the cyber threats targeting their industry,” said Chris Freedman, CEO of OnDefend. “The goal of this managed service is to validate security tools and hold monitoring vendors accountable, all while empowering our customers to demonstrate they are achieving the return on investment they deserve.”
Early access customers who implemented RDV found their security teams’ overall posture improved, showcased continuous risk reduction, proved return on investments, and are prepared to safeguard essential healthcare operations.
Read the case study: Prominent Healthcare System Implements Ransomware Defense Validation to Safeguard Patient Safety
and Data Security
This service is now available to healthcare organizations nationwide.
To further understand Ransomware Defense Validation, we invite you to explore our additional resources here: https://ondefend.com/blindspot/ransomware-defense-validation/
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of BlindSPOT, its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform. OnDefend is a trusted partner, empowering organizations globally to combat real-world cyber threats proactively. From ensuring compliance with industry standards to building out mature security programs, our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about our services and solutions, please visit www.ondefend.com.
OnDefend on Social Media
Contacts
OnDefend Media Contact:
Lauren Verno
Media@ondefend.com
904-299-3669
Whether that be your email gateway, EDR, or even the response times from your third-party vendors, we understand teams lack bandwidth, that every dollar counts, and the stakes have never been higher in proving your organization is going above and beyond compliance to keeping operations safeguarded.
Here are some of the new projects we’ve been working on, including Ransomware Defense Validation and highlights that have set OnDefend and our in-house breach and attack simulation tool BlindSPOT apart from the rest.
Are your security controls actually working? OnDefend analyzed security control failures across critical tools security teams rely on daily. The results:
Read: Understanding the Root Causes of These Failures

Did you miss our recent webinar with Baptist Health CISO James Case and OnDefend CEO Chris Freedman? Inspired by real conversations between healthcare leaders, Ransomware Defense Validation (RDV) was built as a proactive solution tailored to identifying those security control failures.
In this webinar, you’ll:
Learn how a leading U.S.-based healthcare system enhanced its ransomware resilience by validating security controls, ensuring vendor accountability, and strengthening defenses to protect critical patient data and care continuity.
“Ransomware Defense Validation plays a crucial role in building a robust, resilient, and trustworthy healthcare organization. You can’t eliminate all risk, but you can reduce it to safeguard patients and their sensitive data while maintaining their trust so we can focus on what matters most: patient care.” – Healthcare Chief Information Security Officer (CISO)

One of the great joys in building anything is seeing the things that once existed only on a whiteboard work in the real world. I’m always amazed at how the development and tradecraft team can take a whisper of an idea and then be ready to demo it a short time later. Demo day for new features is always amazing, and one of my favorite things about writing this newsletter is that I get to share this great work with all of you.
BlindSPOT, our breach & attack simulation tool is completely written in house by our development team. That gives us incredible flexibility to add new features, change an interface, or integrate with a new tool. But the best part is that we can add these based on your feedback. If you’ve got a thought on something that would help you make BlindSPOT even more useful, we’re happy to hear it!
We previously shared the ability to upload security tool logs at the campaign level. This is a great way to save time without having to go through the full API integration with a security tool.
This feature lets you export activity (in whatever the standard format for the tool is) and upload it to BlindSPOT.
BlindSPOT will then match that information with the campaign and automatically score your campaign for you. And now, we’ve introduced that at the project level too.
Let BlindSPOT handle scoring the entire project through file uploads.
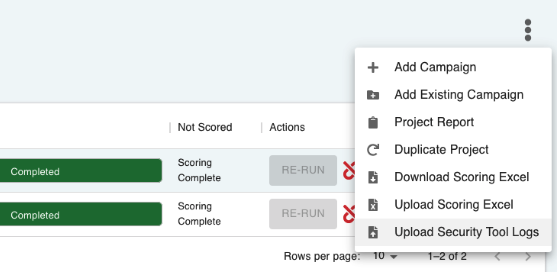
Upload Security Tool Logs
You’ll see a list of all of the tools you have configured in your BlindSPOT tenant:
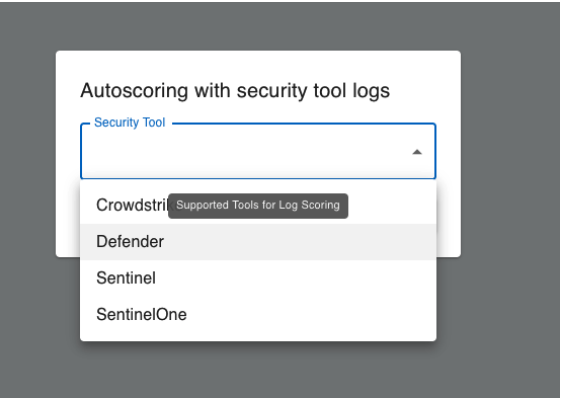
BlindSPOT Tenant
The BlindSPOT agent (or implant) is the only part of the BlindSPOT platform that must be deployed onto the system in order to execute activity on it. We’ve released a brand-new version of our implant in beta mode for you to test.
Among other things, it generates a smaller payload, improved detection evasion techniques, and runs without a front-end UI for improved execution in non-interactive modes. Try it on your next workshop.
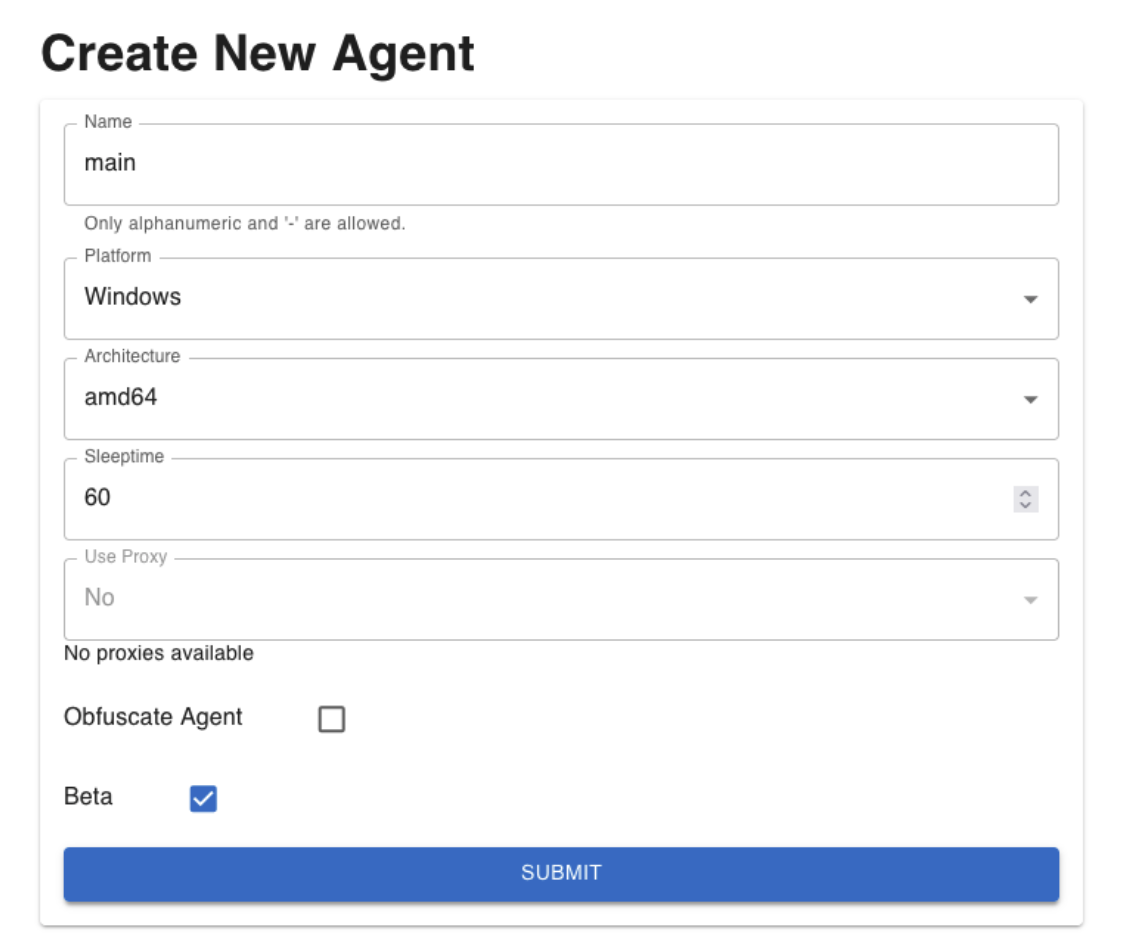
BlindSPOT Agent- Implant
We’ve long had the ability for BlindSPOT simulations to attempt to exfiltrate data and download content from the Internet. But facilitating those actions either meant using public sources (out of our control – never a good idea) or having to stage the necessary services on the Internet to handle file hosting or uploads. We’ve been hard at work designing a way to make this easier.
The result is something we are calling Satellite – a specialized app that you can host on any Windows or Linux server and instantly be prepared to test exfiltrating files or downloading content as part of your simulations.
Best of all, you are in complete control of the execution of the Satellite – it runs on systems under your control and when you want it. It allows us to quickly move to new IP addresses and domains that have never interacted with your organization before, to see how your tools would handle that type of activity. Oh, and it will also act as a C2 relay, so your implants don’t have to phone home directly to the BlindSPOT server. Currently released in limited beta testing, we expect to have this out to all BlindSPOT customers soon.

With extensive experience in cybersecurity, intelligence, and incident response, Carly will play a pivotal role in enhancing OnDefend’s threat intelligence capabilities and program development.
Previous Leadership Roles:
Meet Carly
Thank you for taking the time to read our updates. We are committed as an organization to continue pushing boundaries within the world of innovation. OnDefend & BlindSPOT are the products of that. If you would like to learn more or have any suggested recommendations, please reach out: Contact Us.
Email phishing is now the #1 ransomware attack vector—and if you’re responsible for managing a Secure Email Gateway (SEG), you know the frustration of seeing malicious emails bypass filters despite your best efforts.
You’re not alone.
Many organizations deploy industry-leading SEGs, yet they still struggle with phishing and ransomware delivery attempts slipping through. Why? Because email security isn’t a set-it-and-forget-it solution—it requires constant testing, fine-tuning, and adaptation to evolving threats.
Let’s break down why SEGs miss threats, what you can do to strengthen your defenses, and how continuous ransomware defense validation can prove whether your SEG is actually working as intended.
Today’s phishing emails aren’t the sloppy, typo-ridden scams of the past. Threat actors continuously test their payloads against multiple SEGs to find what gets through. Some of their most effective evasion techniques include:
Many organizations deploy SEGs with default settings, assuming their vendor’s out-of-the-box policies will protect them. But every environment is different, and failure to fine-tune filters leads to missed threats. Common configuration issues include:
A SEG is only as good as its last real-world test. Many organizations assume their SEG is working—until a ransomware attack proves otherwise. The only way to know for sure is through continuous validation that simulates real-world phishing and malware delivery attempts to test whether your SEG is actually blocking what it should.
In a recent webinar, Reimagining Ransomware Defense: Revealing and Removing the Hidden Risks of Security Control Failures, OnDefend CEO Chris Freedman discussed why SEGs commonly fail. Here’s a short clip:
The best way to identify weaknesses is to actively test your SEG with the same techniques attackers use. OnDefend’s Ransomware Defense Validation (RDV) includes comprehensive SEG testing, helping organizations:
Once you identify the gaps, it’s time to optimize your SEG configuration:
If your SEG consistently fails real-world attack simulations, it may be time to evaluate other vendors. Not all SEGs offer equal protection, and some provide better:
Email is still the cybercriminal’s favorite playground, and your Secure Email Gateway (SEG) is supposed to be the bouncer at the door. But let’s be real—how often do you check if that bouncer is actually stopping the bad guys?
Your SEG isn’t magic—it’s only as good as the rules and configuration you set and the tests you run. Don’t assume it’s got you covered just because it’s there. It’s definitely not a set-it-and-forget-it security control. Get hands-on, put it through the wringer, and make sure it’s actually keeping your inbox safe. Because when it comes to email security, guessing isn’t good enough.
Or better yet, let OnDefend do it for you with real-world phishing and malware testing. SEG testing is inexpensive and a super small lift on your end (just set up an inbox for our tester). Once we have access to the email, we send hundreds of malicious payloads your way. We’ll assess for the risks of spoofing, non-repudiation, and as a threat vector, and after a 7-day testing period, we’ll provide a full report. Get in touch with OnDefend today to get started.
—–
Resources: https://blog.knowbe4.com/heads-up-email-phishing-is-now-the-top-ransomware-attack-vector
With extensive experience in cybersecurity, intelligence, and incident response, Carly will play a pivotal role in enhancing OnDefend’s threat intelligence capabilities and program development.
Her journey into cybersecurity is anything but traditional, making her expertise in offensive and defensive cyber operations a game-changer for OnDefend. Get to know Carly in this exclusive one-on-one interview.
My role as Director of Threat Intelligence and Programs involves curating, analyzing, and contextualizing threat intelligence to help organizations proactively defend against cyber threats. This includes developing cybersecurity programs that reinforce OnDefend’s strategic and operational efforts.
Whether it’s advancing threat modeling, enhancing cyber defenses, or managing large-scale security programs, my job is to ensure OnDefend stays ahead of evolving cyber threats and in return helping our customer’s stay ahead.
My path was definitely unconventional. I hold a master’s degree in healthcare administration and initially planned to work in healthcare management. However, my work in technical rescue operations led me to the North Carolina Department of Public Safety, where I became involved in intelligence work.
This exposure to counterterrorism, critical infrastructure protection, and cyber threats propelled me into cybersecurity. Over time, I transitioned from working on public safety and law enforcement investigations to tackling cybercrime, ransomware defense, and nation-state threats.
One of my defining moments was leading multiple incident response efforts for organizations facing advanced cyber threats. Whether dealing with nation-state adversaries or ransomware groups, I was responsible for guiding teams and organizations through high-stakes cyber incidents.
Previous Leadership Roles:
- Interim State Chief Risk Officer & Chief Information Security Officer (CISO) of North Carolina – Oversaw state-wide cybersecurity infrastructure.
- Former Deputy State Chief Risk Officer & Chief Information Security Officer
- Principal Consultant at CrowdStrike – Led digital forensics and incident response (DFIR) efforts against global cyber threats.
OnDefend is uniquely positioned—it’s a growing, yet stable cybersecurity company. That balance provides the perfect opportunity to build and shape cybersecurity programs that will have a long-term impact.
Additionally, I was drawn to OnDefend’s mission. The company goes beyond compliance checkboxes, focusing on real-world testing of security defenses. That aligns with my philosophy: cybersecurity should be proactive, dynamic, and constantly evolving to outpace adversaries.
A recent project that stands out was helping to identify and attribute a new cyber threat actor tied to North Korean cyber operations. As part of a global intelligence effort, within my role at CrowdStrike, I contributed to the discovery and documentation of tactics used by this group, leading to their official designation as Famous Chollima.
Being involved in tracking, analyzing, and exposing a major adversary’s operations was a career-defining moment for me.
- Be open to opportunities – Your career path might not go as planned, and that’s okay. Many of my biggest career moves came from saying yes to unexpected challenges.
- Speak up and ask questions – The best cybersecurity professionals are always learning. Don’t be afraid to say, “I don’t know, but I’ll find out.”
- Never dim your light to make others comfortable – Your skills and insights are valuable. Own them confidently.
I hope to see a shift towards real-world testing of security controls rather than just compliance requirements. Cyber threats evolve too quickly for static defenses. We need to be adaptive, dynamic, and creative to stay ahead.
With advancements in AI-driven threats and automation, defenders must be just as innovative as attackers. I expect a stronger focus on offensive security testing and real-time threat validation over the next five years.
Watch Carly’s full interview here: OnDefend welcomes Carly Sherrod as new Director of Threat Intelligence and Programs
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world cyber threats. From ensuring compliance with industry standards to building out mature security programs, our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, please visit http://www.ondefend.com/
OnDefend Media Contact:
Lauren Verno, Media@ondefend.com
904-299-3669
Let’s face it—ransomware isn’t just a buzzword anymore; it’s a business reality. From high-profile attacks on hospitals to cyber criminals targeting supply chains, no organization is immune.
There were 1,204 confirmed ransomware attacks and 195.4 million compromised records in 2024, according to a recent study by Comparitech. But here’s the good news: you can take proactive steps to improve your defenses and ensure that your organization can withstand even the most determined attacker. Ransomware readiness is about more than just prevention—it’s about preparation, response, and resilience.
So, buckle up! We’re diving into the top five steps you need to take to prepare your organization for the inevitable ransomware threat (and yes, we’ve kept it simple and actionable).
You can’t protect what you don’t know you have. Start by mapping out the crown jewels of your organization—those assets that, if compromised, would cause serious harm.
Action Items:
Pro Tip: Prioritize assets that house sensitive customer data, intellectual property, or operational systems that are essential to business continuity.
Gone are the days when a strong perimeter defense was enough. With hybrid work and cloud environments, your organization needs a security approach that assumes no one and nothing can be trusted.
Core Components of Zero Trust:
You’ve invested in security tools, but are they actually working? Misconfigurations, outdated policies, and evolving threats can all create blind spots in your defenses.
Continuous validation ensures you know where your gaps are—before attackers do.
What You Should Do:
Dive deeper: into the hidden risks of security control failures that teams may be missing, read our blog The Hidden Risks of Security Control Failures.
Pro Tip: Testing and validation isn’t a one-and-done activity. Make it part of your ongoing security program to catch changes before they become vulnerabilities using managed services like OnDefend’s Ransomware Defense Validation (RDV).
Think of backups as your insurance policy. Even with the best security, breaches can happen. The key is ensuring you have clean, up-to-date backups that you can rely on during recovery.
Best Practices for Backups:
Fun Fact: Backups are a favorite target of ransomware attackers. 96% of ransomware attacks targeted backup repositories. Make sure yours are protected and isolated from the production network.
Let’s be honest—when ransomware hits, you don’t want to be scrambling to figure out what to do. A well-documented and tested response plan can mean the difference between a contained incident and a full-blown crisis.
What Your Plan Should Cover:
Pro Tip: OnDefend’s Ransomware Defense Validation (RDV) services will simulate a real-world attack to test your incident detection and response protocols and determine if your response teams are optimally functioning.
Ransomware readiness isn’t a checkbox; it’s an ongoing process. By taking these five steps, you’ll be well on your way to building a resilient organization that can prevent, detect, and respond to ransomware threats with confidence. Don’t wait until you’re in the middle of an attack to realize you weren’t ready. Start today, iterate, and continuously improve.
Oh, and one last thing: Reach out to us here if you need help validating your defenses or simulating real-world ransomware attacks. We’ve got your back (and your backups!).
We know you’ve invested heavily in your security controls like Secure Email Gateways (SEGs), Endpoint Detection and Response (EDR) tools, and Managed Detection and Response (MDR) services. We also know from first-hand experience doing thousands of security tests for our customers that even best-in-class technologies and security provider vendors can and do fail—often silently.
For CISOs, CIOs, and security teams, understanding why security controls fail is critical to ensuring defenses remain effective against countless adversaries.
Let’s explore common failure points, their root causes, and actionable strategies to address these challenges head-on.
Security controls fail for a variety of reasons, including misconfigurations, outdated rules, and human error. Most organizations have three primary control layers—prevention, detection, and response—and here’s where they often break down.
SEGs are often the first line of defense, designed to protect organizations from email-based threats by filtering out phishing emails, malicious attachments, and spoofed communications. However, these systems can fail due to:
A 2024 report by Cofense revealed a staggering 104.5% increase in malicious emails bypassing SEGs. This rise highlights the difficulties SEGs face in keeping up with the rapidly evolving tactics of phishing campaigns, which can lead to potential security breaches when these malicious emails reach end-users. For most enterprises, relying on “good enough” email security is no longer a viable option.
Detection tools like EDR, XDR, SIEM, and NDR solutions are critical for identifying malicious activities. If you’re like most CISOs we’ve talked to, you’re probably dealing with challenges from each one such as:
Tool Misconfigurations: Often the result of improper setup, incomplete tuning, common misconfigurations include:
According to OnDefend’s assessments (2023-2024), 7 out of 10 attack simulations identified security tool misconfigurations or exploitable control failures.
Unintentional Changes: Tools often experience configuration drift, where the settings gradually deviate from the optimal state due to:
In Vectra AI’s 2024 State of Threat Detection and Response research report, they found that “77% of SOC teams say they push aside important security tasks more than twice a week so they can tune, monitor, and maintain existing security tools and some teams even say this is a daily occurrence.”
Threat response failures of security monitoring teams, such as Managed Detection and Response (MDR), Network Detection and Response (NDR), etc. often result from a combination of the following:
In fact, 5 out of 10 of attack simulations conducted by OnDefend resulted in no response or a delayed response outside SLA requirements.
A prominent U.S. healthcare system faced significant challenges with its email gateway, detection tools, and response providers. Despite investing in state-of-the-art SEGs, EDR solutions, and internal teams working with third-party response providers, simulated tests by OnDefend uncovered critical vulnerabilities:
Results: After addressing these issues, the organization improved its email filtering accuracy to 97% and reduced MTTR to under 21 minutes, significantly reducing risk exposure.
Read the full case study here.
Every security control failure is a chance to improve. By continuously testing, validating, and optimizing your defenses, you can transform your organization from reactive to resilient. You’ve already invested in the best and it’s time to find out if your controls are working right now. Don’t wait for the bad guys to find out first.
We also know how very little bandwidth you have, which can make it seem impossible to do all of this with the resources you currently have. We solved this problem for you. With OnDefend’s Ransomware Defense Validation (RDV) services, our expert teams take care of the continuous testing and validation using our proprietary BAS tool, BlindSPOT.
Discover and fix hidden gaps in your defenses. Schedule a call with OnDefend today to learn more.
Want to learn why continuous security control validation is critical? Read this next.
This year was a whirlwind (in a good way). From being named TikTok’s Independent Security Inspector to rolling out some of the most impactful updates for BlindSPOT yet. Along the way, we welcomed new talent, expanded partnerships, and tackled some of the biggest challenges in cybersecurity.
TikTok U.S. Data Security selected OnDefend as its Independent Security Inspector
OnDefend’s rigorous application and network penetration testing standards was one of the reasons OnDefend was selected as the Independent Security Inspector for TikTok USDS this year. Our role continues into 2025, to ensure that TikTok USDS platform’s security strictly complies with national and global cybersecurity standards.
BDO Digital integrates OnDefend’s cutting-edge Breach & Attack Simulation (BAS) into its Active Assure Security Service
“Our collaboration with OnDefend empowers BDO Digital to offer our clients real-time validation that enhances defenses against the dynamic and sophisticated nature of cyber threats,” said Ric Opal, BDO Digital Principal & National Leader of IT Solutions and Strategic Partnerships.
This year, BlindSPOT became even more powerful, helping organizations like yours identify security control “blind spots” faster than ever.
Key Highlights:
Everything on the BlindSPOT roadmap is designed to make it the best option for you to safely and quickly test your defenses, and a lot of the ideas we’ve featured in these updates have come from customer feedback and suggestions, so thank you!
Catch Up on the Latest Updates
OnDefend is recognized as one of the world’s fastest-growing Gator businesses in 2024.
OnDefend named the 37th fastest growing Gator business globally in 2024 by the University of Florida Alumni Association’s prestigious Gator100 program.
This recognition celebrates the achievements of alumni-led businesses worldwide and underscores the significant contributions of Gators in various industries.
Honored as an honoree in GrowFL’s 14th Annual Florida Companies to Watch
OnDefend was selected as an honoree in the 14th Annual GrowFL Florida Companies to Watch Awards. Selected from over 500 nominees, OnDefend joins a select group of second-stage companies celebrated for their contributions to Florida’s economic growth, innovation, and resilience.
Former Department of Defense, Booz Allen & EY exec Wayne Loveless joins OnDefend
Wayne Loveless is a globally recognized cybersecurity engineer, strategist, and leader with more than 25 years of industry experience across the Government and Public Sector, Defense, Energy, Oil and Gas and Healthcare industries.
He has led and supported teams in the development of National Cybersecurity Strategies, development and implementation of large-scale enterprise cybersecurity programs, research and development, and cybersecurity engineering in government and private industry.
Aaron Rosenmund Joins OnDefend as Senior Director of Programs and Tradecraft
With a passion for redefining cybersecurity strategy and prevention, Aaron brings extensive expertise in red teaming, threat emulation, and security testing.
In addition to his role as Senior Director of Programs and Tradecraft, Aaron will serve as associate program director for the Independent Security Inspector program with TikTok USDS. He will lead teams to ensure the effectiveness of security measures for TikTok USDS, while driving innovation and implementing his strategic vision across OnDefend’s services and product offerings.
This year has been a whirlwind for cyber-attacks which made narrowing down this list particularly difficult. Taking into consideration level of critically, financial disruption, and overall impact, we present the biggest attacks of the year:
1. Change Healthcare Ransomware Attack
2. China’s Espionage Campaign Targeting U.S. Telecommunications
3. AT&T’s Data Breach Affects Nearly All Customers
4. Ticketmaster and Snowflake Attack
5. Synnovis Ransomware Attack on London Hospitals
BONUS: Go behind the scenes with a healthcare CISO to unpack the BlackCat ransomware attack on Change Healthcare. Watch Here.
Built by security leaders for security leaders to combat the growing ransomware pandemic. The RDV service simulates real-world attacks using OnDefend’s proprietary solution, BlindSPOT to consitently prove your defenses in depth are protecting your organizations:
Join us in the new year as we reimagine ransomware defense, showcasing RDV in action within a prominent healthcare system. See real results and the difference proactive security testing can make in real time.
Want a sneak peek? Learn more here.
Thank you for taking the time to read our updates. We are committed as an organization to continue pushing boundaries within the world of innovation. OnDefend & BlindSPOT are the products of that. If you would like to learn more or have any suggested recommendations, please reach out: Contact Us.
About OnDefend:
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world cyber threats. From ensuring compliance with industry standards to building out mature security programs our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, contact us.
This year has been a whirlwind for cybersecurity, with some of the most devastating and eye-opening cyberattacks making headlines. From ransomware shutting down healthcare systems to espionage campaigns targeting critical infrastructure, these incidents have sent shockwaves through industries worldwide.
Why do these attacks matter to your organization and everyday life? Understanding what happened, why it matters, and the lessons we can take away is key in a world where cyber threats are only getting more sophisticated.
We need to learn from our mistakes, it’s that simple.
What Happened
The Alphv/BlackCat ransomware attack on Change Healthcare and its parent company UnitedHealth sent shockwaves through the healthcare industry, impacting over 100 million individuals. According to reports, the attackers exploited vulnerabilities in the company’s infrastructure to encrypt data and exfiltrate private health information, including diagnoses, treatment records, and financial details. The breach disrupted critical healthcare operations across the United States, forcing some facilities to delay treatments and even cancel appointments. Investigations revealed that the attackers used advanced tactics to maintain persistence in the network, escalating the damage over time before their demands surfaced.
Why It Matters
This attack isn’t just about numbers—it’s about lives. The stolen data is not only highly sensitive but also incredibly valuable on the black market, where medical records can fetch significantly higher prices than credit card information. The attackers not only encrypted critical files but also demanded a hefty ransom of $22 million. With Change Healthcare serving as a linchpin in healthcare operations for hospitals, clinics, and insurers nationwide, the attack demonstrated just how crippling a breach at such scale can be. It also exposed the healthcare sector’s ongoing struggles with outdated cybersecurity measures, making it a prime target for sophisticated ransomware groups.
The Takeaway
The Change Healthcare ransomware attack is a stark reminder of the stakes involved when cybercriminals target the healthcare sector. Beyond the immediate operational and financial fallout, the long-term consequences for affected individuals—identity theft, fraud, or even compromised patient care—are immense.
Watch an Exclusive Interview: Learn from James Case, CISO of a major healthcare system, as he discusses the impact of this attack. Watch Here.
What Happened
China’s Salt Typhoon group has ramped up its cyber espionage operations, targeting U.S. telecommunications networks to steal sensitive communications data. These attacks have been ongoing for months, starting well before the U.S. election, and have involved highly sophisticated techniques, including the exploitation of vulnerabilities in key systems such as Cisco routers and Microsoft Exchange servers. The breach affected major telecoms like T-Mobile, Verizon, and AT&T. While T-Mobile assured that no sensitive customer data was compromised, the campaign’s larger focus was clearly on high-value government and political targets, showcasing its national security implications
Why It Matters
Senator Mark Warner, speaking to The Washington Post, emphasized the severity of the attacks, stating, “My hair is on fire” because of the sustained nature of these intrusions. These attacks are far more advanced than previous incidents like the SolarWinds supply chain attack or the Colonial Pipeline ransomware attack. The Salt Typhoon campaign has given Chinese operatives a persistent foothold in U.S. telecom networks, potentially requiring the replacement of “thousands and thousands” of switches and routers. This shows just how vulnerable our most critical infrastructure has become. With these networks integral to national defense and public communications, an attack of this scale not only affects business but could disrupt entire government operations and defense strategies.
The Takeaway
Senator Warner’s comparison of China’s cyber actions to Russia’s cyber incidents, calling them “child’s play,” highlights the growing complexity and scale of cyber warfare from nation-states. This attack is a wake-up call for the private sector and government alike to seriously address vulnerabilities in telecommunications infrastructure.
Discover OnDefend services: Learn how OnDefend simulates real-world threat actors on an organizations environment in real-time using in-house breach & attack simulation capabilities with BlindSPOT.
What Happened
Hackers breached AT&T’s systems, stealing 50 billion call and text records. The stolen data included call logs, text message metadata, and who communicated with whom—but not the content of messages. AT&T publicly confirmed the breach in July, acknowledging that “nearly all” its cellular and landline customers were affected, with approximately 110 million individuals being notified.
Why It Matters
The breach highlights the risks of third-party data storage and the value of metadata, even without message content. It also underscores the importance of third-party risk management.
The Takeaway
Ensure continuous monitoring and simulation of potential third-party risks. Comprehensive tabletop exercises can uncover vulnerabilities in your supply chain.
Take the Next Step: How OnDefend can help your company prepare for these challenges by running comprehensive tabletop exercises designed to uncover vulnerabilities in your supply chain. Learn More.
What Happened
While the Ticketmaster and AT&T attack may be tied, they we’re both impactful enough to generate their own headlines.In May, cybercriminal group ShinyHunters stole the personal data of 560 million Ticketmaster customers worldwide by exploiting stolen login credentials for Snowflake, the company Ticketmaster uses for cloud storage. The breach included names, contact details, and encrypted credit card information. The hackers reportedly attempted to sell the stolen data for $500,000 on a dark web forum. Ticketmaster delayed notifying customers, citing ongoing police investigations, and recently began sending warning emails to customers in North America.
Why It Matters
The scale of the attack—impacting over half a billion users—raises serious concerns about the security of sensitive customer data stored on cloud platforms. The delay in notifying customers further compounds the issue, as it leaves individuals exposed to potential identity theft and fraud for an extended period.
The Takeaway
Same as above. Love the cloud? Then love regular audits and rock-solid configuration controls even more.
What Happened
The Synnovis ransomware group targeted London’s healthcare infrastructure, leading to widespread disruption. Synnovis, which provides laboratory and diagnostic services to hospitals, became a prime target for the Qilin ransomware gang, who successfully encrypted critical data using a combination of phishing and exploitation of vulnerabilities. This attack left hospitals struggling to process medical results, impacting patient care and hospital operations. The breach also forced the affected hospitals to switch to manual processes, delaying diagnostic services and causing significant operational chaos.
Why It Matters
Ransomware gangs are increasingly targeting the backbone of healthcare—laboratory services and diagnostic systems. These operations are integral to patient care, and a disruption of such services can have a ripple effect throughout the healthcare ecosystem, potentially putting lives at risk.
The Takeaway
Implement stringent vendor management, comprehensive cybersecurity protocols, and continuity plans to mitigate such attacks.
Discover How: Prepare and defend your organization from ransomware with OnDefend’s Ransomware Defense Validation. Learn More.
These attacks are more than headlines—they’re impacting our everyday lives. No industry is safe, and the general public is becoming more aware of the impact these cyberattacks can cause on our critical healthcare services to the daily use of our cell phones. While we can prevent all risk associated with an attack, we can reduce it. Let’s learn from our past.
Contact Us Today: Learn how OnDefend helps companies prepare for and defend against real-world threats. Get Started.
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world cyber threats. From ensuring compliance with industry standards to building out mature security programs, our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, please visit http://www.ondefend.com/
OnDefend Media Contact:
Lauren Verno, Media@ondefend.com
904-299-3669
Sources:
Qilin ransomware gang linked to attack on London hospitals, Bleeping Computer
Snowflake hackers identified and charged with stealing 50 billion AT&T records
Ticketmaster warns customers to take action after hack, BBC News
China has utterly pwned ‘thousands and thousands’ of devices at US telcos, The Register
JACKSONVILLE, Fla. (October 29,2024) – OnDefend, a leader in preventative cybersecurity solutions, has been selected as an honoree in the 14th Annual GrowFL Florida Companies to Watch Awards. Selected from over 500 nominees, OnDefend joins a select group of second-stage companies celebrated for their contributions to Florida’s economic growth, innovation, and resilience.
The GrowFL Florida Companies to Watch awards, presented by Nperspective CFO & Strategic Services in partnership with the Edward Lowe Foundation, highlights businesses that showcase impressive growth potential, strong leadership, and community impact.
Recognizing OnDefend’s Commitment to Cybersecurity Innovation and Community Impact
Companies were evaluated on a comprehensive set of criteria including:
“Being recognized by GrowFL as a Company to Watch is a testament to our team’s dedication to advancing cybersecurity, supporting economic growth, and making a positive impact on our state” said Chris Freedman, CEO of OnDefend. “At OnDefend, we are committed to developing innovative solutions that empower businesses to defend against real-world cyber threats. We’re proud to be part of Florida’s thriving ecosystem and look forward to continuing our mission to ensure that the security resources organizations invest in are well-utilized, effective and provide tangible results.”
“GrowFL Florida Companies to Watch is dedicated to recognizing the invaluable contributions of second-stage businesses,” said Pete Previte, Chair of GrowFL Board of Directors and Broker Associate, CRES CORP. “These companies are the driving force behind Florida’s economic vitality, fostering job creation, innovation and sustainable growth.”
About the GrowFL Florida Companies to Watch Awards Program
For eligibility, companies must be headquartered in Florida with 6-150 employees and revenue between $750,000 and $100 million. Over the past four years (2020-2023), these honorees collectively generated close to $2 billion in revenue and created 1,462 jobs, reflecting a remarkable 180% revenue increase and 127% job growth. This translates to an average annual revenue growth of 45% and 32% employee growth.
Continued Growth Projected for Honorees
These companies projected consistent growth, with a projected 31% revenue increase and 19% employee growth in 2024. If their projections hold true, these companies will have generated more than $2.9 billion in revenue and added 1,951 employees over the last five years — a staggering 266% increase in revenue and 169% increase in jobs since 2020.
The official recognition of the 50 Honorees will take place on February 27, 2025, at the Hard Rock Live in Universal CityWalk, Orlando, FL.
About GrowFL: GrowFL is Florida’s premier organization dedicated to accelerating the success of second-stage companies. We equip these high-growth businesses (with at least 6 employees and $750,000 in revenue) with the tools and connections they need to overcome unique challenges and achieve their full potential. Through our diverse programs and proven methods, GrowFL empowers Florida’s second-stage companies to drive economic prosperity throughout the state.
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world cyber threats. From ensuring compliance with industry standards to building out mature security programs, our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, please visit www.OnDefend.com.
Contact
These tales are a reminder of the lurking dangers from sometimes the most obvious sources. From phishing attacks to data center nightmares, here are five real-life cybersecurity stories that will give you goosebumps!
Wayne Loveless, OnDefend Managing Director of Strategic Services
Several years ago, I led a large team tasked with designing and implementing security controls for a massive, newly built hospital. The facility had already opened, even though it was still being built from an IT perspective. My primary concern was the lack of physical security controls. For instance, the hospital’s main data center, which served not only the local hospital but the entire Washington D.C. region, had doors propped open, and access was practically free for all.
After repeatedly raising the issue to senior leadership without action, I decided to take matters into my own hands—with the CIO’s permission, of course. I left my badges in the car, put on some scrubs, and walked right into the data center, past several checkpoints without being stopped. I then wheeled out a rack containing patient data right out of the front doors of the hospital, assisted by staff along the way.
I sent a selfie to the regional CIO, showing myself with the stolen equipment. It worked like a charm—security was quickly and dramatically improved. Sometimes, it takes a little trickery to deliver the treat of better protection!
Aaron Rosenmund, OnDefend Senior Director of Programs and Tradecraft
The phone rang for the third time in 10 minutes. Our IT support team, utterly exhausted after weeks of around-the-clock shifts, answered yet another call from a team member unable to access mission-critical resources. Machines were mysteriously dropping off the network, and the ports were locking. Logs indicated MAC address mismatches, making it seem like someone was spoofing devices.
The team suspected everything from insider threats to advanced malware, but there was little evidence to go on. It wasn’t until we isolated and baselined one of the systems in the lab that the truth emerged—a rare, misconfigured network switch was causing all the chaos. No hacker, no malware—just a simple configuration error wreaking havoc on an entire mission-critical system.
Sometimes, the biggest horror stories are not from advanced cyberattacks but from the small mistakes that get overlooked during high-pressure situations.
Joe Brinkley, OnDefend’Director of Offensive Security
During a penetration test for a hospital, we stumbled upon an old MRI machine running Windows Server 2003—ancient by today’s standards. Exploiting known vulnerabilities in the system, we gained access. But what we uncovered next was truly terrifying.
From this single machine, we cracked passwords, infiltrated the hospital’s local domain, and compromised more accounts. Then, we gained access to a connected vendor’s domain and VPN, escalating our privileges. In the end, we had the ability to steal sensitive patient data from multiple organizations undetected.
The experience was a chilling reminder that even seemingly innocuous devices can become powerful tools for cybercriminals if left unprotected.
Billy Steeghs, OnDefend COO
Phishing attacks are one of the most effective tactics used by cybercriminals. We were conducting a phishing and social engineering test for a client. After presenting the results, we realized that the person who had initiated the test and signed the contract had fallen for the phishing attempt. Despite being fully aware of the exercise, they unknowingly provided their credentials.
It was a humbling reminder that no one is immune. Even those who organize the tests can be caught off guard. It just goes to show how convincing and dangerous phishing attacks can be—especially when they target human behavior.
Evan Hosinski, OnDefend’s Senior Tradecraft Engineer
One of the most frightening experiences I’ve had was during a web application pentest for a medical company. They relied on a third-party vendor to generate all their PDFs linked to medical records. After some probing, I found the vendor’s site and a version number that led me to a series of vulnerabilities (CVEs). Using this information, I developed a tool that could brute force random patient IDs, giving access to medical records.
When I presented my findings, the client dismissed it as an unlikely scenario, saying it would require insider access. Fast forward a few months, and the same company made the news—hundreds of medical forms were leaked due to the exact type of brute force attack I had warned them about. This was not a database leak but a targeted attack, and they paid the price for not taking the threat seriously.
From phishing attacks and unsecured data centers to unpatched machines and network misconfigurations. These real-life stories remind us that even the most well-prepared organizations can fall victim to cyber threats. The lesson here? Always stay vigilant and never underestimate the power of even the smallest vulnerabilities—they might just turn into your next horror story.
About OnDefend
OnDefend, established in 2016, stands at the forefront of preventative cybersecurity testing and advisory services, a reputation further enhanced by the introduction of its advanced Breach and Attack Simulation (BAS) Software as a Service (SaaS) platform, BlindSPOT. OnDefend is a trusted partner, empowering organizations globally to proactively combat real-world cyber threats. From ensuring compliance with industry standards to building out mature security programs, our mission is to ensure that the security resources our customers invest in are well-utilized, effective, and provide tangible results. For more information about their services and solutions, please visit http://www.ondefend.com/
OnDefend Media Contact:
Lauren Verno, Media@ondefend.com
904-299-3669