Cybercriminals are always on the lookout for vulnerabilities to exploit, and no industry is safe from their attacks.
This is why it’s crucial for organizations to stay one step ahead by proactively identifying and addressing potential security risks before they can be exploited by malicious actors. One effective way to do this? Threat-informed pentesting – a comprehensive security testing approach that focuses on identifying and mitigating real-world threats that specifically target your industry.
It’s a proactive approach to cybersecurity that helps you sleep better at night knowing you’re taking the necessary steps to protect your organization from cyber attacks.
 This isn’t going to be a traditional year, don’t limit yourself to a traditional pentest. Contact OnDefend today to learn more about how threat-informed pentesting can help protect your organization.
This isn’t going to be a traditional year, don’t limit yourself to a traditional pentest. Contact OnDefend today to learn more about how threat-informed pentesting can help protect your organization.
Our experienced team of cybersecurity experts can provide you with a customized approach to threat-informed pentesting that fits your specific industry and organization.
OnDefend Company Newsletter: Creating a Culture of Understanding and Solutions
Have you ever heard the phrase, the days are long but the months are short? That is the only way I know how to describe the first few months of 2023. Between launching a new set of featured services, rolling out more BlindSPOT updates, and keeping up with the news, it has been a rollercoaster for our company. Which is why we are launching this newsletter, to keep everyone up to date with what’s going on with OnDefend and the latest cybersecurity trends. So, before I bore you to death with anymore long winded metaphors, let’s go ahead and get started.
Better Together

OnDefend is proud to call ourselves a partner first company. While we can’t name every company who private-labels our services we are excited to announce some recent partnerships, including PlexTrac. Check out our most recent webinar with PlexTrac CEO Dan Decloss & OnDefend CTO Ben Finke.
Learn More: OnDefend Integrates with PlexTrac to Deliver Threat-Informed Pentest
Threat- Informed Pentest
Are you limiting yourself to a traditional pentest? Traditional pentests are great but they don’t always answer leaderships question “are we prepared for this specific threat actor that we read about in the news? TIP solves that problem.
Learn More: Threat-Informed Pentesting: What Is It?
OnDefend In The News

It is always an honor to be recognized for achievements within your community. From being recognized for growth in the tech sector to Inno On Fire, there has been plenty of reasons to celebrate our companies success. Personally, I love the fact that one publication used our CEO’s picture and made him look like a character out of the hunger games.
Learn More:
Flurry of activity in 2022 has Jax’s tech sector prepared for coming year
2022 Class of Fast 50: OnDefend
Bylines By Ben

We are proud to announce our CTO Ben Finke was accepted into the Forbes Technology Council. What does this mean? Forbes accepts members based on their background, experience, and achievements within tech. Ben was accepted into this elite group of leaders and innovators to share advice and write meaningful content which is shared across Forbes’s platform. Check out his first article, breaking down the basics of a supply chain attack.
Learn More:
You Don’t Need To Be In IT TO Understand A Supply Chain Hack (Forbes)
15 Expert-Recommended Ways For Consumers To Better Protect Their Privacy Online (Forbes)
13 Tech Industry Leaders Discuss Their Top Internal Initiatives For 2023 (Forbes)
16 Tech Leaders’ Tips For Managing The Day-To-Day Work Grind (Forbes)
CMMC Deadline
DoD contractors are required to become CMMC complaint by the end of May, but this process won’t happen over night. Our experts say your company needs 60-90 days to complete all requirements. Aka let us help you now!
Learn More: CMMC 2.0 Basics: The 101 of Getting Compliant
BlindSPOT Updates
We are constantly working on new BlindSPOT features to make the platform as user friendly as possible. We believe in making these changes as easy and understandable as possible, so with that being said here are the latest BlindSPOT updates for 2023, so far…
BlindSPOT Updates: January Edition
Anybody else feel like we just scratched the surface? That’s because we did. Stay tuned for this bi-monthly newsletter, for all of OnDefends latest and greatest. In the meantime if you have any questions feel free to reach out at contact@ondefend.com.
JACKSONVILLE, FLORIDA and BOISE, IDAHO — February 15, 2023 — OnDefend, a critical partner of security service firms and corporations throughout the US and around the world, using the power of PlexTrac, the premier cybersecurity reporting and collaboration platform, presents a groundbreaking security offering to customers and partners through threat-informed penetration testing (TIP).
TIP is the next generation in penetration testing that leverages global threat intelligence about specific emerging adversaries targeting your industry to provide valuable insight on how your environment will respond. TIP safely tests the exact tactics and techniques of the threats your leadership and organization are concerned about.
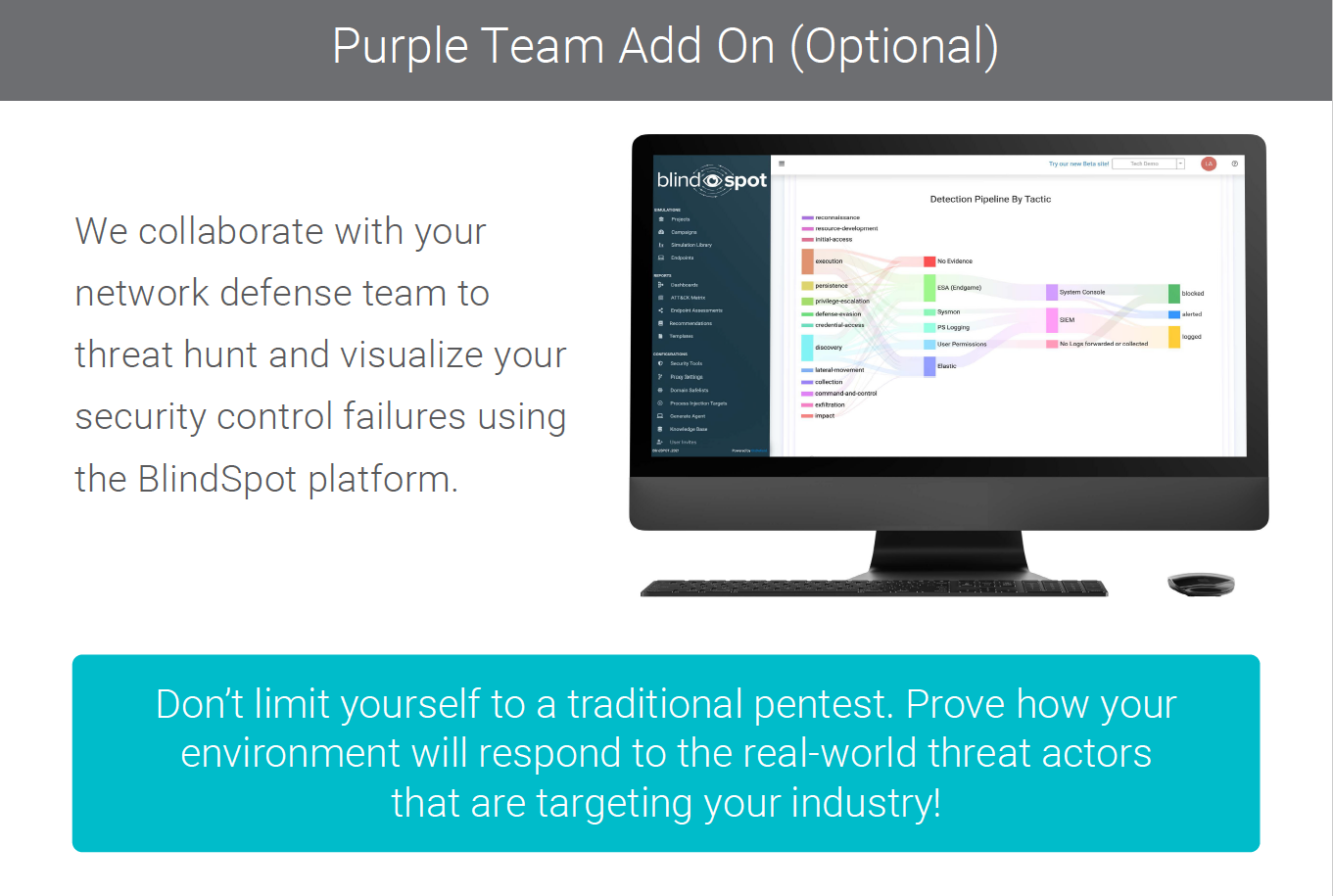
Through an in-depth API integration, OnDefend can now offer customers their automated breach and attack simulation (BAS) solution, BlindSPOT, with seamless remediation management and retesting through PlexTrac Runbooks. OnDefend’s BlindSPOT enables you to execute attack activity on your client’s production network environments for more consistent and real-world practice against adversaries. PlexTrac’s Runbooks supports the planning, execution, reporting, and remediation tracking of your red teaming, purple teaming, or adversary emulation activities.
Using OnDefend and PlexTrac together make TIP actionable for your team by
- Leveraging OnDefend’s seasoned red team to emulate the specific threats actors of your company’s choosing
- Automatically delivering results via API to PlexTrac for comprehensive reporting and remediation management
- Performing remediation retesting via PlexTrac Runbooks, selecting BlindSPOT, OnDefend’s Breach and Attack Simulation solution, to guide the testing
“The partnership between OnDefend and PlexTrac provides companies invaluable insight into whether their security network will withstand an attack from an emerging adversary using threat-informed penetration testing. In addition, organizations need to know their controls will work throughout the year, which is where PlexTrac and OnDefend’s proprietary tools — BlindSpot and Runbooks respectively — will help leadership of those companies sleep well at night knowing their security tools work,” said OnDefend CEO Chris Freedman.
“We are excited to promote this deep integration and partner with OnDefend to help them make threat-informed penetration testing accessible and valuable for any security team,” said PlexTrac Founder and CEO Dan DeCloss. “Using threat intelligence to guide your offensive testing is a great way to become more proactive and move toward a continuous assessment strategy.”
Watch an on-demand webinar from OnDefend and PlexTrac to learn more about the value of threat-informed pentesting and see the BlindSPOT/Runbooks integration in action.
Watch Threat-Informed Pentesting: The First Step to Continuous Assessment:
About OnDefend
OnDefend empowers the information security industry through its cutting-edge technological innovations and battle tested professional services team. By solving the problems that the cyber security industry has not solved, OnDefend has become a critical partner of security service firms and corporations throughout the US and around the world. Whether it’s their next generation SaaS offerings of BlindSPOT and Confirm4Me or their seasoned security team leveraged by partners to meet market service demand, OnDefend has enabled cyber security firms to extend their capacities and corporations to secure their future. To learn more, visit ondefend.com.
About PlexTrac
PlexTrac, Inc. is the premier penetration test reporting and proactive cybersecurity management platform driven by a mission to help teams win the right cybersecurity battles. PlexTrac makes security data aggregation, red and blue team reporting, purple team collaboration, and remediation tracking more effective and efficient so security teams can become more proactive and demonstrably improve security posture. To learn more, visit plextrac.com.
Originally written for Forbes.
Once you understand a supply chain attack, it’s hard not to question whether you might have already been a part of one. We are all familiar with direct cyberattacks, which is why your company’s IT department consistently warns of phishing emails. The attackers need to find a way inside. But what if they were able to find a way in where their malware got brought in by the target themselves? Welcome to the world of supply chain attacks.
Supply chains are a fact of life for every aspect of any IT system and enterprise. Most of the software that we run was made by another company. The hardware it runs on is manufactured by hundreds of different vendors and, in many cases, is hosted and managed by a third party. Even the software we build internally relies heavily on libraries and other software components that are simply imported from other sources. An attacker who can modify anything in the upstream supply chains in any of these scenarios would find themselves already inside hundreds or thousands of environments without having to exert any effort. Scary right?
I’ll give you an example. In 2020, attackers targeted many businesses and organizations, including one notable attack involving SolarWinds. You can read more about this attack via extensive reporting from several media outlets, including Forbes and The Washington Post. A company called Kaseya, which makes another remote monitoring and management (RMM) tool, had something similar occur.
If you’re not in cybersecurity or IT, don’t worry if you don’t completely understand the significance of what could happen in a supply chain attack. Hackers can break into the internal systems used by an organization and add their own malicious code to the real software. When a vendor like this then updates the software used by their customers, they unknowingly send out the malicious code with it.
In some cases of supply chain attacks, thousands, if not tens of thousands, of companies are affected. That’s thousands of separate companies that these attackers are able to sneak their malware into by simply attacking a single organization. Once those companies install an update (which is what security wonks like me are constantly telling folks to do!), the attackers can gain access to those companies’ information technology systems and are able to install even more malware. Think of it as a trickle-down effect. The really scary part is that hacks like these are often undetected for months, gaining access to both government and private entities.
These hacks can be stealthy, where they avoid detection for months, or the attacker can choose to take more noticeable actions with it, perhaps by delivering ransomware. In the case of ransomware, the impact is obvious, but the source is elusive, as these tools are often seen as the defense, not the attack vector.
The impacts of a supply chain attack vary from data breaches to malware installation and financial loss. Detecting this malicious code can be incredibly difficult. And removing the malicious code can be even more challenging, if not impossible.
Attribution is incredibly difficult in these cases, but given the rewards available to a successful operation, it is believed that nation-states and organized cybercrime groups are actively pursuing supply chain attacks to further their own interests.
If only we could go back to only worrying about those phishing emails.
So, what can you do to reduce your own exposure to a supply chain attack? Supply chain attacks may be the most challenging cybersecurity risks we are going to face. But here’s a start.
- Baseline what normal behavior is. “Should our server monitoring software be making connections to the internet?”
- Avoid the temptation to omit any activity executed by “trusted” applications from your threat detection process. That software should behave reliably. You must understand normal to understand abnormal.
- Use software that receives third-party security verification and ensure the vendor can provide up-to-date information like a software bill of materials
- Build an incident response playbook for what to do if one of your trusted utilities is suddenly unavailable to you, especially during a security incident investigation.
- Supply chain attacks are the initial access for these attackers. Plan on catching them when they start moving to the next phase of their operation.
We’ve just scratched the surface of what you can do about supply chain attacks. Stay tuned for the next chapter in our supply chain series, including a deeper dive into what companies can do to block these hackers and an answer to the question, “Will cybersecurity ever be solved?”
Read the original article here: You Don’t Need To Be In IT To Understand A Supply Chain Hack (forbes.com)
OnDefend Media Contact: Lauren Verno, Lauren.verno@ondefend.com
Cybersecurity Maturity Model Certification is a U.S. Department of Defense (DoD) program that applies to Defense Industrial Base (DIB) contractors. It is collective standard and new certification model to ensure DoD contractors protect sensitive unclassified information.
In layman’s terms the government is setting ground rules when it comes to the cybersecurity of organizations they work with.
Why do companies need to take meeting CMMC guidelines seriously? To start, its government mandated and it’s not going away. If anything, CMMC may apply to all non-DoD government contractors in the future. CMMC is not just is not just a bunch of paperwork, such as policies and procedures, the purpose of meeting these standards is to make sure your organizations security tools are working. Finally, CMMC is not something to ignore; it will affect your future in winning bids.
The Basics:
The Department of Defense (DoD) released the CMMC framework to reduce the risk posed by cyber criminals. This framework is set to assess and improve the cybersecurity posture of an astounding 300,000 companies that contribute to DoD systems, networks, installations, capabilities and services.
It is also intended to increase the security of DoD’s supply chain by promoting compliance from all companies that are part of it.
Yet, a recent survey revealed 87% of DoD contractors don’t meet the basic cybersecurity requirements. (Tech.co)
According to the Department of Defense, The CMMC 2.0 program has three key features:
- Tiered Model: CMMC requires that companies entrusted with national security information implement cybersecurity standards at progressively advanced levels, depending on the type and sensitivity of the information. The program also sets forward the process for requiring protection of information that is flowed down to subcontractors
- Assessment Requirement: CMMC assessments allow the Department to verify the implementation of clear cybersecurity standards.
- Implementation through Contracts: Once CMMC is fully implemented, certain DoD contractors that handle sensitive unclassified DoD information will be required to achieve a particular CMMC level as a condition of contract award.
National Industry of Standards and Technology NIST
It provides a comprehensive mapping system that connects specific controls and processes associated with various cybersecurity standards to three distinct maturity models, ranging from basic (Level 1) cyber hygiene to advanced (Level 3).
Some examples of these controls are:
- Do you limit access to authorized users only?
- Do you perform Security Awareness Training for all your users?
- Do you retain and monitor system logs?
- Do you have and exercise an Incident Response plan?
- Do you perform recurring Security Assessments
- Do you limit physical access and monitor the facilities?
- And more…
Drafting policies and procedures, creating system documentation, and implementing technical solutions to close the gaps is a time-consuming and costly process. Cybersecurity consulting firms can help you understand exactly what to implement without going overboard and tailor the implementation to your requirements, needs, and budget.
All DoD contractors and Subcontractors are required to achieve within their level of CMMC 2.0 by end of May with CMMC guidelines and requirements on DoD bids this July.
Find out how OnDefend can assist your company to meet CMMC compliance. Get started today contact@ondefend.com
Want to learn more? https://ondefend.com/blindspot/
Originally written for Jacksonville Business Journal by James Cannon
JACKSONVILLE, Fla. –The First Coast is chock full of companies and nonprofits developing new products, growing their teams and supporting their communities.
To provide a window into that growth, we’ve singled out six outstanding innovators to honor with the 2023 Fire Awards, presented by First Coast Inno and the Jacksonville Business Journal. The honorees include startups and more established firms, and vary in industry and geography across the First Coast.
Company Name: OnDefend
Industry: Cyber Security
CEO: Chris Freedman
Year Founded: 2016
Brief description of what the company does: Private label security-as-a-service and cyber security, threat, detection and assessment firm.
2022 Funding: N/A
As you reflect on 2022’s successes and growth, what was the prime contributing factor?
A strong 2022 strategic plan resulted in another fantastic year of growth despite a waning economy and recession fears toward the end of the year. Because we have a multitude of revenue streams ranging from our cutting-edge products to our wide array of security services, we were not wholly dependent on one offering. Additionally, the fact that we service partners and direct customers further diversified our market share dependence. Regarding our comprehensive security service offerings, our primary customers are other national and international cyber security firms who subcontract us, under their brand, to service their customers. Security talent had become extremely hard to find, employ and retain for years now, which increased wage demands and decreased our partner’s service profit margins. These companies private label us to remove their profit margin fluctuation and to meet market demand without delay. With 2022’s economic uncertainty, our strategic partners began to remove their fixed-expense employee costs and outsource even more services. This also motivated new strategic partners to seek us out and capitalize on the strategic advantage we can afford them.
Now that VC funding and investments have begun to slow, what is your strategy for seeking outside capital?
We have had the rare strategic advantage of not requiring outside capital to find service & product market fit as well as to grow to meet their corresponding demands. This has specifically allowed us to make fast and nimble product moves to find product/market fit with our proprietary SaaS solutions, including our BlindSPOT Breach & Attack Simulation Solution. Now that we are achieving product market fit with our SaaS solutions, we may seek outside debt or equity partners to scale and meet partner and customer demand throughout the US and around the World.
Taking a step back to the company’s founding, are you where you expected to be by now? If more or less, how so?
When we first started we expected to be serving companies in Jacksonville and possibly the Southeast. We never imagined that we would be securing private and public organizations throughout the world. We started out as a pure-play consulting firm with the hope of launching a software division and creating completely unique solutions, but there are very few service providers
that have successfully spun up software divisions, much less found product/market fit for their software solutions. We seem to have successfully navigated those murky waters thus far.
Where does the company go from here? What is next for your company in the short to near-term?
We believe that our company will begin to scale more rapidly and have a larger brand presence in our industry. Our BlindSPOT solution is enabling our direct customers and partners, as well also our internal services team to provide offerings that competitors in our industry cannot. With this distinctive advantage comes the opportunity for scale and we only see more of that in our short- and long-term future.
What is your outlook for your industry and the role you play in it going into the new year?
As cyber grows, so does our industry, and cybercrime is growing at an unprecedented rate. The global cyber security market was valued at $202.72 billion in 2022 and is projected to expand at a compound annual growth rate of 12.3% from 2023 to 2030. Our services and products division can address much of that total addressable market and that is our north star. We also have some paradigm shifting patents that we have yet to develop into commercial SaaS solutions. These patents are focused on identifying account comprises and employee impersonation attacks not only for the email domain, but across many domains including social, media and even new technologies like the metaverse. We plan for our groundbreaking technologies to solve the problems that have not been solved and level the playing field for organizations and individuals against the emerging threats that target them.
Read the original article here: https://www.bizjournals.com/jacksonville/inno/stories/awards/2023/01/19/2023inno-on-fire-ondefend.html
OnDefend Media Contact: Lauren Verno, Lauren.verno@ondefend.com
To what extent can cyberattacks wreak havoc and terrorize modern society?
Until now, this question has revolved around the potential of cyber operations to cause physical destruction or other material harm. In this paper, we propose a broader interpretation. We submit that assessing cyber-threats through the prism of physical destruction has obscured the human dimension of the threat. Instead, we propose calculating the gravity of cyberattacks by measuring psychological distress. This approach recognizes that even seemingly inconsequential cyberattacks can levy tremendous damage by traumatizing civilians, undermining societal cohesion, and exacerbating cycles of violence.
To test whether cyberattacks cause significant individual harm, we employ an internal meta-analysis looking at eighteen studies conducted in three countries over 6 years. Across these studies, we exposed 6,020 respondents to simulated cyberattacks and conventional attacks. We conclude that cyberattacks can cause high levels of psychological harm—equal even to that caused by conventional political violence and terrorism.
This finding overturns a widely accepted view that cyberattacks are a mere irritant at best and a threat to information security at worst. Through this lens, the findings suggest that even nonphysically destructive cyberattacks can trigger consequences that constitute a legally defined armed attack that permits using armed force in self-defense. We conclude by discussing how the onset of psychological distress generates political pressure in support of retaliation and can lead to military escalation.
Read the full report and findings: https://academic.oup.com/jogss/article/8/1/ogac042/6988925
SOURCE: Ryan Shandler, Michael L Gross, Daphna Canetti, Cyberattacks, Psychological Distress, and Military Escalation: An Internal Meta-Analysis, Journal of Global Security Studies, Volume 8, Issue 1, March 2023, ogac042, https://doi.org/10.1093/jogss/ogac042
OnDefend CTO Ben Finke explains this new security offering specifically targeting emerging threat actors.
A new year with the same set of problems. Instead of finding ourselves on the threshold of solving our cybersecurity woes, companies will be forced to do more with the same budget. We have already seen many organizations facing pressure to reduce their spending, including security budgets. But generating better results with less investment is going to require some new approaches to how we think about testing in our environment’s.
Start by asking these questions:
- How can we guarantee the security tools we’ve already invested in will work? How do we identify the gaps that need our attention?
- Companies already conduct annual penetration tests, and that’s not going away, but is that the best way for us to ensure we are prepared for threats?
- What about new emerging threats specifically targeting your industry, how do you test for those?
- How can I better alleviate my leadership and BOD concerns when they ask question of “are we prepared for threat actors we read about on news?”
Threat- Informed Pentesting can fill in the gap.
Forbes Technology Council Advisor Ben Finke has dealt extensively with Penetration testing and detecting emerging threats. In the following interview, he answers the most asked questions about Threat- Informed Pentesting.
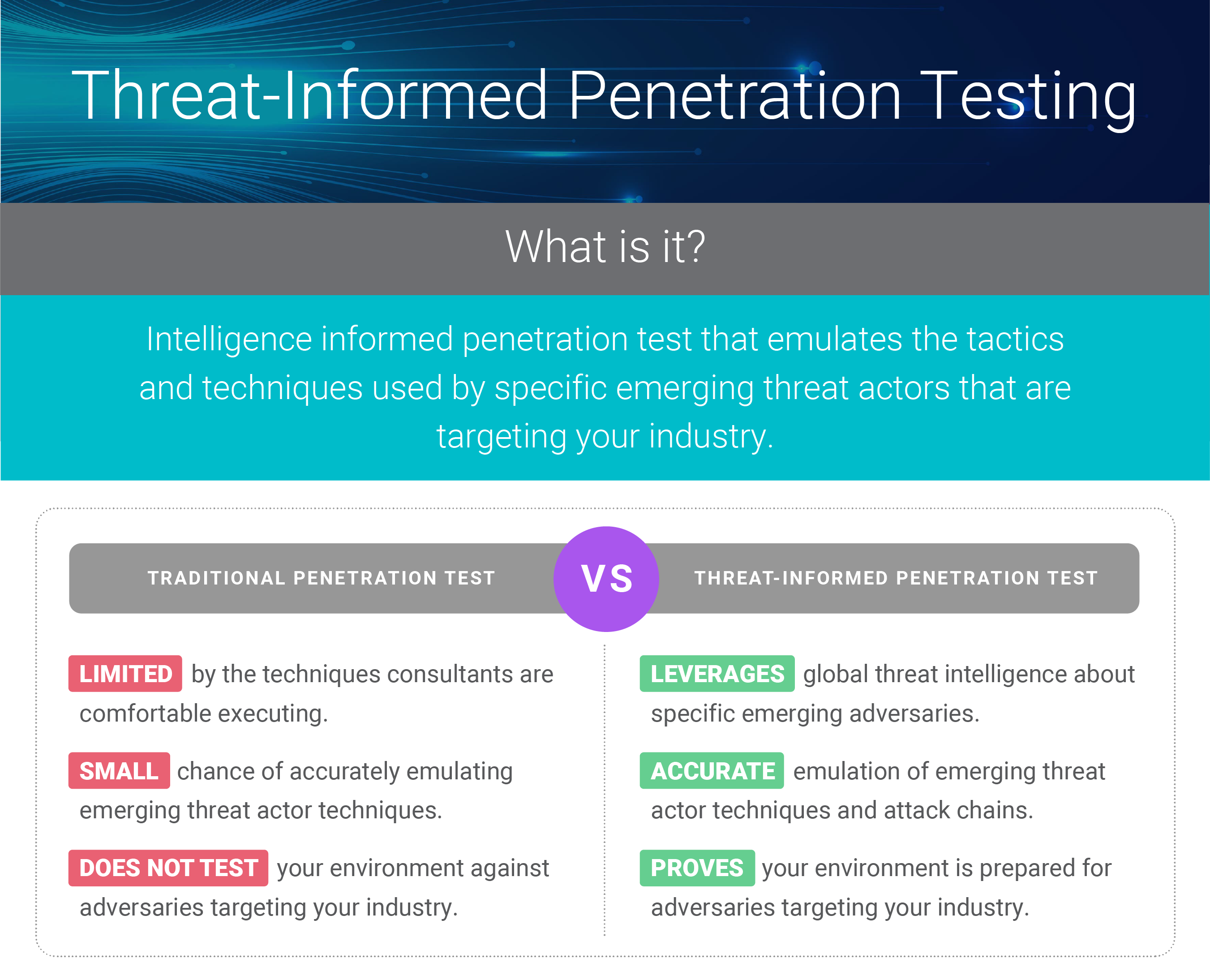
What is Threat- Informed Pentesting (TIP)?
TIP is Intelligence informed penetration test that emulates the tactics and techniques used by specific emerging threat actors that are targeting your industry,
giving you the opportunity to understand exactly how your controls would handle them.
Answering questions like, do you have some mitigation in place that prevents these actions from working? What detection do you have that would allow your team to identify this activity in place?
Why is this better than regular Pentesting?
In a “regular” Pentest the only attack actions executed tend to be the ones that the consulting firms pentester is comfortable using. Since the Pentest frequently starts from the same point (an internally placed dropbox), you never exercise the types of ingress used by real attackers – connect over the VPN using genuine credentials, exploit an externally positioned application, phish their way into a privileged user, etc – you miss testing these systems altogether. And because threat actors use different procedures and tooling, the testing provider by the Pentester firm may not have much in common with the real threat at all.
Is this a replacement for a regular Pentest?
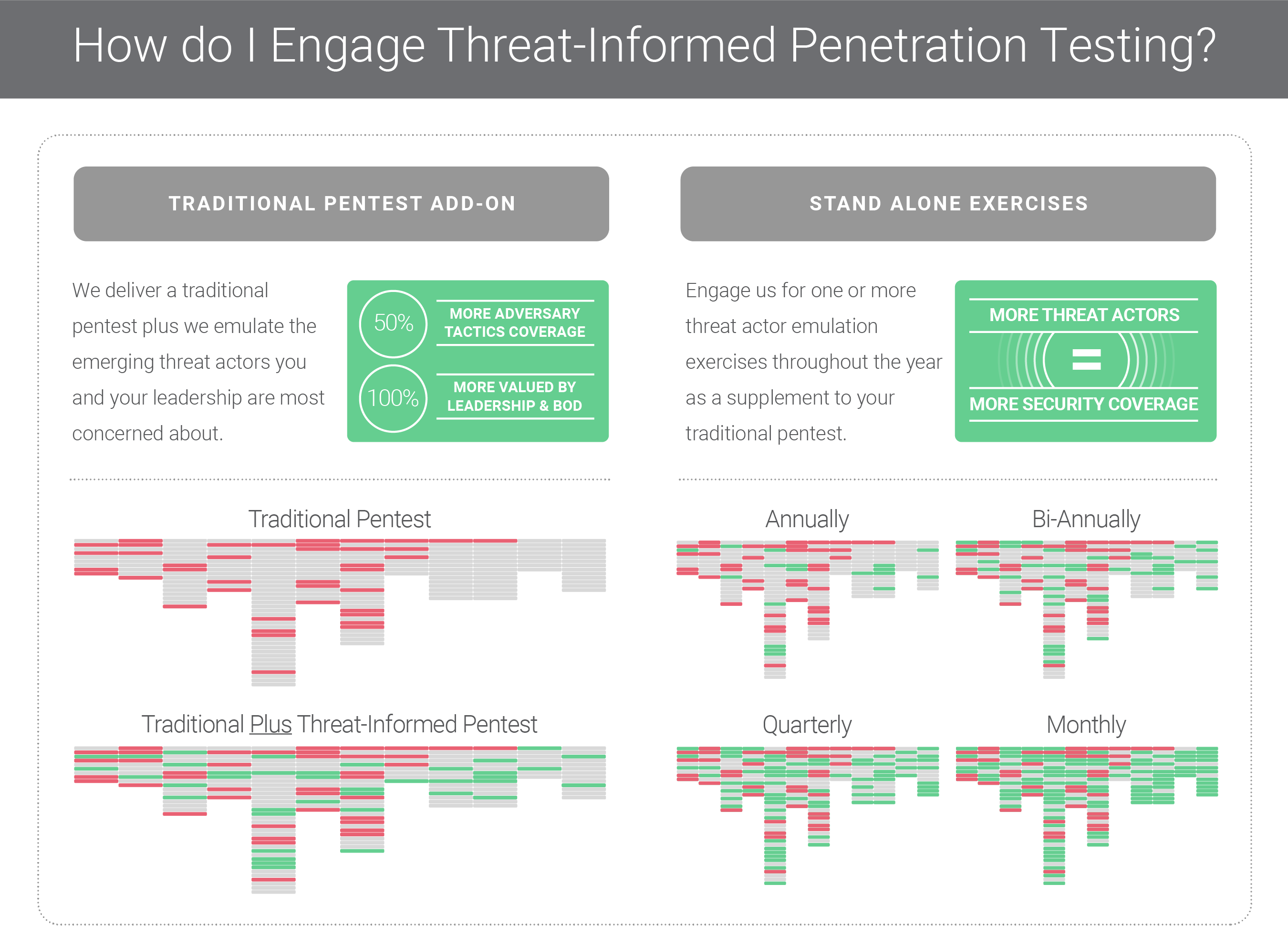
A single TIP is not a replacement for a full Pentest. First, the scope of the scenario is very narrow and targeted based on the adversary, so plenty of available attack actions are left out of a TIP. Second, because of the narrow scope, the TIP may not provide any feedback on the security posture of other systems, which in a traditional Pentest would be examine and probe them at a minimum. TIP can be conducted either as a stand-alone exercise as a supplement to your traditional Pentest or it can be offered as an add- on to your regularly conducted test.
How do we pick the “adversary”? How do we know which one is relevant to us?
Threat actors tend to blur industry lines a lot but selecting a TIP that simulates an adversary known for attacking other orgs in your vertical is a good start. It’s also good to have a variety of scenarios – access over VPN, exploiting web app vulnerability, supply chain attack, or spearphishing. Each scenario is intended to drive discussion among the team around whether security controls are deployed correctly and with the right configurations. For example, if faced with the reality that the adversary gained access over the VPN, do you have enough logging data to reconstruct what happened? Do you know how to try an IP address from the VPN tool to a specific user account for the time when the access occurred? Can you revoke access successfully and within your operational time targets? When all else fails, ask your BOD and leadership what adversary they are specifically worried about.
Why can’t we just do that without the scenario?
Many of these scenarios require different starting points than a traditional pentest – they also require some scaffolding put in place in cooperation with the customer to ensure the scenario can proceed (example: credentials with VPN access), which frequently are not given during standard Pentests. These scenarios don’t open up for consultants to move around with impunity – they are strictly timebound and focused on executing the different stages of the scenario.
This sounds like a Breach and Attack Simulation (BAS) tool or an Automated Pentest tool?
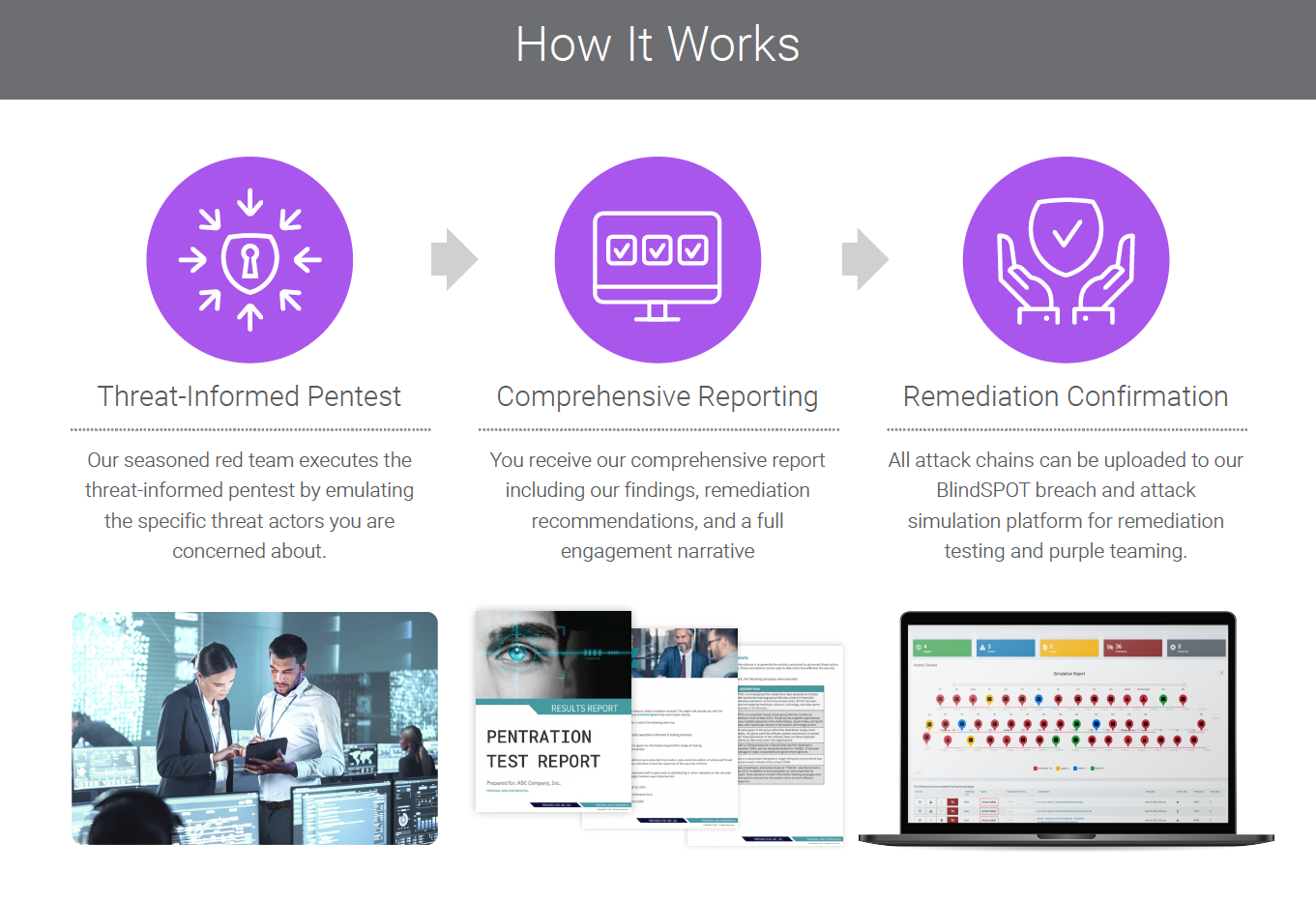
While using a BAS tool can provide valuable automation to repeatably test specific actions, TIP relies on the ability of a human being to execute a scenario while being able to adapt to the results they are seeing. BAS tools have limited ability to vary their procedures and payloads during execution time, which a talented and imaginative consultant can adjust on the fly during the operation. After the simulation is complete, we highly recommend retesting with BlindSPOT (OnDefend’s propietary Breach & Attack tool) to automatically retest and confirm successful remediation.
You mentioned something earlier about needing “scaffolding” for the scenarios – what does that mean?
TIP scenarios are designed to be very compact, which ensures you can try more than one and that they don’t require a huge commitment of resources. As part of compressing this timescale we build in some requirements and some stages.
Requirements are the specific items needed to begin the scenario. For example, if we execute a LAPSU$ scenario, we require credentials will access to the VPN (or other remote access technology). A LAPSU$ agent will pay an employee or contractor for their creds, something which we don’t have time to execute in the simulation window. But by starting with access, we can immediately begin executing the technical actions that you would see from the threat actor.
Stages are groups of actions in a TIP scenario. Let’s say that during the FIN7 scenario we have an initial opening stage of sending the first payload in through an email. If we are unable to get any attachment through the email security filtering, we will mark that stage as preventing success, but then move to the next stage, where the customer facilitator would place the payload on the intended system so that we can move to the next stage.
The goal is to work through ALL stages, and the report for the scenario will include the details around which stages were successful, and which were not. But without having the necessary resources to start and then continue, we cannot provide the full end-to-end experience of the activity executed by the threat actor.
What is your recommendation for someone looking into Threat- Informed Pentesting? Where should they start?
First – what threat are you most worried about? Or put another way, if you found out today that a breach occurred, what would your first instinct tell you is the likely way it happened? One of the great benefits of TIP is the validating assumptions you have – either good or bad. I would probably start with a scenario that is different from how you conduct your standard Pentest. If your regular Pentest starts with a focus on endpoint devices, maybe pick a scenario where the threat actor gets in through your VPN or what about simulating an exploit of one of your webservers that faces the Internet?
Once you have the scenario in mind, draw up the plan with where you expect your security tools to prevent or detect the threat actor. If you use the VPN access scenario, see how effectively you can track activity across systems. Can you carry identity through from the VPN connection itself to other network activity, or application activity? Do you have a complete picture of what that VPN client connection did while connected? Do you have a way of containing further activity from that VPN account?
It’s important that you play the scenario out all the way. Preventing some actions early in the TIP scenario is great, but it’s important to understand how your defenses would work afterwards. Don’t rely on that initial prevention as your only tested component, because as soon as the threat actor figures out a way around, you are going to want to know how your detective controls work too.
Ready to learn more? Don’t miss out on the opportunity to stay ahead of the competition. Join OnDefend CEO Chris Freedman and CTO Ben Finke live for Threat-Informed Pentest: Preparing for Threats Targeting Your Industry on Wednesday, May 10th at 1pm ET.
See you there!

Register Here:
The motto for this year: do more with less.
Amazon, Salesforce, and Meta laid off tens of thousands of people this past year citing an uncertain economy. It goes without saying if these mega giants are feeling the squeeze, everyone will. While cybersecurity seems as if it would be nonnegotiable, we’ve seen from experience no one is immune from these cuts.
Let’s recap where Cybersecurity is headed with some numbers. Cloudward reported for Ransomware attacks only:
- Cost the world 20 billion in 2021.
- Will cost upwards of $265 billion by 2031
- 37% of all businesses and organizations we’re hit by ransomware
- $1.85 million: the average amount it cost businesses to recover from a ransomware attack.
Those numbers are expected to be higher for 2022. Companies cannot afford a breach, but everyone has a bottom line. We’re only two weeks into the new year but let’s break down four quotes from industry leaders that paint a picture what to expect this year.
1. “Catastrophic cyberattacks may overwhelm the insurance industry in the future,” said Chief Executive of Zurich Insurance Group AG Mario Greco. … “there is a limit to the amount of damage that the private sector can cover and called on governments to set up public-private schemes to handle systemic cyber risks.” (Financial Times)
It’s not just companies that can’t afford to be breached; the insurance industry is nervous too. Cybersecurity insurance is a complicated issue. While it exists, it is usually very costly and requires a rigorous compliance standard for a policy to be issued. Should companies have to comply with a certain standard? Absolutely, but the framework for those standards is still being worked out. Take, for example, CMMC for government contractors. Those compliance standards don’t go into effect until May 2023, and that doesn’t include any private businesses. CNBC reported that costly data breaches, ransomware, and other security attacks are also behind an increased cyber insurance policy cost trend: the average premium increased by 28% in the first quarter of 2022 compared with the fourth quarter of 2021. Here’s what to take from this quote: government interaction, cybersecurity insurance, and compliance standards are going to be a hot topic this year for everyone.
2. “One of the biggest issues in data security that will continue to be an issue in 2023 has been the relentless sale and essentially open market for personal data from social media platforms,” said Art Shaikh, founder and CEO of Circleit and DigitalWill.com.
A hacker claims to have collected over 400 million unique users’ data with a now-fixed API vulnerability on Twitter. This is still an ongoing issue and only highlights the quote above. It is no secret that social media companies collect people’s information and sell it (to what extent we may never know). At the end of the day, it poses a risk for every single person that signs onto one of these platforms. (Source: Forb
(Source: Forbes, Wayne Rash)
What To Expect For Security And Privacy In 2023 (forbes.com)
3. “Producers and developers don’t have much incentive to reduce these vulnerabilities,” she said, because the “cost is on users” when there’s an attack. – Lorena Boix Alonso, the European Commission’s top cybersecurity official
While you may hope that companies who collect your most sensitive information won’t fire the people protecting it, that’s not the case. A business is a business and at the end of the day; everyone has a bottom line. Lay-offs aside, let’s say a company develops a widget for an app. That company needs to make money and waiting on IT to make sure all their ducks in a row isn’t always going to cut it. Producers and developers aren’t necessarily putting out a product that is vulnerably malicious on purpose, but it happens. When the product goes out and something goes wrong, whose personal information or money is on the line? The user. As budgets get tighter, we may be seeing a lot of that this year.
(Source: Tim Starks, Washington Post- RE: Luca Bertuzzi of Euractiv)
Europe’s cybersecurity dance card is full – The Washington Post
4. “Securing critical infrastructure like the energy and health care sectors plays a key part in mitigating cyber risks,” said Josephine Wolff, an associate professor of cybersecurity policy at the Tufts University Fletcher School of Law and Diplomacy.
Supply chain attacks like SolarWinds are the first thing that came to mind when reading this. Hackers are incredibly good at playing the long game to infiltrate a system like a hospital or energy source. With budget cuts this year, it’s going to make a vulnerable industry even more penetrable. For example, when the pandemic hit, hospitals were packed but filled ERs don’t necessarily equate to money back to the hospital. We know that, for some hospitals, meant freezing or cutting the budget on cybersecurity. For many, this means relying on an outdated and thin security system to fend off these skilled hackers. Whether it’s a federal step in or higher compliance standards, there needs to be a focus on these sectors or there will be a major issue.
(Source: The Hill, Ines Kagubare)
Four cyber concerns looming in the new year | The Hill
What should we take away from this? It’s going to be a busy year when it comes to cybersecurity. I know we say that every year, but that’s what happens when you are in an ever-evolving industry.
We invite you to learn more about our services and products on our website Ondefend.com. We look forward to helping our partners around the world secure our world.
About OnDefend
OnDefend helps companies prepare for and defend against real-world cyber adversaries by providing preventative information security services as well as its patented and proprietary cyber defense products BlindSPOT and Confirm4Me. By working with companies ranging from Fortune 500 corporations to regional businesses, OnDefend helps strengthen the private and public sectors security posture against continually evolving and persistent cyber adversaries throughout the US and around the world.