BlindSPOT Newsletter: The Inaugural Edition
The latest BlindSPOT updates, a breach and attack simulation solution.
Read
What a year this has been! If you’ve been with us throughout 2023 I hope you’ve been able to enjoy all of the new features, content, and improved performance of the BlindSPOT platform!
I’d like to thank everyone who has had a hand in helping us make BlindSPOT better – whether you gave us feedback during an exercise, sent in a suggestion, or shared some of the stories of your executions in the platform – thank you.
To the development team and the content team, I am honored to work with each of you every day, and I continue to be amazed at your creativity and determination to build something we are so proud of.
Alright, let’s get to some of the highlights of the last couple of months!
-Ben Finke
BlindSPOT has always provided a way for you to find, well, your blindspots, with our Attack Simulation capability. But once you get those tools tuned and alerts just the way you want, how can you make sure those tweaks remain ready? And arguably just as important, how do you know you are getting the right data into your pipeline for those alerts to fire? Enter Alert Validation!
We leverage the Attack Simulation capability within BlindSPOT to execute attack activity on endpoints in your environment, then connect to your security tools and find the alerts you expect to fire – and give you all the details about them:
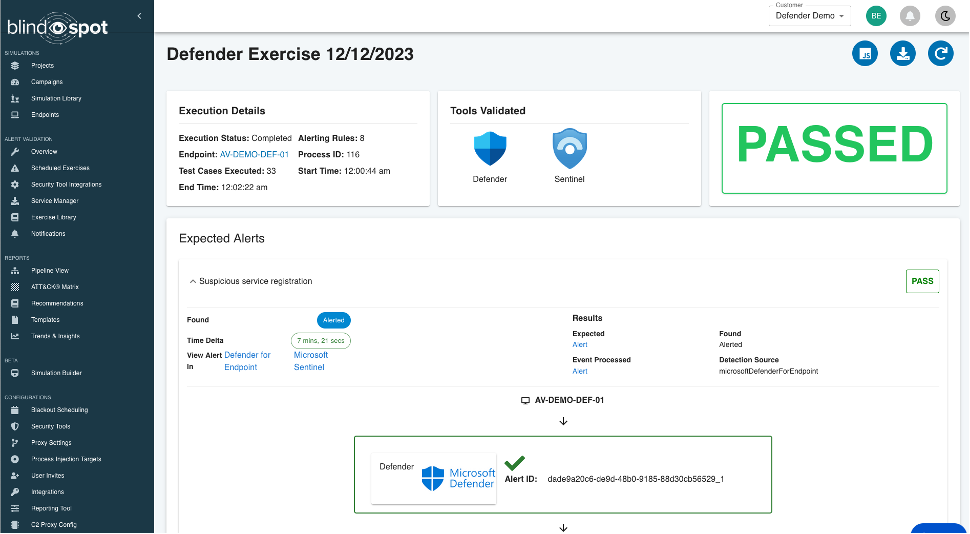
We’ll show you the exact alerts firing in your tools, and how long it took for them to fire (in this case, just over 7 minutes). If any alerts you were expecting don’t fire, we’ll let you know.
All this means you get proactive testing of your detection capabilities, end to end, fully automated and over time you get a Detection Uptime report!
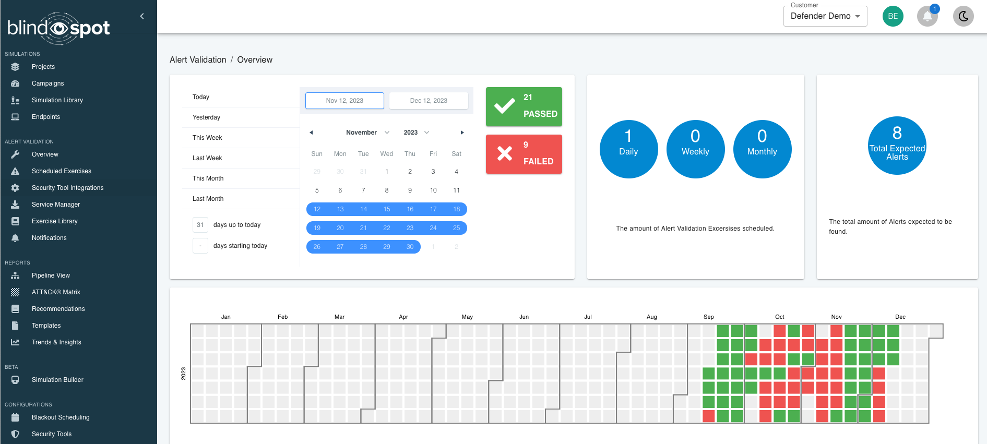
We’re starting with Microsoft Defender for Endpoint and Sentinel, and plan to expand those capabilities to include more tools in the very near future.
Already a BlindSPOT user and want to check out Alert Validation? Let us know if you’d like to try it out.
P.s. we’d love to know what tools you’d like for us to include in our next update!
In the last BlindSPOT newsletter, we told you about our newly redesigned simulation library that streamlines the process when you want to find a specific simulation you need.
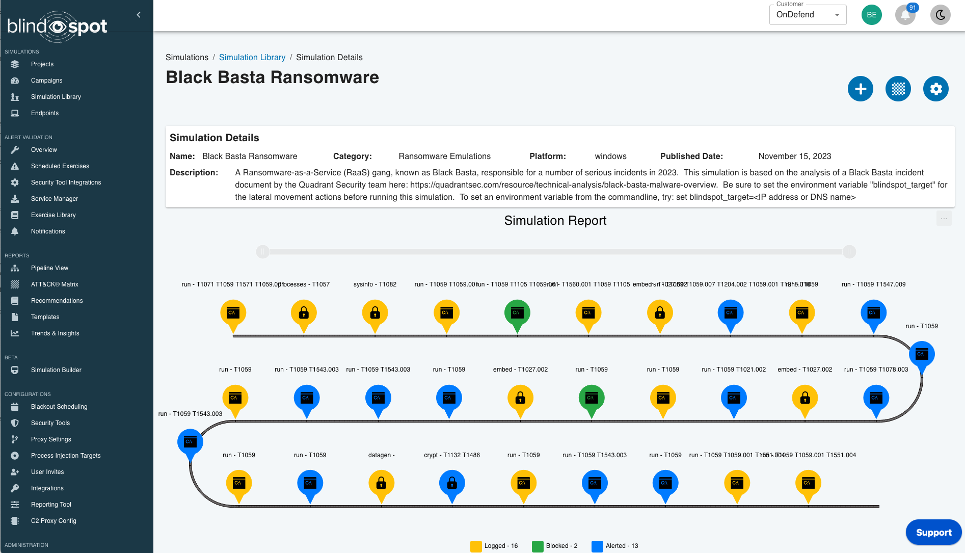
We continue to build out that simulation library and wanted to highlight a new release, the Black Basta Ransomware simulation.
Based on the excellent write-up by our friends at Quadrant Security this simulation includes lots of new tradecraft not seen in other ransomware intrusions, including, a chained LNK -> JS -> CMD -” regsvr32 executing a malicious DLL, all packed in an ISO image file.
Phew!
The standard BlindSPOT agent was designed to be easily placed on target systems, quick and flexible to execute, with simple cleanup (just delete the file!), but sometimes you may want a more persistent version of the agent, one that can always be ready to run a campaign, even surviving reboots. Enter our new BlindSPOT Service Manager:
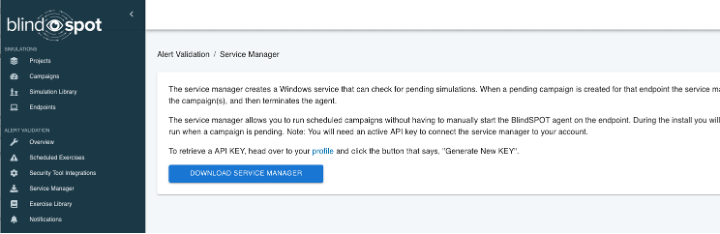
Download the Service Manager, grab an API key (oh yeah, did I mention our API is live too!), and run the downloaded MSI. You’ll see a new app on the machine, the BlindSPOT Service Manager. Enter your API key, and now you can install the service, specifying the specific BlindSPOT agent you want to use to run any campaigns you assign to that endpoint:
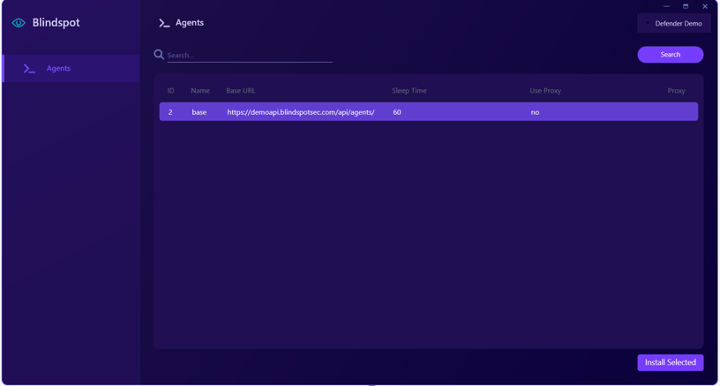
Pick the agent you want, click on “Install Selected” and you’re ready to install your BlindSPOT agent service:
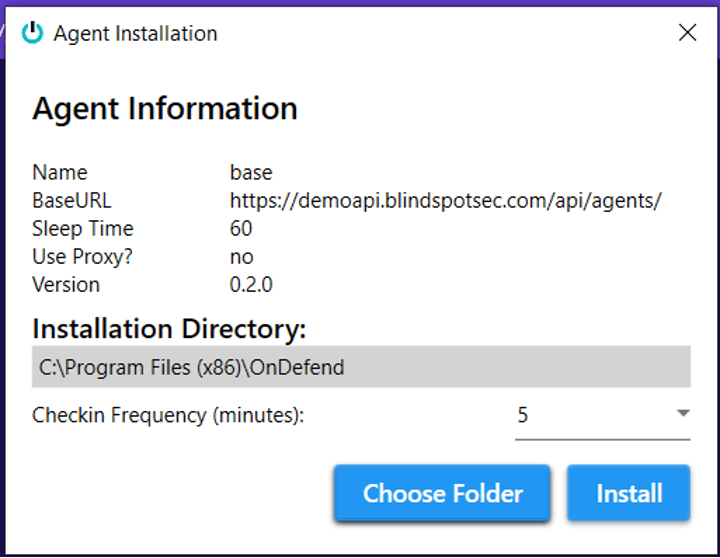
The service will check in with BlindSPOT, and when it sees you’ve got a campaign ready to run it will download and/or start the agent, execute the campaign, and then put the agent back to sleep until the next one. Works great for running Attack Simulations, and pairs nicely with the Alert Validation feature too!
BlindSPOT Satellite: We’re building an integrated utility that you can use to test data exfiltration techniques, execute different Command and Control traffic patterns (C2), and source downloads to execute tool ingress techniques. You’ll be able to use our satellites, or deploy your own on your own custom systems, using any domain you want.
Attack Simulation Autoscoring: Building on the success of our Alert Validation feature, we’ll soon have fully automated autoscoring for Attack Simulation campaigns too. (I know many we are all excited for this one.)
One last thing…
BlindSPOT was always a dream of ours and seeing it run successfully in organizations around the world is the best present we could ever ask for. From the bottom of our hearts, We want to thank you for joining this BlindSPOT journey and am looking forward to the new year. Happy Holidays everyone!

If you want to stay in the loop about what’s happening at OnDefend & BlindSPOT, including our upcoming webinars, the latest cybersecurity trends, and product updates, then follow us on Facebook, Twitter, and LinkedIn @ondefend.