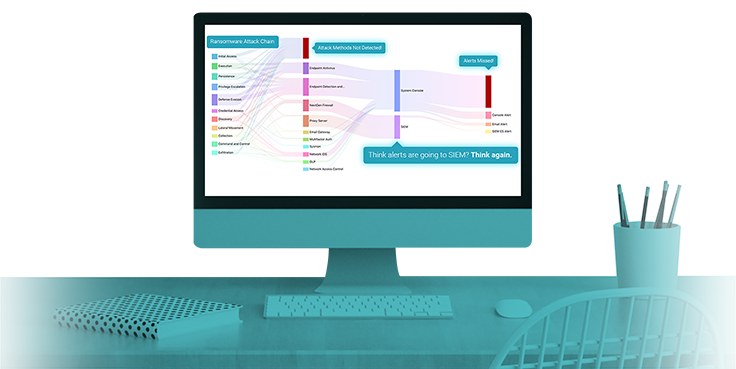
Security providers who deliver new and cutting-edge solutions to solve their clients’ problems are winning the hearts and minds of their customers and the battle for marketshare.
Cybersecurity Consulting Service Pains
Finding Qualified Employees is DOWN
Qualified Employee Costs are UP
Service Rates are Becoming COMMODITIZED
Is This You?
PAIN
1
I can’t find qualified talent to meet market demand.
$28.2
BILLION
How Much the Cybersecurity Consulting Market is to Surpass by 2031.
50%
of Businesses Surveyed Say Their Cybersecurity Applicants are Not Qualified.
PAIN
2
I am having to delay or turn down customer projects.
70%
of Customers Seek a Competitor When Needs are Not Met.
PAIN
3
I am concerned about the profitability of certain services.
16.3%
Increase in Cost of Qualified Pentest Employees Since 2019.
PAIN
4
I would rather my staff focus on other growth offerings.
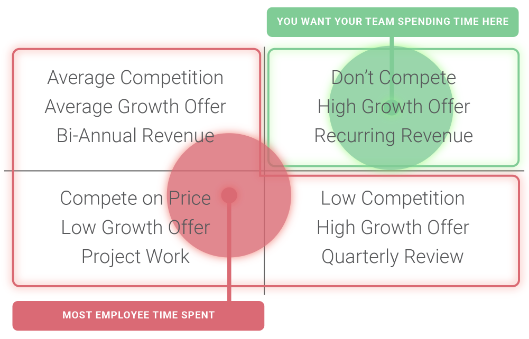
PAIN
5
How can I differentiate from my competitors?
Consulting firms, MSSPs, and MSPs throughout the U.S. are offering similar security services and solutions.
How a Private Label Service Partner Can Provide Relief
PAIN 1
SOLUTION
Access qualified professionals on-demand to meet market demand.
PAIN 2
SOLUTION
No more saying “No.” Meet your customers’ needs on their timeline and within their budget.
PAIN 3
SOLUTION
Remove your risk by setting your service margins and removing fixed expenses.
PAIN 4
SOLUTION
Subcontract services that are not optimally profitable and aligned to your growth strategy.
PAIN 5
SOLUTION
Add services from purple teaming to managed breach and attack simulations.
Want to learn how we can do this for you?
Submit Your Information Below:

SMART. STRONG. RELIABLE.
Supercharge Your Business.
Contact us today to expand your security offering, meet market demand, and secure our world.
Contact Us